In the race towards digital transformation, many companies have upgraded their IT infrastructure to keep up with the times. Unfortunately, the cyber threats that we face have drastically evolved as well and are becoming increasingly difficult to combat. Threat actors are looking for new and innovative ways to invade networks and steal private data. It’s estimated that the total cost of cybercrime is set to reach US$ 10.5 trillion annually by 2025. This is why cyber security monitoring is essential for any organization looking to survive. This is especially needed when it is estimated the total cost of cybercrime is set to reach US$ 10.5 trillion annually by 2025.
In this blog article, we look at what cyber security monitoring is, how it works, and why it plays such a critical role in protecting networks. We also explore the many benefits of cyber security continuous monitoring and navigate the different cyber security monitoring tools available. However, before we get into the finer details, let’s understand the definition of cyber security monitoring.
What Is Cyber Security Monitoring?
Cyber security monitoring can be described as an automated process that helps organizations identify cyber threats. This is done through the rigid and continuous observation of network traffic, endpoint behavior, servers, logs, and more. Once any suspicious activity is detected, the cyber security monitoring tools will send an alert to the IT team and instigate an immediate response. This ensures that cyber-attacks are nipped in the bud and mitigated before any damage can be done. Now, let’s try to figure out how cyber security monitoring works.

How Does Cyber Security Monitoring Work?
Cyber security monitoring uses real-time response to help organizations identify threats faster and more efficiently. These threats are typically the result of active cyber-attacks or vulnerabilities found in the system. For this reason, cyber security monitoring relies on two main categories of monitoring to function: endpoint monitoring and network monitoring. Let’s learn more about those tools:
Endpoint Monitoring
Your endpoints are the devices that have access to your network. This includes laptops, PCs, smartphones, and more. This group of devices forms the endpoint boundary of your network and is often the first point of entry for most cyber threats. Endpoint monitoring ensures the continuous observation of all these crucial points along the edge of your network to detect and prevent potential malware files, unauthorized access, and other endpoint threats.
Network Monitoring
Similarly, network monitoring is the supervision, tracking, and analysis of the entire network to prevent cyber threats. Networks can have flawed components sometimes which can lead to weak areas - such as slow webpage loading and crashing sites. Essentially, network monitoring observes performance issues that could indicate vulnerabilities. This response is done through the constant monitoring of network traffic, activity logs, and more. Examples of network monitoring tools include SIEM systems, Intrusion Detection (IDS), and Behavioral Analytics (BA) systems.
It's the combination of these forms of monitoring that helps build the foundation for cyber security monitoring services. Now, let’s see why these tools of observation are so important for organizations.
Why Is Cybersecurity Monitoring Important?
To fully understand the need for cyber security monitoring, you have to understand the digital landscape it’s meant to secure. Cyber-attacks are becoming increasingly more complex and sophisticated as technology evolves and threat actors are finding easier ways to infiltrate networks. Even the 2023 World Economic Forum’s Global Risks Report listed cybersecurity as one of the current and future top 10 risks globally.
This means that organizations need a radical and consistent framework of protection where traditional cyber security seems to fail. This is where cyber security monitoring comes into the picture and actively reduces data breaches, prevents financial and reputational loss, and ensures a rapid response to threats before they can wreak damage. The rise of remote working environments has also expanded the attack surface for many threats and network vulnerabilities. Companies can benefit from cyber security monitoring in a variety of ways which is why it’s so important in the modern world. Next, let’s focus on those numerous benefits.
Benefits of Cyber Security Continuous Monitoring
Cyber security monitoring services can elevate and enhance your network protection in various ways. Some of the main advantages of cyber security continuous monitoring include:
- Marked Reduction in Cyber-Attacks: Naturally, a reinforced security boundary will prevent cyber-attacks from occurring. Continuous monitoring also limits the damage of a cyber-attack and helps to mitigate threats quickly and effectively in real-time.
- Boosts Employee Productivity: For most companies, network monitoring tools help to track employee productivity levels and can help organizations organize a more effective workforce. Scanning for network vulnerabilities also ensures that systems run more efficiently – which also boosts productivity.
- Regulatory Compliance: Cyber security monitoring tools also ensure that data integrity is maintained by preventing data breaches. Many industries have strict regulatory bodies that enforce harsh penalties for the misuse or ineffective management of user data. This means that monitoring services keep your company compliant – boosting brand image and customer trust.
- Reducing Downtime: Cyber threats force businesses to stop and assess damage during an attack. This downtime can cause substantial financial and reputational harm. Consistent monitoring ensures that networks are secure and functional at all times to prevent even the possibility of downtime.
- Implementing Advanced Threat Intelligence: With the use of consistent monitoring, your security system can create a store of threat intelligence that allows you to identify certain malware and anomalies faster. This will help to secure the network in the future and help to build a constantly evolving source of threat intelligence.
Cyber security monitoring services offer many more benefits for small or large organizations. However, you might still be unsure about the types of tools at your disposal. We’ll now take a closer look at some of the main cyber security monitoring tools you can put to work.
Cyber Security Monitoring Tools
There are various types of cyber security monitoring tools on the market that you can choose to invest in. We’ve taken the liberty of listing some of the main tools that will ensure a secure network for most organizations:
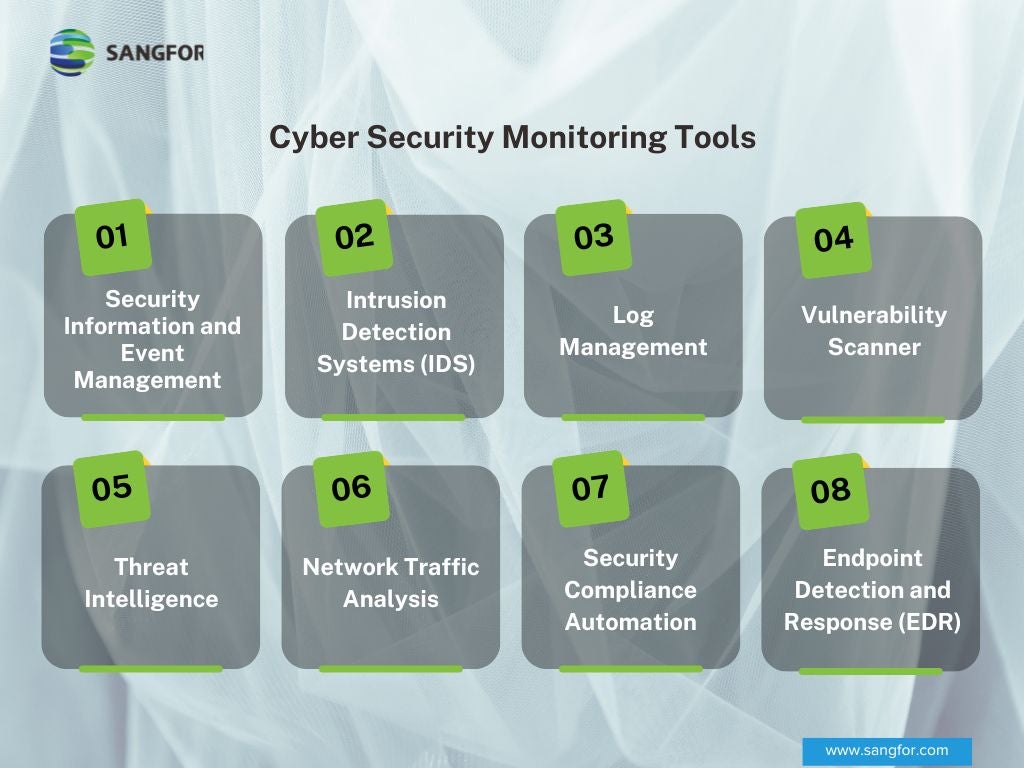
- SIEM Cyber Security Monitoring Tools: Security Information and Event Management - or SIEM – tools will help your company use accumulated data from logs and security incidents to enhance protection. These platforms use real-time data from multiple sources and proactive threat detection to generate alerts with actionable insights for security teams to put to use.
- Intrusion Detection Systems (IDS) Cyber Security Monitoring Tools: The Intrusion Detection System will immediately notify your security team of any unauthorized access, suspicious network behavior, malware, and more. These tools are based on proactive threat detection and automated malware identification using a baseline to flag odd activity.
- Log Management Cyber Security Monitoring Tools: This is the collection, storage, and analysis of all data in the system. Watch a video on how Sangfor can monitor the logs. Monitoring activity logs and activity on the network can help pinpoint suspicious behavior faster and build a better threat intelligence store. It also helps to identify user patterns and create a normal baseline to ensure that anomalous behavior is flagged in real-time.
- Vulnerability Scanner Cyber Security Monitoring Tools: Vulnerability scanning tools allow you to constantly monitor the network for any flaws or vulnerabilities. A single vulnerability scan can offer some insight but a continuous vulnerability scanning tool will ensure that weak spots are found and dealt with immediately – this includes misconfigurations, weak passwords, suspicious apps, and more. Threats can be found easily and quickly with the visibility and comprehensive monitoring of a vulnerability scanner platform. Explore Sangfor Managed Detection and Response services – MDR Services to learn more about vulnerability scanners.
- Threat Intelligence Cyber Security Monitoring Tools: Threat intelligence cyber security monitoring tools ensure that raw data, security incidents, and malicious files are analyzed properly to generate reports and intelligence feeds that prevent future cyber-attacks from happening.
- Network Traffic Analysis Cyber Security Monitoring Tools: Networks can be tricky to navigate based on their sheer size. This is why network traffic analysis tools can monitor all forms of network traffic to identify problems with data and files – both incoming and outgoing. This helps to spot issues like malware, latency, packet loss, and more.
- Security Compliance Automation Cyber Security Monitoring Tools: Effective security compliance automation tools ensure that your company maintains a strong security posture at all times to keep in compliance with set regulatory standards. These platforms provide real-time visibility across the network to ensure security protocols and policies are in place.
- Endpoint Detection and Response Cyber Security Monitoring Tools: Endpoint Detection and Response (EDR) tools are used to ensure the effective protection of all endpoint devices. From laptops to smartphones, your endpoints are vulnerable to cyber threats at all times. These tools prevent malware, data breaches, and suspicious files from entering the network while offering user-based analytics and intelligence.
Most cyber security monitoring companies will offer you solutions based on specific needs rather than an overarching approach to network monitoring. This is why Sangfor Technologies is the ideal choice for any organization taking their cyber security monitoring seriously.
Choosing Sangfor for Your Cyber Security Monitoring
Sangfor Technologies is an innovative and effective cybersecurity and cloud computing provider that’s dedicated to ensuring the best security posture for your organization. Sangfor boasts a range of security platforms that offer superior cyber security monitoring services. Some of the highlights you can look forward to from Sangfor include:
Sangfor’s Next-Generation Firewall
The AI-powered Sangfor Next-Generation Firewall (NGFW) can identify malicious files at both the network level and endpoints. With advanced malware detection and protection of Neural-X and Engine Zero, it provides comprehensive and holistic protection from all threats with easy operation - ensuring that any security threats are curbed swiftly and effectively.
Sangfor’s Endpoint Secure
The Next-Generation Firewall is also used in conjunction with Sangfor Endpoint Secure to identify malicious files at both the network level and endpoints. The Endpoint Secure platform provides integrated protection against malware infections and APT breaches across your entire organization's network – all with ease of management, operation, and maintenance.
Sangfor’s Incident Response
Additionally, Sangfor’s Incident Response is a service geared towards flexible, fast, and effective elimination and prevention of cyber-attacks. The focus of incident response is locating and eradicating threats while implementing active disaster recovery and providing tailored analysis to help safeguard your company from future cyber-attacks.
Sangfor’s Cyber Command
The Sangfor Cyber Command (NDR) Platform helps to monitor for malware, residual security events, and future potential compromises in your network and is coupled with an enhanced AI algorithm to keep you updated on any vulnerabilities or threats detected in the system.
Sangfor also offers advanced threat detection and response tools that can collaborate and coordinate to maintain the highest security measures. Sangfor ensures that your cyber security monitoring is effective, efficient, and affordable.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.
Frequently Asked Questions
Cyber security monitoring is an automated process that continuously monitors an organization’s network to detect cyber threats. This helps to proactively respond to these threats and minimizes damage to data and systems.
Some of the benefits of cyber security monitoring include:
- Reduces cyber-attacks
- Boosts productivity
- Ensures data integrity
- Ensures regulatory compliance
- Builds threat intelligence to prevent future security incidents
- Reduces risk of downtime
Some of the challenges involved in creating effective cyber security monitoring include:
- Evolving cyber threats
- Large networks
- False positives and alerts
- Limited budget constraints
- Lack of network visibility in remote environments
Automating monitoring processes ensures that no cyber threats get through the gaps and that visibility is consistent.





