Introduction
Microsoft Windows is an operating system which includes both server and desktop components along with an easy to use GUI. Windows provides functions that enable application programmers to use DNS functions like automatic DNS queries, comparing records, and look-up of names via the DNS API which was introduced with Windows 2000.
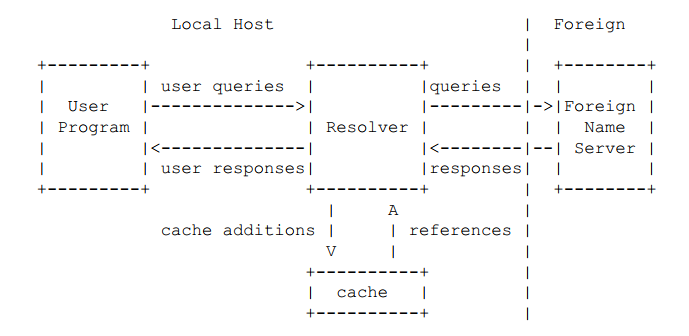
Below is one of the simplest interaction processes between user and DNS server:
DNS queries and responses are transmitted in DNS messages, which have the following structure:

In addition to standard queries and responses, DNS includes a Dynamic Update message type, which resembles a query/response in structure. However, the sections in a Dynamic Update message are "Zone, Prerequisites, and Updates" instead of "Question, Answer, and Authority."
The structure of DNS header is as follows:
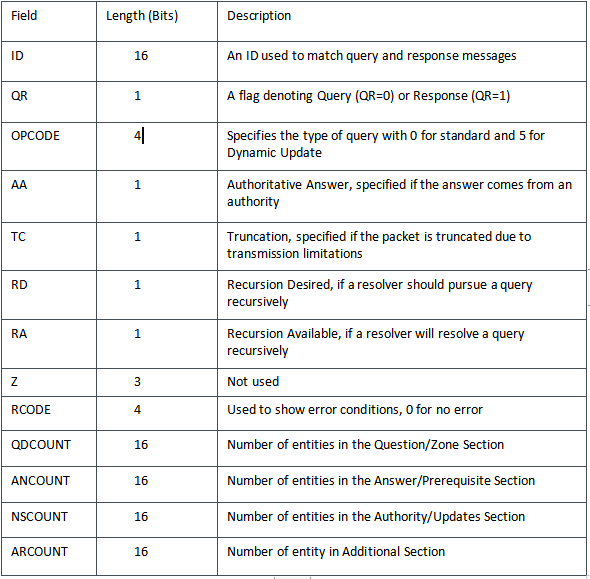
All multi-byte data is transmitted in big-endian order. Each of the sections, (Zone, Prerequisite, Updates, and Additional) contain a variable number of Resource Records (RR), which specify detailed information about DNS resources and entities. The structure of an RR is as follows:
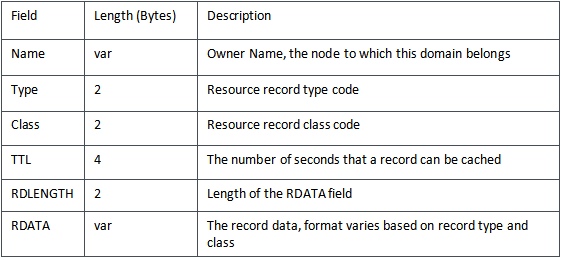
The "Zone" section contains an RR in the above format, with the exception that the TTL, RDLENGTH, and RDATA fields are omitted.
The "Name" field encodes zero or more DNS labels followed by a null-terminating character. Each label is a one-byte-length prefixed octet string. For example, a domain name such as "www.example.com" is split up into three labels, "www," "example," and "com," and they are together encoded as "\x03www\x07example\x03com\x00." Alternatively, instead of length-encoding an octet string, a label may contain a two-byte pointer, with its first two, most-significant bits set to one, and the remaining bits storing the offset in bytes from the start of the DNS header, where the uncompressed label occurs. For example, if the "Zone" section contains one RR with "Name" "\x03www\x07example\x03com\x00", then other RRs can refer to this name by using the two-byte pointer "\xc0\x0c" (where 0x0C is the offset from the start of a DNS packet where the Zone RR Name field occurs).
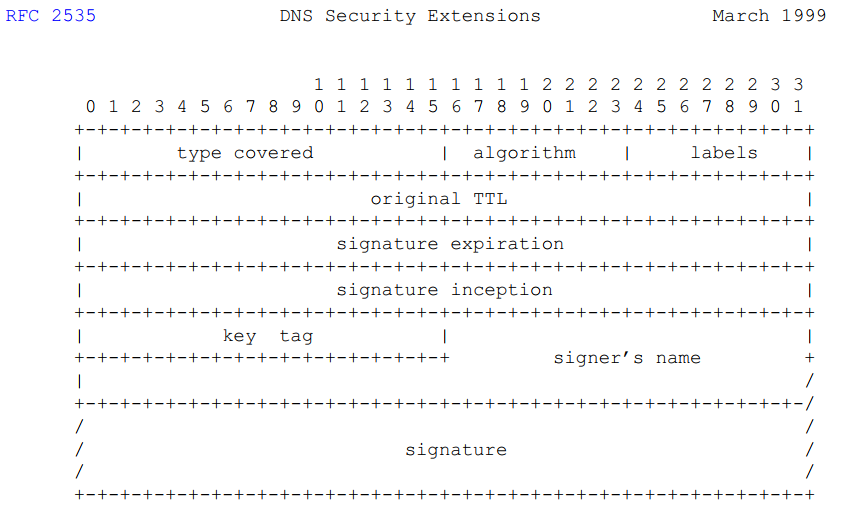
Dynamic Update is a mechanism for remotely updating DNS records on a server. Typically, it requires updates to be signed with the use of a pre-shared key, using RRs such as SIG or TSIG. The RRs to be updated are transferred in the Updates section of a Dynamic Update message. SIG RR has a "Type" of \x00\x18. The following shows the format of RDATA field of a SIGRR:
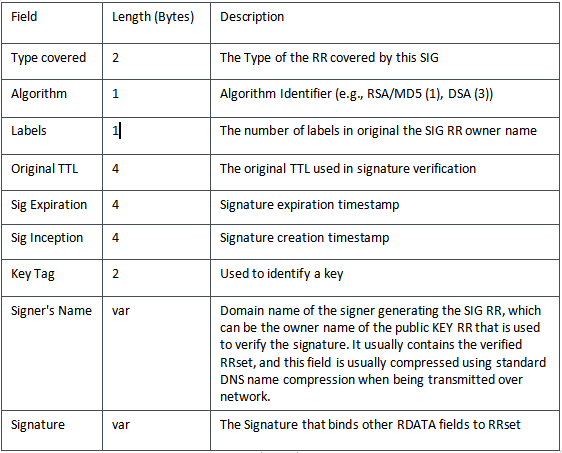
The structure is shown in the figure below:
Analysis
In Windows, DNS client and DNS server are implemented through two different modules:
- DNS Client: dnsapi.dll, responsible for handling DNS resolution
- DNS Server: dns.exe, responsible for answering DNS query
dns.exe implements a parsing function for various supported response types including:
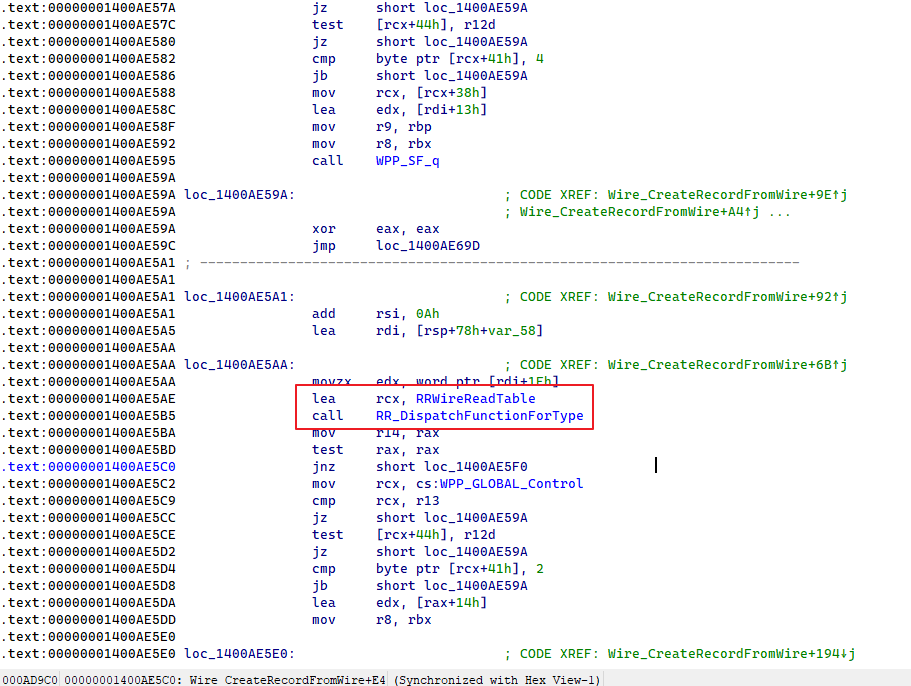
dns!RR_DispatchFunctionForType() uses RRWireReadTable to determine the corresponding handling function. Supported response types included in RRWireReadTable are as follows:





