Definition of Pharming
Pharming is a cyberattack technique where users are redirected from legitimate websites to fraudulent ones without their knowledge. Phishing usually tricks users into clicking harmful links. In contrast, pharming changes to network or server settings.
This automatically sends users to fraudulent sites. These sites often aim to collect sensitive information, like passwords or banking details.
Pharming Techniques
To fully grasp the threat posed by pharming, it’s essential to explore the various techniques employed by cybercriminals. Here are the most common methods used to execute pharming attacks.
- DNS Poisoning (DNS Spoofing): Attackers manipulate DNS servers to redirect internet users attempting to access a legitimate web address to a malicious one. This makes it hard for users to detect that they’re not on the correct website.
- Hosts File Modification: Attackers can change the local host’s file on a user’s computer. This allows them to send specific URLs to fake websites. This method is often easier to execute if malware is installed on the target device.
- Malware-Based Pharming: Some pharming attacks involve deploying malware that can automatically redirect users or modify DNS settings without their knowledge.
- Rogue DNS Servers: Malicious actors can create fake DNS servers that look quite realistic. These servers then can send users to phishing pages instead of legitimate sites.
Pharming vs Phishing
While both pharming and phishing are forms of cyberattacks, they differ significantly in execution and impact. Comparing these two methods highlights their unique characteristics and dangers.
|
Aspect |
Pharming |
Phishing |
|---|---|---|
|
Method |
DNS manipulation |
|
|
Definition |
Redirects users from legitimate sites to fake ones |
Tricks users into revealing information via fake messages or emails |
|
Target |
Domain Name System (DNS) |
User's trust and vigilance |
|
User Action |
Unintentional redirection |
Clicking malicious links or downloading attachments |
|
User Awareness |
Harder to detect; users may see the correct URL |
Users can recognize fake links with caution |
|
Impact |
Exposure to malware, identity theft, financial loss |
Data breaches, financial loss, identity theft |
|
Prevention |
Strong security practices, DNS protection, user awareness |
Strong passwords, email filters, user education |
Types of Pharming Attacks
Pharming attacks can be categorized based on their execution methods. The primary types include DNS-based and host-based.
DNS-Based Pharming
DNS-based pharming is when someone changes the Domain Name System (DNS) settings. This tricks a user into visiting a fake website instead of a real one. Attackers usually change the DNS settings on a user's computer or a DNS server. They can make a real domain, like bank.com, point to a wrong IP address.
This wrong address leads to a harmful website. This type can be dangerous. Users might not notice they are on a deceptive site. This is especially true if the fraudulent site looks quite like the real one.
How it Works:
- DNS Cache Poisoning: Attackers change the DNS cache on a user's computer. They alter the records of real sites to direct them to fake IP addresses.
- DNS Server Compromise: If attackers take control of a DNS server, they can change the IP addresses for some websites.
Host-Based Pharming
Host-based pharming focuses on altering the hosts file of an individual computer. This file maps domain names to IP addresses and is used to direct traffic to a particular website. In host-based pharming, attackers modify the host's file. This change redirects certain domains, like a bank's website, to an IP address they control.
Host-based pharming is different from DNS-based pharming. While DNS-based targets DNS servers or local caches, host-based happens only on the affected device. However, it can still cause significant harm.
How it Works:
- Hosts File Change: Attackers get into a user's computer and change the hosts' file. This redirects a real website to a harmful one.
- No DNS Server Involvement: This attack avoids changing DNS records. It directly alters how websites are resolved on the local device.
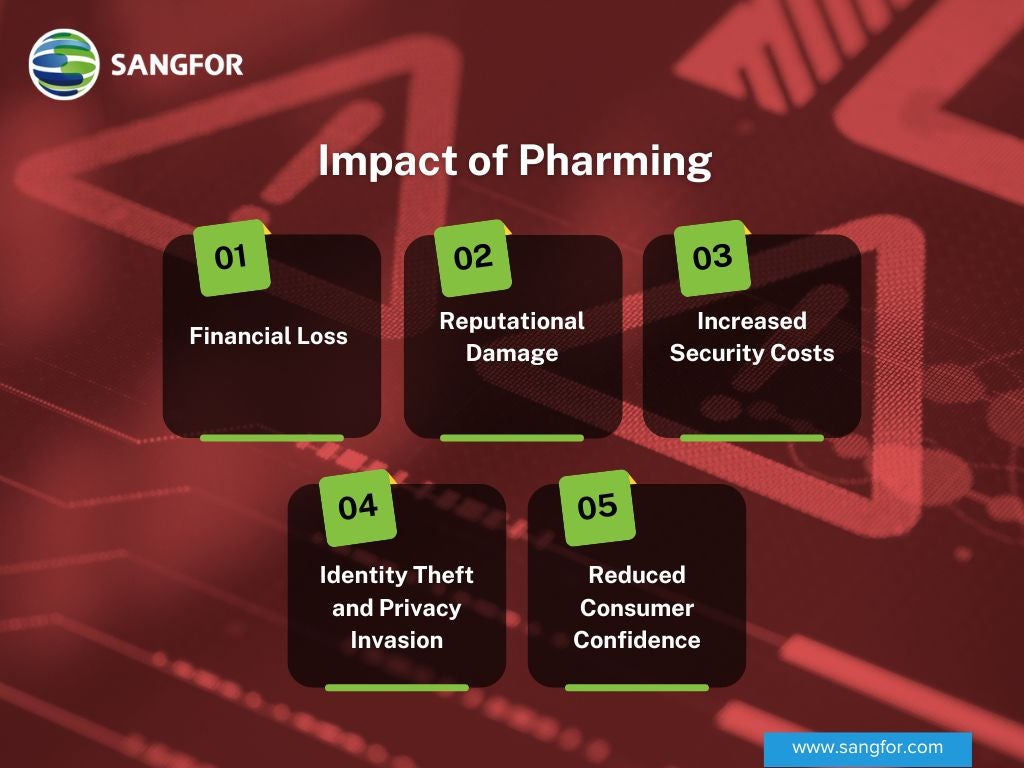
Impact of Pharming
The consequences of pharming attacks can be severe, affecting both individuals and organizations. Examining the various impacts of pharming, from financial losses to compromised personal information, underscores the importance of vigilance.
- Financial Loss: In 2007, a large pharming attack targeted customers of major banks in Brazil. Cyber criminals send users from real bank sites to fake ones. This put personal and banking information at risk and as a result, many people lost a lot of money.
- Reputational Damage: Pharming can harm the reputation of affected companies, as it makes their customers vulnerable. For instance, attacks on trusted websites (like banks) reduce user trust in the brand.
- Increased Security Costs: Companies spend heavily on cyber security tools to detect and prevent pharming. For example, after several DNS pharming attacks, some banks have invested in better anti-pharming tools and employee training.
- Identity Theft and Privacy Invasion: In 2014, pharming scams hit healthcare providers. They tricked employees into deceptive login portals. Attackers stole credentials and accessed sensitive patient data. This led to identity theft.
- Reduced Consumer Confidence: Many pharming attacks have made people more careful about online transactions. This change impacts industries that depend on online services and financial transactions.
Prevention and Protection of Pharming
Preventing and protecting against pharming requires a multi-faceted approach. Strategies and best practices for both individuals and organizations can significantly reduce the risk of pharming attacks.
Individual Precautions
- Digital Hygiene: Regularly update operating systems and software to address security vulnerabilities. Employ strong, unique passwords for each online account, and avoid reusing passwords across multiple platforms. Be wary of unwanted emails, links, and attachments, as they often serve as entry points for phishing attacks.
- Robust Security Software: Utilize reputable antivirus and anti-malware software to safeguard devices from malicious threats.
- Multi-Factor Authentication: Enhance account security by enabling two-factor authentication, adding an extra layer of protection beyond passwords.
- Network Vigilance: Exercise caution when using public Wi-Fi networks, as they are often less secure. Consider using a VPN to encrypt internet traffic and protect privacy.
- Stay Informed: Keep up with the latest cyber security trends and best practices. This will help you make smart choices and stay ahead of new threats.
Organizational Safeguards
- Fortified DNS Infrastructure: Implement robust security measures for DNS servers, including firewalls, intrusion detection systems, and regular security audits.
- Network Monitoring: Employ network monitoring tools to detect and block malicious traffic before it can compromise systems.
- Employee Awareness: Conduct regular cyber security training to educate employees about phishing tactics and other social engineering techniques.
- Comprehensive Security Policies: Establish stringent security policies and procedures, encompassing password policies, access controls, and incident response plans.
- Web Application Firewalls (WAFs): Deploy WAFs to protect web applications from a range of attacks, including pharming.
- Regular Security Audits: Conduct periodic security audits to identify and address vulnerabilities within the network and systems.
Conclusion
Pharming is a complex and often hidden cyber threat. It can cause serious problems like financial loss, identity theft, and damage to your reputation. By redirecting users to fraudulent websites through DNS manipulation, malware, or hosts file alterations, pharming exploits both technical vulnerabilities and human trust.
Effective prevention measures, including robust DNS security, antivirus software, multi-factor authentication, and continuous employee training, are crucial in safeguarding individuals and organizations. As cyber threats keep changing, staying alert and aware is important. This helps reduce the risks from pharming attacks.
Frequently Asked Questions
Pharming is a type of attack in which bad actors send users from real websites to fake sites. They often do this by altering DNS (Domain Name System) settings. This allows attackers to steal sensitive information, like login credentials or financial data.
Pharming usually involves changing a user’s device settings (local pharming) or altering DNS records. This can redirect traffic or users to fake malicious websites.
Both phishing and pharming aim to steal information. Phishing tricks users with fraudulent messages or emails. In contrast, pharming redirects traffic at the system level, making it harder for users to notice the attack.





