In 2022, 71% of companies worldwide were affected by ransomware. The statistics alone speak for themselves to show that ransomware is on the rise. Scaling ransomware attacks by hacker groups are now also stealing headlines - notably, those of the Cl0p ransomware gang.
While a typical ransomware attack involves the use of malware to extort money from a company while holding data hostage, these days ransomware attacks have become more complex. The use of ransomware-as-a-service models has simplified the process for criminals.
Similar to software-as-a-service frameworks, ransomware-as-a-service is the use of already-constructed ransomware. Users of this service pay to launch ransomware developed by expert operators. Organizations need to stay updated on the threat actors targeting networks to ensure better cybersecurity and prevent ransomware attacks.

What Is the Cl0p Ransomware Gang?
CLOP – or cl0p – is derived from the Russian word “klop” which translates to “bedbug.” The group surfaced in 2019 using its namesake ransomware which is part of the Cryptomix ransomware family.
The Cl0p ransomware uses the “.clop” extension after encrypting a victim's files. A unique feature of the strain is its string “Don’t Worry C|0P" within the ransom note left behind. The ransomware attempts to disable Windows Defender and remove the Microsoft Security Essentials to avoid detection.
The US Health Sector Cybersecurity Coordination Center (HC3) revealed in an analyst note that the Cl0p ransomware is believed to have been developed in Russia and is a popular payload for groups such as FIN11 and other Russian affiliates.
The note goes on to describe how Clop was written to target Windows systems and some reporting samples showcase that it is a Win32 executable written in C++. “The executable packet is compressed, which helps hide its functionality. The ransomware encrypts files with an RSA 1024-bit public key with RC4 that uses 117 bytes of the public key.”
Phishing emails have also been a primary initial access vector for Clop but reports have shown that it also exploits the following Common Vulnerabilities and Exposures (CVE): CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, CVE-2021-27104, and CVE-2021-35211.
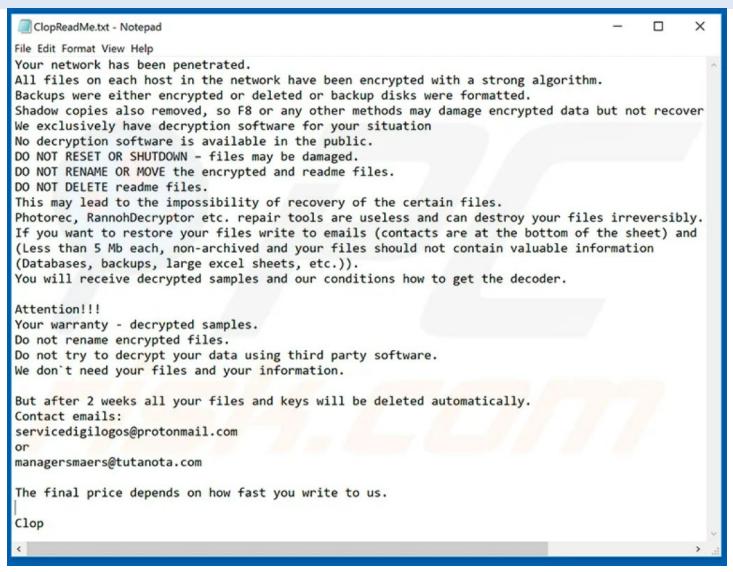
The HC3 also shares that once a network has been compromised, remote desktop protocols are used and Cobalt Strike is deployed to aid in lateral movement. After encryption is complete, the victim can access a dropped README.TXT and the encrypted file’s extension will be changed to ‘Clop’.
In the ransom note, it states that the Shadow Volume Copies have been deleted and the decryption key is only available from the group. It also claims that all the files will be deleted after two weeks have passed.
The ransom note also contained the emails unlock@eqaltech.su, unlock@royalmail.su, and kensgilbomet@protonmail.com which can be used to contact the attackers for payment instructions.
Source: hhs.gov
Financial gain appears to be the group’s primary goal, which they leverage through the use of the double extortion model. The threat actor will encrypt and exfiltrate sensitive information. Thereafter, sensitive data will be released on their dark web leak site if payment is not made.
List of Cl0p Ransomware Attacks Reported
Cl0p has continued to make headlines around the world for its ransomware attacks on industries - typically exploiting organizations with a revenue of US$ 5 million or higher. We’ve drafted up a brief overview of some of the cyber-attacks by the Cl0p ransomware gang so far:
ExecuPharm
In March 2020, the pharmaceutical giant revealed that it had been hit by a ransomware attack. The company stated that social security numbers, financial information, driver’s licenses, passport numbers, and other sensitive data may have been accessed.
The data was found on the dark web associated with the Cl0p ransomware gang. The site contained a vast cache of data - including emails, accounting records, user documents, and database backups – all stolen from ExecuPharm’s systems.
TechCrunch reported that while Cl0p said it would not attack hospitals, nursing homes, or charities, ExecuPharm would not qualify as commercial pharmaceutical companies “are the only ones who benefit from the current pandemic.” Around 163GB of unencrypted files were stolen.
Indiabulls Group
Financial services group, Indiabulls confirmed that it was the victim of a Cl0p ransomware attack. The hackers threatened to leak stolen data if the company failed to pay the ransom within 24 hours. However, a spokesperson for the group assured that the information leaked was “not sensitive in nature” and that all affected systems were restored properly.
Software AG
In October 2020, Cl0p became the first ransomware to demand payment of over US$ 20 million when it infected Software AG - the second largest enterprise software firm in Germany. After negotiations failed, the Cl0p gang published screenshots of the company's data onto the dark web – including employee passport and ID scans, employee emails, financial documents, and directories from the company's internal network.
Accellion Hack
December 2020 marked the start of several cyber-attacks that involved the Cl0p ransomware gang and the FIN11 threat group. Up to 100 companies were breached with multiple zero-day vulnerabilities and a new web shell.
The enterprise cloud file-sharing company revealed that threat actors used its 20-year-old File Transfer Appliance (FTA) to compromise data from multiple companies. The list included supermarket giant Kroger which exposed HR data and pharmacy records, Singtel, QIMR Berghofer Medical Research Institute where 73 GB of data was stolen, the Reserve Bank of New Zealand, the Australian Securities and Investments Commission (ASIC), and the Office of the Washington State Auditor.
Investment giant, Morgan Stanley was also added to the list of victims when its account maintenance third-party vendor was also affected by the Accellion breach.
While Accellion claimed to have resolved the vulnerability and released a patch within 72 hours, the impact of the breaches has still left many clients reeling.
In June of 2021, law enforcement agencies from Ukraine, South Korea, and the US joined forces to arrest six people suspected of being involved in the CLOP ransomware gang. The operation was coordinated from INTERPOL's Cyber Fusion Centre in Singapore and targeted Cl0p for its multiple attacks against Korean companies and US academic institutions.
These arrests led to a lull in the gang’s activities which was thought to be the beginning of the end for the group. However, a few days after Operation Cyclone – as it was named - the ransomware group continued to grab headlines by publishing data obtained from multiple new victims.
Cl0p Water Company Identity Issues
In August of 2022, the Cl0p ransomware gang claimed responsibility for a ransomware attack on South Staffordshire Water. However, some confusion followed the announcement as the group appeared to have misidentified the company as Thames Water instead.
South Staffordshire Water assured that its ability to provide safe water was not compromised in the breach. Cl0p’s site claimed to have stolen 5TB of data – including scanned copies of passports and ID cards belonging to South Staffordshire employees.
BleepingComputer suggested that the group’s misidentification of Thames Water – which is the largest water supplier in the UK – was perhaps an attempt to extort a larger, more lucrative victim.
Cl0p Healthcare Scare
In January 2023, the US Health Sector Cybersecurity Coordination Center (HC3) released an analyst note commenting that despite the arrests made in 2021, the group’s activity appears to be uninterrupted. The note also explained that the gang experienced difficulty in getting victims to pay ransoms which has led to a change in their tactics that directly impacts the Health and Public Health sector.
The Cl0p group began infecting files disguised to look like medical documents and submitting them to facilities. They would then request a medical appointment hoping those malware files would be opened. The note cautioned that these attacks would have a higher chance of working due to the expansion of the COVID-19 telehealth environment.
GoAnywhere MFT
Developers of the GoAnywhere MFT file transfer solution warned customers of a zero-day remote code execution vulnerability on exposed administrator consoles. The security flaw - now tracked as CVE-2023-0669 - allows attackers to gain remote code execution on unpatched GoAnywhere MFT instances with their administrative console exposed to Internet access.
The ransomware group reached out to BleepingComputer to claim that it had allegedly stolen the data from over 130 organizations over the course of ten days after breaching servers vulnerable to exploits targeting this bug.
Cl0p claimed that it could move laterally through networks and deploy ransomware payloads to encrypt their systems but decided against it and only stole the documents stored on the compromised GoAnywhere MFT servers.
Crown Resorts
Crown Resorts has also confirmed a potential global data breach after a limited number of company files were accessed illegally. A Crown Resorts spokesperson confirmed in an update that the breach was through the breach of the GoAnywhere third-party file transfer service.
The statement claims that “a small number of files have been released on the dark web - including employee time and attendance records and some membership numbers from Crown Sydney.” The company assured also that no personal information of customers has been compromised as part of the breach.
Tasmanian Government
The Tasmanian government announced that it was caught up in a data theft incident. In April 2023, the government revealed in a precautionary statement that the latest investigations “indicate a risk that financial data from the Department for Education, Children, and Young People may have been accessed in the global incident."
According to the statement, the data may include names, addresses, invoices, and bank account numbers. This breach was made possible through the GoAnywhere hack by the Cl0p ransomware group.
Saks Fifth Avenue
In March 2023, the Cl0p ransomware group listed the luxury retailer on its data leak website among its latest victims. While the group didn’t disclose additional information about the specifics of the data stolen or the ransom negotiations, BleepingComputer has confirmed that the incident is linked to Cl0p's ongoing attacks targeting GoAnywhere servers vulnerable to a security flaw.
While ransomware groups continue to evolve, it’s important to note how to prevent ransomware attacks from damaging your network.
Sangfor’s Ransomware Solutions
Based on world-class cybersecurity and cloud computing technology, Sangfor offers intensive and advanced Anti-Ransomware solution and state-of-the-art infrastructure to help protect your network. Ransomware detection and avoidance have never been simpler with this integrated solution that pieces together several advanced Sangfor products:
Next-Generation Firewall (NGAF)
Sangfor’s Next-Generation Firewall (NGAF) uses an advanced network security firewall for comprehensive and integrated surveillance and protection of your entire security network. Investing in a hardware firewall is also essential to network security for protection from malicious traffic and cyber-attacks.
Endpoint Secure
The correlated response works beside endpoint security to isolate the breach in the direction of inbound and/or outbound traffic. Sangfor’s Endpoint Secure solution is an advanced endpoint protection system that detects and prevents malware on PCs and servers - deployed at over two million endpoints worldwide.
Cyber Command
The groundbreaking Cyber Command solution is a network detection and response platform that provides automated responses to threats. Using AI and machine learning technology to help your company isolate, analyze, and eliminate potential threats before they can infiltrate your system. Endpoint Secure works with Cyber Command to collect data for analysis and use its confining and scanning capabilities for advanced threat detection.
Sangfor has the only complete, holistic security solution to prevent and mitigate ransomware attacks in real time. No other anti-ransomware prevention tool can impact every step in the ransomware kill chain and no other solution is modular enough to be tailored to the requirements and budget of an organization.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.





