Athena NDR captures full network traffic and security logs across all network segments—both north-south and east-west—and analyzes this data using AI, behavior analytics, threat intelligence, and more. By establishing baselines of normal activity, Athena NDR identifies anomalies that signal sophisticated threats such as advanced persistent threats (APTs), ransomware, lateral movement, and insider threats—often missed by isolated security tools. This enables real-time, context-rich threat detection across the entire environment.
Intelligent Threat Detection and Response Platform
Sangfor Athena NDR (previously known as Sangfor Cyber Command) provides real-time visibility into network traffic. With AI-driven behavioral analytics, it detects what others miss—lateral movement, advanced attacks, and insider threats that evade traditional tools. Detailed event insights and automated responses empower your team to handle complex threats with speed and confidence.
Beyond its core NDR capabilities, Athena NDR integrates with firewall and endpoint security solutions, enabling unified visibility and automated response capabilities typical of full-scale SOCs.
How Athena NDR Works at a Glance
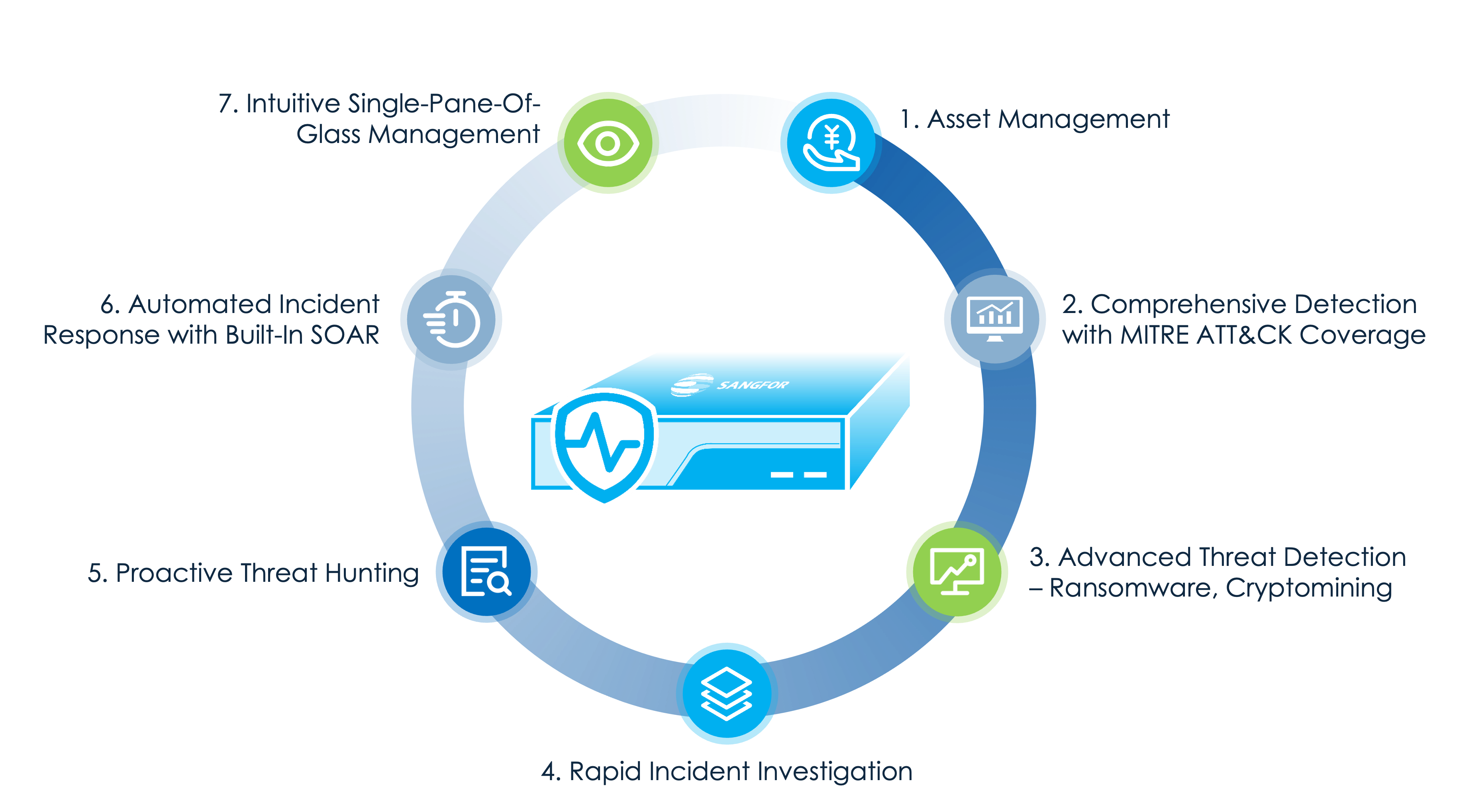
Athena NDR Key Features and Capabilities
Advanced AI-driven Threat Detection
Rapid Cyber Forensic Investigation
Athena NDR streamlines forensic investigation by merging related security events and highlighting affected assets. By collecting IOCs and BIOCs, it enables deep, post-incident analysis, helping analysts quickly uncover root causes, validate threats, and export findings for reporting.
Threat Hunting & Attack Chain Visualization
The Golden Eye engine enables proactive threat hunting by analyzing compromised asset behavior and reconstructing the entire attack chain. This deep visibility into attacker tactics and techniques enables high-confidence investigations and rapid root cause identification.
Automated Incident Response (SOAR)
A built-in SOAR module accelerates threat containment using predefined and customizable playbooks. It integrates with Athena EPP, Athena NGFW, and third-party tools to automate actions like host isolation and domain blocking, reducing response time and analyst workload.
Centralized Threat Management
Athena NDR aggregates logs and alerts from integrated security tools to provide a unified view of assets, threats, vulnerabilities, and more. This centralized approach allows teams to monitor security posture in real time, spot risks faster, and take proactive actions—all within a few clicks.
Advanced AI-driven Threat Detection
Athena NDR captures full network traffic and security logs across all network segments—both north-south and east-west—and analyzes this data using AI, behavior analytics, threat intelligence, and more. By establishing baselines of normal activity, Athena NDR identifies anomalies that signal sophisticated threats such as advanced persistent threats (APTs), ransomware, lateral movement, and insider threats—often missed by isolated security tools. This enables real-time, context-rich threat detection across the entire environment.
Rapid Cyber Forensic Investigation
Athena NDR streamlines forensic investigation by merging related security events and highlighting affected assets. By collecting IOCs and BIOCs, it enables deep, post-incident analysis, helping analysts quickly uncover root causes, validate threats, and export findings for reporting.
Threat Hunting & Attack Chain Visualization
The Golden Eye engine enables proactive threat hunting by analyzing compromised asset behavior and reconstructing the entire attack chain. This deep visibility into attacker tactics and techniques enables high-confidence investigations and rapid root cause identification.
Automated Incident Response (SOAR)
A built-in SOAR module accelerates threat containment using predefined and customizable playbooks. It integrates with Athena EPP, Athena NGFW, and third-party tools to automate actions like host isolation and domain blocking, reducing response time and analyst workload.
Centralized Threat Management
Athena NDR aggregates logs and alerts from integrated security tools to provide a unified view of assets, threats, vulnerabilities, and more. This centralized approach allows teams to monitor security posture in real time, spot risks faster, and take proactive actions—all within a few clicks.
Athena NDR Walkthrough VideoExperience how Athena NDR delivers real-time threat detection, investigation, and response in a single, lightweight platform. This walkthrough video takes you through its powerful features and shows how it simplifies security operations without compromising performance. |
Athena NDR Use Cases


Stop Lateral Movement Before It Spreads
Stop Lateral Movement Before It Spreads
A government agency identified suspicious network communications between departments. Athena NDR traced the source to a compromised asset and stopped lateral propagation.


Accelerate Incident Investigation
Accelerate Incident Investigation
A telco struggled to investigate alerts quickly due to the lack of resources. With Athena NDR, they could trace the full attack chain, cutting investigation time from hours to minutes.


Automate Response during Non-business Hours
Automate Response during Non-business Hours
A manufacturer struggled to respond to alerts during evenings and weekends. Athena NDR was deployed to execute automated response actions without human intervention.


Detect Insider Threats
Detect Insider Threats
A financial firm noticed a spike in internal file activity. Athena NDR flagged abnormal access patterns on a shared drive, revealing a user collecting sensitive data to prevent a data breach.
Athena NDR Competitive Advantages
Athena NDR combines signature-based detection, threat intelligence, and AI analytics under one license. Together, these enable the detection of known, emerging, and unknown threats, while some competing NDR solutions require separate add-ons for full coverage.
Unlike other NDR platforms, Athena NDR includes built-in threat hunting with Golden Eye and native SOAR capabilities—no external tools or add-ons required. This eliminates compatibility issues, reduces complexity, and cuts costs.
Athena NDR offers Sangfor Security GPT’s detection model—Detection GPT—as an add-on. Detection GPT leverages GenAI capabilities to enhance the detection of zero-day and unknown threats. Most NDR vendors do not offer GenAI options for their products.
Athena NDR integrates with Sangfor EPP, NGFW, and third-party tools to aggregate alerts for unified visibility and management. Combined with built-in SOAR, it delivers lightweight SOC functionality, whereas many NDR products focus on standalone traffic analysis.
Athena NDR Business Benefits

Minimize Business Risk
Athena NDR identifies sophisticated threats like APTs and ransomware in real time, detecting 95% within five minutes. Early detection helps prevent breaches that lead to data loss, regulatory penalties, and operational outages, ultimately protecting your bottom line and brand reputation.

Affordable, Enterprise-Grade SecOps
Athena NDR offers similar capabilities of a full-scale SOC—unified network visibility and threat management, advanced analytics, and automated workflows—at a fraction of the cost of third-party XDR and SIEM solutions.

Fast Time to Value (TTV)
Athena NDR integrates quickly with your existing security stack, such as EDR and firewall, without disrupting operations. Pre-configured detection policies and built-in automation mean you start detecting threats within hours, not weeks.

Boost Security Team Efficiency
Athena NDR automates threat investigation and response, enabling small security teams to handle complex threats without the time and skill demands of traditional manual analysis. This streamlined approach frees up valuable time to focus on real threats and strategic security initiatives.
Athena NDR Market Recognition



Customer Success with Sangfor: EBM Enhances IT Infrastructure and Support





Athena NDR Frequently Asked Questions
Athena XDR and Athena NDR are both designed to enhance threat detection and response, but they serve distinct roles within a security operations framework, with differences in scope, data handling, and automation capabilities.
1. Data Coverage and Threat Detection Approach
Athena XDR performs threat detection by ingesting data from a wide range of sources—including endpoints, firewalls, cloud platforms, and more. It performs deep correlation and contextual analysis across these inputs, enabling the identification of complex, multi-stage attacks.
Athena NDR focuses specifically on network traffic analysis for detecting threats based on behavioral patterns and anomalies. While it can aggregate logs and alerts from other tools (e.g., firewalls, endpoints), it does not correlate this data. Instead, it provides centralized visibility and threat management for network-based incidents, allowing security teams to monitor and manage the alerts of multiple tools in a single interface. This, combined with other capabilities outlined below, is what makes Athena NDR an effective lightweight SOC solution.
2. Automated Response (SOAR Capabilities)
Both Athena XDR and NDR include a built-in SOAR module, enabling automated incident response based on alerts from integrated tools. This allows for consistent and timely responses without manual intervention.
3. Security Operations Tools
Athena XDR includes a wider suite of tools for end-to-end security operations—including asset management, vulnerability management, ticketing systems, and reporting dashboards. This positions it as a unified platform for managing the entire security lifecycle.
Athena NDR provides basic asset and vulnerability management, but lacks the breadth and depth of operational tools found in XDR.
4. AI and GPT Integration
Athena XDR leverages the full capabilities of Sangfor Security GPT, including models like Detection GPT, Operation GPT, and Anti-Phishing GPT, enabling advanced AI-driven insights and automation.
Athena NDR, by contrast, supports only Detection GPT as an optional add-on, limiting its AI-enhanced capabilities to threat detection within the network domain.
Yes, Athena NDR supports integration with a broad range of third-party products from mainstream cybersecurity vendors, such as CrowdStrike Falcon EDR, Palo Alto and FortiGate firewalls, Macmon NAC, and more. It also supports sending real-time notifications via instant messaging applications, helping organizations establish security operations workflows and improve efficiency.
While SIEMs focus on collecting and correlating large volumes of logs, they face common challenges: static detection rules, high hardware demands, and limited operational effectiveness. Athena NDR addresses these gaps with real-time traffic inspection and behavior analytics, detecting threats that SIEMs often miss, such as APTs and lateral movement, without requiring complex rule maintenance or expensive infrastructure.
Yes, Athena NDR supports sharing data to SIEM platforms via RESTful API and Syslog (CEF, LEEF).
Athena STA (Stealth Threat Analytics) is a network sensor that mirrors raw traffic from the core switch. It uses Network Traffic Analysis (NTA) to pre-analyze and filter the data before sending the results to Athena NDR for more advanced analysis. Athena STA is a compulsory component of Athena NDR.
No, Athena STA transmits traffic analysis data to Athena NDR in real time; scheduled transmission is not supported.
Yes, Athena NDR supports email notifications via SMTP, POP3, and IMAP protocols. Note that ESMTP (e.g., Microsoft Exchange) and Webmail are not supported.







