
Apache Log4j2 Remote Code Execution Security Vulnerability (CVE-2021-44228)
Recently, researchers discovered that the Apache Log4j2 Java module has a remote code execution high-risk vulnerability (CVE-2021-44228). Because this module is universally used in middleware, development frameworks, and web applications, this vulnerability is considered as highly destructive.
What is Apache Log4j2?
Apache is an open-source web server platform developed by "The Apache Software Foundation", powering at least 1/4 of all global web servers (according to Netcraft.com). Apache Log4j2 is a Java logging framework and an upgraded version of Log4j. It can control the output format of each log and make the log generation process more detailed by defining the level of each log. It is widely integrated in various servers and components because of its ease of use.
Sangfor Team also prepared a video and another blog article for easy understanding on Apache Log4j vulnerability and its possible impact on your organization. We have interviewed Jason Yuan, VP – Product & Marketing, Sangfor Technologies. We have also provided some emergency guidelines and usage of Sangfor products such as NDR - Network Detection and Response for immediate mitigation.
Apache Log4j2 Analysis
CVE-2021-44228 is a remote code execution (RCE) vulnerability in Apache Log4j2. Unauthenticated, remote attackers can exploit this vulnerability by sending specially crafted web requests to a server using Apache Log4j2 that has the vulnerability. The crafted requests inject code using the Java Naming and Directory Interface (JNDI) via a variety of services including:
- Lightweight Directory Access Protocol (LDAP)
- Secure LDAP (LDAPS)
- Remote Method Invocation (RMI)
- Domain Name Service (DNS)
If the vulnerable server uses Log4j2 to log requests, the exploit will request a malicious payload using JNDI via one of the services listed above from a command-and-control server. Successful exploitation could lead to RCE.
On December 9, researchers published proof-of-concept (PoC) exploit code for vulnerability CVE-2021-44228. The Sangfor Neural-X cloud-based intelligence and AI analytic platform recorded an explosive increase in the number of exploit attacks against the vulnerability. At the same time, H2Miner, Mirai, Muhstik, Z0Miner and other hacker organizations showed they have integrated this exploit into their own arsenals. Sangfor FarSight Labs expects the number of attacks using this vulnerability will continue to increase in the future.
A Minecraft client or private server can be exploited through its chat function.
It has been reported that vulnerability exploits have embedded cryptominers on systems.
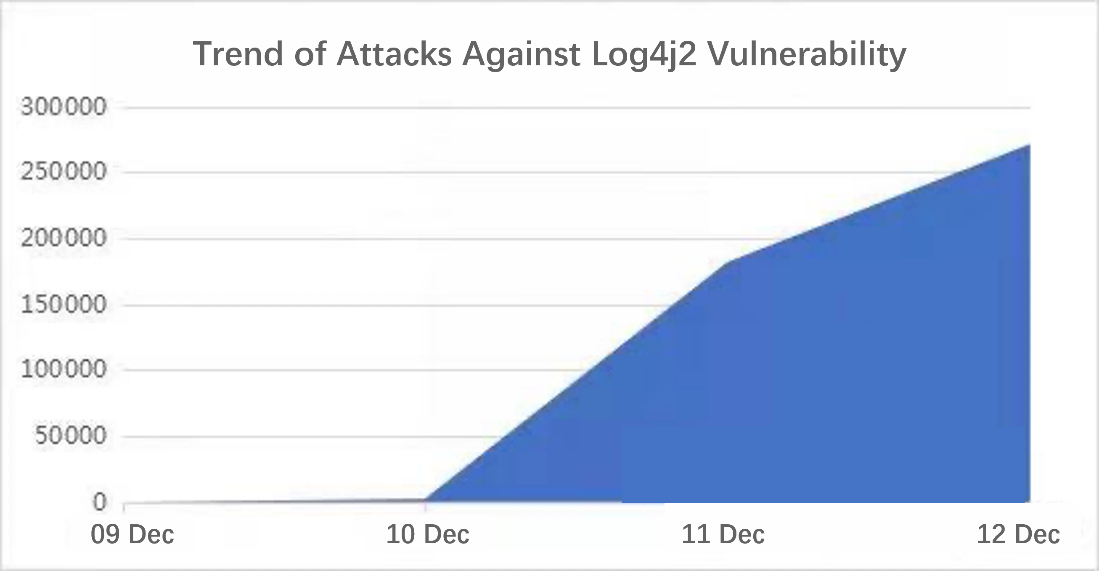
The following is recent attack trend data captured by Sangfor Neural-X:
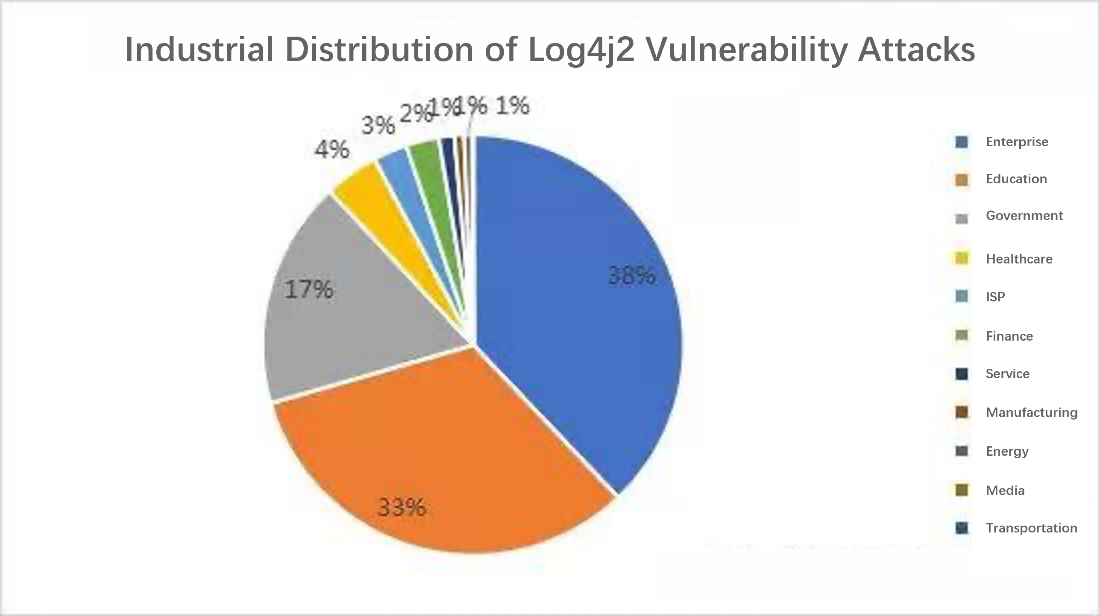
Industries such as education, government, and manufacturing are most vulnerable to exploit attack. The distribution of attacked industries seen is show in the graph.
Sangfor Emergency Response Guidelines
Apache released version 2.15.0 on December 10 to fix the vulnerability. However, Log4j2 2.15.0 requires Java 8. Any organization that uses Java 7 needs to upgrade to Java 8 before installing the updated version of Log4j2.
Sangfor recommends the following emergency response guidelines to help you quickly conduct risk analysis and emergency reinforcement of your network security if you cannot patch Log4j2 immediately:
Q1: How to complete a risk self-assessment?
- Assent management is critical to identify and categorize the business risk of potential target servers. Sangfor Endpoint Secure can assist users who have a great number of host, system, and application assets that need categorization. Users can quickly sort host assets (operating system, middleware, application software) using the Endpoint Secure Asset Management capabilities without requiring updates to software versions. Endpoint Secure can quickly locate and identify high-risk versions of Apache Log4j2, evaluate high-risk middleware and applications, and assess the population of affected servers.
- Sangfor Cyber Command network detection and response (NDR) platform updates vulnerability threat detection models using Neural-X data as soon as a vulnerability is discovered and reported. Cyber Command can accurately locate any affected assets and evaluate their repair priority, quickly converge on the exposed attack surface, and directly trace back the exploits that have occurred.
Q2: How to implement emergency reinforcement?
- Apache Log4j2 version 2.5.10 can be found here.
- For Cyber Command, NGAF, and Endpoint Secure users, Sangfor has quickly provided an update for the corresponding protection rules in its security database, and confirmed that the rules have been activated in the protection policy. For more information on reinforcement, please contact your Sangfor local office.
- For users who have the Sangfor NGAF WAF module, it is recommended that Bot Protection be enabled to run vulnerability scanning and information detection on web requests, and to hide the original directory structure and code files of the website.
- For organizations who do not have Sangfor products yet, Sangfor provides Incident Response and Assessment services to help organizations build full visibility of their entire network and quickly determine the risk of attack or if now suffering attacks exploiting the Apache Log4j2 vulnerability.
Watch a video on easy understanding about Apache Log4j security vulnerability and how you can immediately mitigate the risk.
Click here for a consultation with a Sangfor security expert to help you protect your network from attacks exploiting CVE-2021-44228. You can contact us for Incident Response services. Visit us at www.sangfor.com to learn more about our security solutions & services.





