Technology has evolved rapidly in the year 2023. However, this achievement has also increased the complexity of many cyber-attacks. Ransomware attacks have been at the top of this list for quite some time. Innovations such as Artificial Intelligence and Ransomware-as-a-Service platforms have made it easier for hackers to carry out ransomware attacks.
Ransomware attackers encrypt data and then demand a ransom amount in exchange for the files’ release or a security key. Typically, these ransoms are paid using Bitcoin to maintain anonymity. In this blog article, we explore the biggest recent ransomware attacks 2023 had in store for us and take a look at how Sangfor can help keep your data safe in the new year. Let’s first get a good idea of the state of ransomware 2023 left behind with some sobering statistics.
Ransomware Attack Statistics for 2023
The 2023 year has been quite eventful for ransomware attacks so far. Here are some ransomware attack statistics to consider as the year ends:
- Ransomware attacks went up more than 95% over 2022. (DarkReading)
- As of 2023, over 72% of businesses worldwide were affected by ransomware attacks. (Statista)
- The number of ransomware victims in 2023 has already surpassed what was observed for 2021 and 2022. (DarkReading)
- The media, leisure, and entertainment industry had the highest number of vulnerabilities exploited in ransomware attacks. (Statista)
- 36% of the organizations suffered ransomware attacks because of exploited vulnerabilities in 2023. Credential compromise was the second-most common cause of successful ransomware attacks, while malicious e-mail ranked third. (Statista)
- The average cost of ransomware attack 2023 sits at US$ 1.85 million. (GetAstra)
- The CL0P ransomware group has played a major role in the spike of 2023 ransomware activity. (DarkReading)
- The global average cost of a data breach in 2023 was US$ 4.45 million - a 15% increase over 3 years. (IBM)
- 51% of organizations are planning to increase security investments as a result of a breach - including incident response planning and testing, employee training, and threat detection and response tools. (IBM)
- The average savings for organizations that use security AI and automation extensively is US$ 1.76 million compared to organizations that don’t. (IBM)
While these can be disheartening statistics to consider, ransomware attacks are preventable for most companies with the right tools and skills. History is the greatest teacher of all which is why we’ll first explore the ransomware attacks 2023 made into headlines.

List of Recent Ransomware Attacks in 2023
2023 ransomware attacks were not pulling any punches and many companies got caught amid a financial and security crisis as a result. Here are some of the main ransomware attacks 2023 covered:
1. Dish Ransomware Attack 2023 – February
In February of 2023, the Dish Network was the victim of a ransomware attack after customers reported outages across its platforms. Disruptions were seen on the Dish websites, communications, and apps. While the company maintained that it was experiencing an “internal system issue” with concerned customers, an internal email was sent to Dish Network employees from management that warned them of an “ongoing VPN issue.”
In a public filing, the company admitted that a cybersecurity breach was the cause of the disruptions. However, a month later, customers were still having trouble accessing certain services and getting through to call centers.
In a filing with the Maine Attorney General's Office, the company confirmed that the data breach had affected 296,851 individuals and that the exposed information included names, license numbers, and other personal information. Bleeping Computer later reported that Dish “most likely” paid the ransom demands.
2. NCR Ransomware Attack 2023 - April
In April, financial services firm, NCR, was hit by a ransomware attack that disrupted payment processing systems. The parent company’s Aloha point-of-sale (POS) system and Back Office app were affected by the cyber-attack. While the company claimed that only one of its data centers was hit, that facility did not store customer financial information.
Popular ransomware group, BlackCat/AlphV, claimed responsibility for the NCR attack and warned that while they did not steal NCR data, they had login credentials that could open many doors to client systems. The threat was soon deleted from the ransomware site which usually indicates that negotiations were underway however, NCR declined to comment.
3. MOVEit Attack: CL0P Ransomware Group Exploits Vulnerability - May
In possibly one of the most far-reaching cyber-attacks of the year, the file-transferring software MOVEit was victim to a ransomware attack starting in May 2023. The CL0P ransomware gang began exploiting a previously unknown SQL injection vulnerability (CVE-2023-34362) in the MOVEit Transfer software which led to the attack affecting hundreds of billion-dollar companies including the BBC, Zellis, British Airways, Ofcom, Ernst and Young, Transport for London, and more.
The ransomware group warned that all the stolen data would be exposed on the dark web if the companies did not email them – presumably to discuss a ransom. On the 14th of June, the Cl0p gang listed the first batch of organizations it says it hacked by exploiting the MOVEit flaw.
While the group insisted that it had deleted any data stolen from governments, the military, and children's hospitals during the attacks, several US federal government agencies were still hit by the MOVEit breach. This led to the US State Department's Rewards for Justice program announcing a US$ 10 million bounty for information linking the Cl0p ransomware attacks to a foreign government.
4. City Of Dallas Ransomware Attack 2023 - May
The City of Dallas released a statement in May that it had picked up evidence of a ransomware attack launched within the city environment. Network printers began printing out ransom notes from the Royal ransomware group claiming responsibility for the attack.
In a blog post, the hacking group stated that it would soon share in the blog “tons of personal information of employees (phones, addresses, credit cards, SSNs, passports), detailed court cases, prisoners, medical information, clients’ information and thousands and thousands of governmental documents.”
Several servers were affected by the ransomware attack and had to be taken offline to prevent the spread of malware. The attack affected the Dallas police department, 311 customer service app, courts, water utilities, code compliance services, animal services, secretary’s office, and development services.
In August, the Attorney General's office released a report stating that 26,212 people were affected by the breach. The exposed data included names, addresses, social security numbers, and medical and health insurance information. The total number of people affected then rose to 30,253 after further investigation.
5. TSMC Supplier Hit by LockBit Ransomware Attack 2023 - June
In June, the Sangfor FarSight Labs discovered that the LockBit ransomware group listed TSMC on the LockBit 3.0 website. The Taiwan Semiconductor Manufacturing Company (TSMC) is the world's largest chipmaker and Apple’s biggest semiconductor provider.
TSMC identified Kinmax Technology, one of the company’s suppliers, as the main victim of the breach and that LockBit had demanded a hefty US$ 70 million ransom. Kinmax Technology confirmed the unauthorized access and theft of data but assured that the data was unrelated to the app used by their customers - emphasizing that no customer data was compromised as a result.
However, the LockBit group claimed to have access to TSMC's passwords, login credentials, and network entry points after the attack on Kinmax Technology and threatened to disclose the sensitive information if the semiconductor giant refused to make the payment. After the incident, TSMC immediately terminated its data exchange with the supplier following the company’s security protocols and standard operating procedures.
6. Johnson Controls Ransomware Attack 2023 - September
Johnson Controls filed an 8-K form on the 27th of September stating that the company had “experienced disruptions in portions of its internal information technology infrastructure and applications resulting from a cybersecurity incident.” The building solutions provider claimed that the incident had caused and was expected to continue to cause disruptions to parts of the company’s business operations.
The ransomware group known as Dark Angels is reported to have been behind the ransomware attack on Johnson Controls and the hackers claimed to have stolen 27Tb of data from the company’s systems. As a manufacturer of US industrial control systems, physical security alarms, and facility-related technology, Johnson Controls is still reeling from concerns about the downstream effects of the ransomware attack.
7. Sony Ransomware Attack 2023 - September
In September, Sony began investigating claims of a ransomware attack by an extortion group called RansomedVC. Almost 3.14 GB of uncompressed data, allegedly belonging to Sony, had been dumped on hacker forums and the group claimed to have successfully stolen the data and would now be selling it as the company refused to pay the ransom.
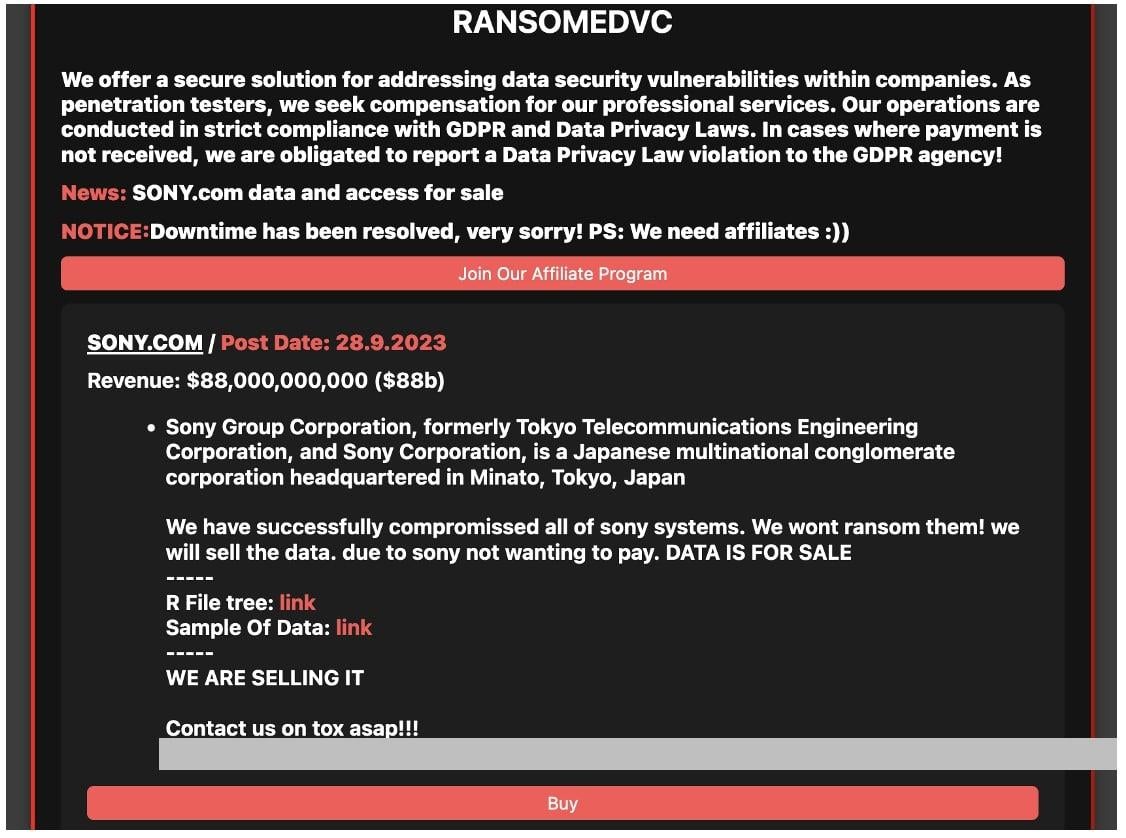
Sourced from Bleeping Computer
The RansomedVC group then shared with BleepingComputer that it had breached Sony's networks and stolen 260GB of data during the attack and that they were attempting to sell it for US$ 2.5 million. Matters took a turn when another hacking group called MajorNelson began to claim responsibility for the Sony attack - refuting RansomedVC's claims and stating that "RansomedVCs are scammers who are just trying to scam you and chase influence. Enjoy the leak."
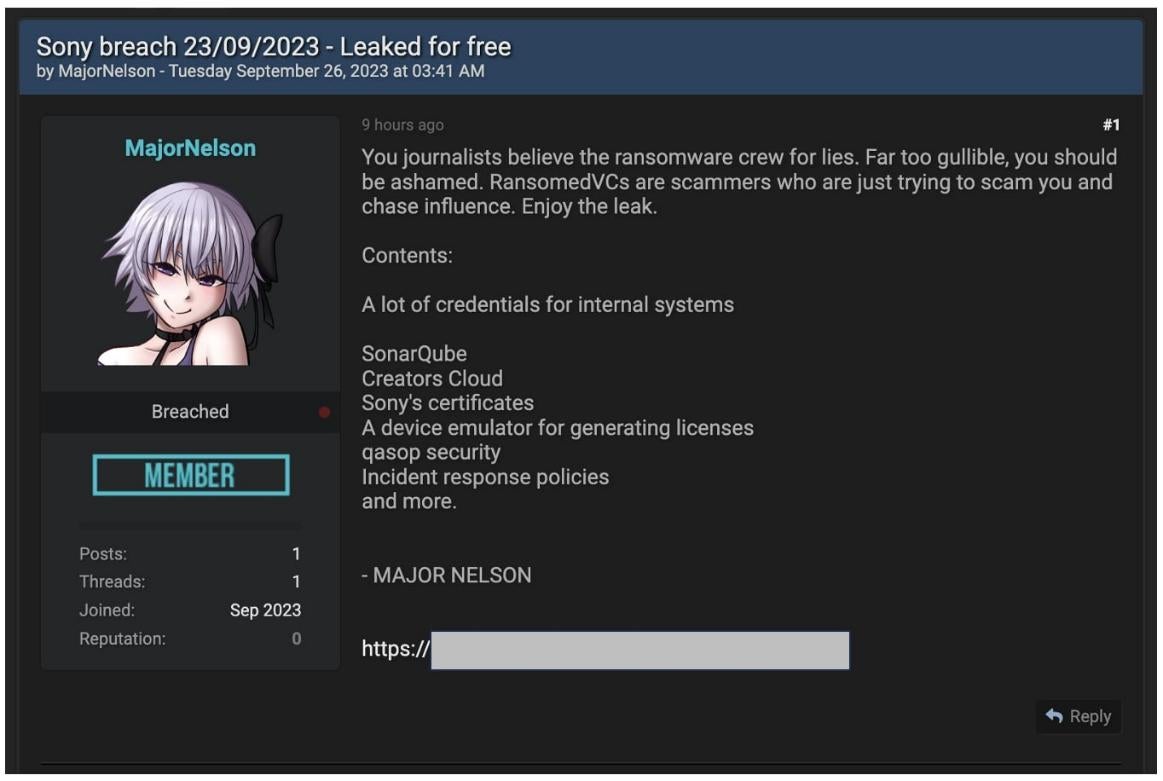
Sourced from Bleeping Computer
MajorNelson then "leaked for free" a 2.4GB compressed archive which contained 3.14GB of uncompressed data allegedly belonging to Sony.
Currently, the media giant is facing another alleged ransomware attack on its Insomniac Games division. On the 12th of December, the Rhysida ransomware group claimed to have attacked Insomniac Games and gave the video game developer six days to respond to an undisclosed ransom demand.
8. Las Vegas MGM Cyber-Attack 2023 - September
Early September was a difficult time for the Vegas crowd when two of the world’s largest hotel and casino companies were victims of ransomware attacks. Both MGM Resorts International and Caesars Entertainment reported that a social engineering attack disrupted their computer systems.
MGM Resorts identified a “cybersecurity issue” affecting some of its U.S. systems which were promptly shut down. The cyber-attack affected several MGM hotels – disrupting the company’s main website and mobile app, online reservations, ATMs, slot machines, and credit card machines.
While no customer bank account numbers or payment card information was exposed, the hackers made off with other personal information - including names, contact information, driver's license numbers, Social Security numbers, and passport numbers belonging to some customers who did business with MGM before March 2019. MGM estimated that the negative impact of the cybersecurity issue in September would amount to approximately US$ 100 million.
Unlike the MGM cyber-attack, most customer services at Caesars Entertainment were not disrupted. However, hackers managed to steal a copy of the Caesars Rewards loyalty program database which contained driver’s license numbers and/or social security numbers. The company further disclosed that the hackers had stolen the data of 41,397 Maine residents in the attack.
The hacking group, Scattered Spider, claimed responsibility for both the MGM and Caesars Entertainment cyber-attacks and collectively stole 6 terabytes of data. The MGM CEO, Bill Hornbuckle, stated that the company was well on its way to repairing the damage by the time the ransom note came and they saw no need to respond. However, it was widely reported that Caesars ended up paying US$ 15 million of the US$ 30 million demanded ransom for the promise to secure the data.

9. CDW Ransomware Attack 2023 - October
In October of 2023, CDW was the victim of a ransomware attack. The information technology products and services company said that it was “addressing an isolated IT security matter,” when the notorious ransomware group LockBit claimed to have stolen data during a cyber-attack. The group published a warning on its leak site warning that a ransom of US$ 80 million had to be paid if the data would be released.
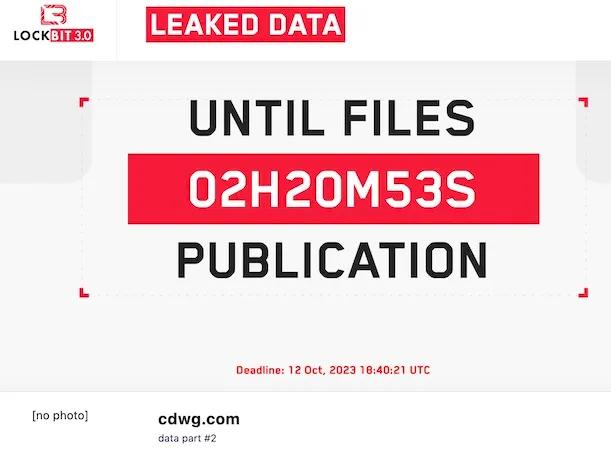
Sourced from CRN
The LockBit group also claimed that CDW offered them US$ 1.1 million in response to the US$ 80 million demand – which was seemingly not enough as the hackers took to leaking the data soon after. CDW admits to knowing about the leak and that the data exposed appeared to be “associated with employee badges, audits, commission payout data, and other account-related information.”
Ransomware attacks can be terrible for any company – big or small. However, hackers can take it a step too far when targeting certain industries. Unfortunately, hospital ransomware attacks were still common in the last year. Let’s look at some of the main ransomware attacks targeting healthcare facilities in 2023.
Hospital Ransomware Attacks 2023
According to the Institute for Security and Technology, at least 299 hospitals have experienced ransomware attacks in 2023. Hospitals are typically targeted by ransomware attacks due to the critical functions they provide. This means that hackers are more likely to be paid to keep lifesaving equipment online and confidential patient records sealed. A few of the key hospital ransomware attacks of 2023 include:
1. Managed Care of North America (MCNA) Dental
In March, Managed Care of North America Dental insurance company was the victim of a ransomware attack that affected 8.9 million patients. The hackers were able to “see and take copies of some information” in the company’s computer system between the 26th of February 2023 and the 7th of March 2023 – including patient names, addresses, dates of birth, phone numbers, and email addresses.
The LockBit ransomware group took responsibility for the cyber-attack and claims to have published all of the stolen files from MCNA Dental after the company refused to pay a US$ 10 million ransom demand. A listing on the group’s website implied that 700GB of MCNA Dental data was uploaded to the group’s website on the 7th of April and is now for sale on the dark web.
2. Harvard Pilgrim Ransomware Attack 2023
In April, Harvard Pilgrim Health Care (HPHC) was victim to a ransomware attack that compromised the data of 2,550,922 people. In the notice by HPHC, the company said that it “identified signs that data was copied and taken.” The information exposed included names, physical addresses, phone numbers, dates of birth, health insurance account information, Social Security numbers, provider taxpayer identification numbers, and clinical information.
Ransomware attacks are often deliberate and aimed at specific targets. Whether it’s a disgruntled ex-employee, a notorious ransomware group, or a lone hacker, ransomware attacks are now becoming worryingly more accessible as well. While a ransomware attack might be difficult for the common person to understand and implement, several Ransomware-as-a-Service organizations are willing to put in the hard work for you. Let’s learn more about them now.
Active RaaS Groups 2023
Ransomware-as-a-Service – or RaaS – is a business model in which a threat actor will pay an experienced ransomware developer to use their ready-made ransomware to execute their attacks. Sangfor has also noted the rapid growth of the RaaS industry in our Global Ransomware Trends Report. These RaaS platforms have made it easier for amateurs to weaponize ransomware for their agendas. Some of the main Ransomware-as-a-Service groups that have been operating in 2023 include:
LockBit Ransomware Group
The LockBit ransomware gang is a notorious RaaS group that emerged in September 2019. Operating on a profit-sharing model, LockBit offers its encryption services to affiliates who target organizations. This includes the use of variants such as .abcd, LockBit 1.0, LockBit 2.0, LockBit 3.0, and LockBit Green.
In a joint cybersecurity advisory from the Cybersecurity and Infrastructure Security Agency (CISA) and other bureaus in June, LockBit was painted as a serious and pervasive threat. The advisory states that the group was the most deployed ransomware variant across the world in 2022 and that one in every six ransomware attacks that targeted US government offices in 2022 was traced back to LockBit actors.
However, due to the sheer number of disconnected affiliates, LockBit’s Tactic, Techniques, and Procedures (TTPs) all vary significantly – which is a challenge for cybersecurity organizations. Some of the methods by the group to attract affiliates include:
- Payments to affiliates before payments to the core group.
- Disparaging other RaaS groups in online forums.
- Engaging in publicity-generating activities and stunts
- Developing and maintaining a simplified, point-and-click interface for its ransomware.
The group is also said to use several repurposed freeware and open-source tools that are intended for legal use. Sangfor's expert cybersecurity team has identified multiple cases of the LockBit ransomware being active in China, Thailand, Indonesia, Europe, and America.
BlackCat Ransomware Group
The BlackCat Ransomware Group is another Ransomware-as-a-Service group. BlackCat – also known as ALPHV – leverages previously compromised user credentials to gain initial access to the victim system. Once the BlackCat malware is inside, it compromises Active Directory user and administrator accounts. The malware then uses Windows Task Scheduler to configure malicious Group Policy Objects (GPOs) to deploy ransomware.
According to the FBI, many of the BlackCat group’s operators include developers and money launderers who originated from the DarkSide Ransomware as a Service (RaaS) platform. In 2022, the FBI also confirmed that BlackCat is written in Rust which is "considered to be a more secure programming language that offers improved performance and reliable concurrent processing."
The BlackCat RaaS business model revolves around letting threat actors use their ransomware, conduct their campaigns, and keep a percentage of what they earn. While most RaaS operations allow affiliates to keep 70% of their profits, BlackCat affiliates keep up to 80-90%. The group has also achieved something that no other RaaS operation has by creating a data leaks website on the public internet.
CL0P Ransomware Group
The Cl0p Ransomware Group surfaced in 2019 using the Cl0p ransomware - which is part of the Cryptomix ransomware family. Using the “.clop” extension after encrypting a victim's files, the group creates a unique string “Don’t Worry C|0P" within ransom notes left behind.
Clop ransomware will attempt to disable Windows Defender and remove the Microsoft Security Essentials to avoid detection. While phishing emails have been a primary initial access vector for Clop ransomware, many reports have shown that it also exploits the following Common Vulnerabilities and Exposures (CVE): CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, CVE-2021-27104, and CVE-2021-35211.
The group uses the double extortion model in which a threat actor will encrypt and exfiltrate sensitive information after which the sensitive data will be released on their dark web leak site if payment is not made. Notable Cl0p ransomware victims include Accellion, MOVEit, IBM, Deloitte, and many more. According to a CISA advisory, the Clop gang and its affiliates compromised over 3,000 organizations in the US and over 8,000 globally.
With many options for hackers, ransomware attacks can be daunting for most companies and individuals alike. However, with the right tools, people can protect themselves and their businesses from ransomware attacks in the future – and Sangfor is leading the way.
Are You Prepared for a Secure 2024? Download the Sangfor 2024 Calendar
Step into the new year with a sense of security with Sangfor. With reliable cybersecurity platforms and advanced technologies, Sangfor will ensure superior anti-ransomware protection for your network.
The Sangfor 2024 Calendar is your roadmap to a more cyber-resilient year. Download this detailed, convenient, and useful guide that provides you with all signposts needed to enhance your security posture in 2024. Make the best choice for a new year of cybersecurity superiority and download the Sangfor 2024 Calendar today.
DOWNLOAD THE 2024 CALENDAR NOW
Take your cybersecurity seriously and invest in Sangfor’s integrated and holistic security solutions today for a safer tomorrow:
Sangfor’s Next-Generation Firewall
Sangfor’s ransomware solution uses an advanced Network Secure - Next Generation Firewall (NGFW) in conjunction with Endpoint Security to identify malicious files at both the network level and endpoints. The advanced firewall is a security device designed to inspect network and application traffic for threats, secure the network environment from intrusion, and bring in security intelligence from outside the network.
Sangfor Cyber Command
The Sangfor Cyber Command Network Detection and Response NDR platform goes on to monitor for malware, residual security events, and future potential compromises in your network and is coupled with an enhanced AI algorithm and threat intelligence – ensuring your data is always kept strictly protected and consistently monitored for lingering threats.
Sangfor Endpoint Secure
Lastly, Sangfor’s powerful Endpoint Secure (EDR) solution is used to go beyond traditional antivirus and anti-malware software. Leveraging Sangfor’s proprietary Engine Zero AI-powered malware detection engine and Neural-X threat intelligence platform to deliver unrivaled malware protection at all endpoints.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.





