Ransomware has become a growing problem for most companies. As more advanced methods are used by hackers, more businesses come under attack. The latest victim of a headline-grabbing ransomware attack has been the file-transferring software called MOVEit Transfer.
Progress Software is a US company that supplies MOVEit Transfer to many businesses for them to securely move files around company systems. In a security advisory released by the company, it was revealed that a vulnerability had been discovered in the MOVEit Transfer software that could lead to “escalated privileges and potential unauthorized access to the environment.”
On the 27th of May 2023, the CL0P ransomware gang - also known as TA505 - began exploiting a previously unknown SQL injection vulnerability (CVE-2023-34362) in the MOVEit Transfer software.

Cl0p Ransomware Attack
The Cl0p ransomware group emerged in 2019 and uses the “.clop” extension after encrypting a victim's files. The Russian hacking gang has reached headlines worldwide and extorted multiple companies in the past.
On the 4th of June, Microsoft’s Threat Intelligence team pinned the cyber-attack on "Lace Tempest" - a threat actor known for running the Cl0p extortion website. Experts have said that while the cyber-attack was successful - affecting hundreds of billion-dollar companies throughout the Western world – it was also surprisingly simple.
Microsoft went on to explain that after the exploit, the hacking group authenticates as the highest privileged user on the system. It then deployed a web shell to collect all the data. The shell - called LEMURLOOT – is designed to interact with the MOVEit platform.
On the evening of June 6th, the Cl0p ransomware gang claimed the credit for the MOVEit attack in an announcement to affected organizations. The group warned all the businesses victims of the MOVEit attack to email them before a specified date or else the stolen data will be published.
The post reveals in broken English that the Cl0p group is behind the attack and that they have “information on hundreds of companies.” The companies are asked to use a given chat URL to continue talks where proof of data will be given and a ransom amount will be agreed to.
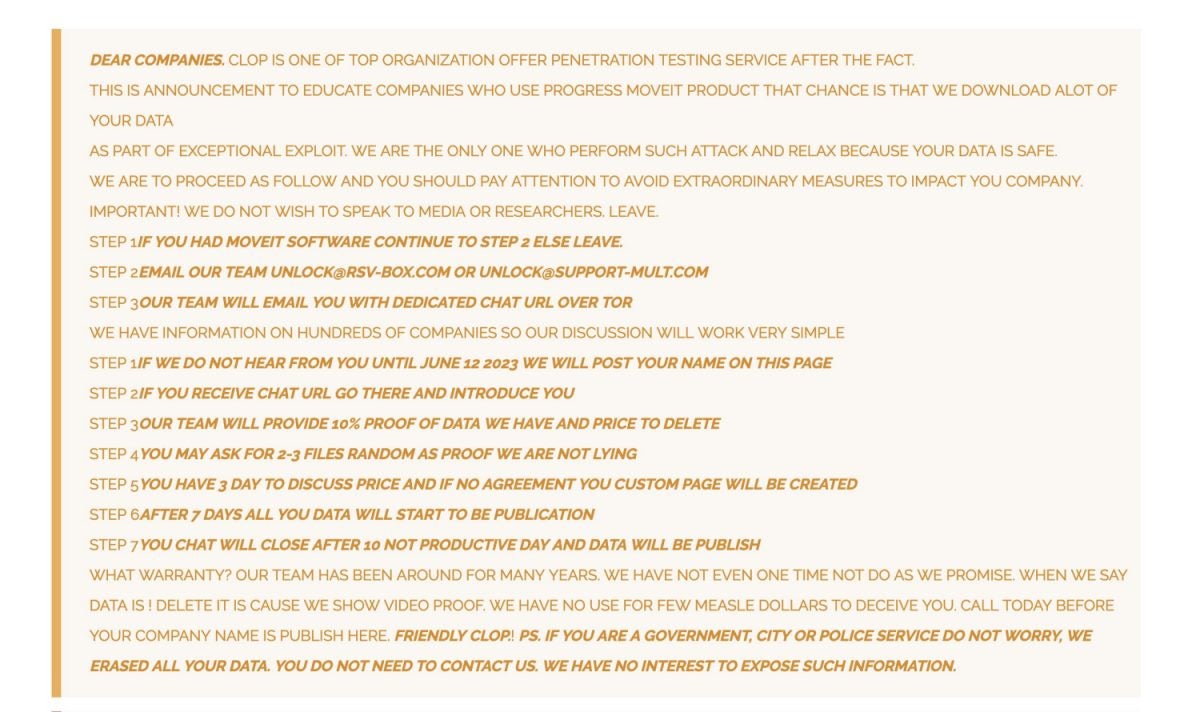
Source: @PinkCursor on Twitter
The group threatened to expose the company names and all the data on the dark web if not entertained. The Cl0p group also added in an email to BleepingComputer that they had deleted any data stolen from governments, the military, and children's hospitals during the attacks. The email stated, "I want to tell you right away that the military, children's hospitals, GOV, etc. like this we no to attack, and their data was erased."
Cybersecurity professionals have still reminded the public that criminals should not be trusted.
The tactic used by the ransomware group is somewhat unusual as typical ransom demands are sent directly to the company. However, the group is now asking for the companies affected to contact them instead. This is possibly because the hackers themselves cannot keep up with the scale of the attack which is still being processed around the world.
A Growing List of MOVEit Attack Victims
The UK-based payroll services provider, Zellis, was one of the MOVEit Transfer users affected. The company confirmed that 8 of its client firms have had their data stolen - including home addresses, national insurance numbers, and bank details in some cases. Not all firms have had the same data exposed.
BBC
BBC reported that the notice resulted in stolen payroll data from over 100,000 members of staff within the BBC, British Airways, and the pharmacy chain Boots. Other organizations that may have also been breached include Aer Lingus, an international airline, as well as the Nova Scotia government and the University of Rochester.
BBC assures that its staff has been warned personal data may have been stolen. In an email to employees, the broadcasting company said data stolen included staff ID numbers, dates of birth, home addresses, and national insurance numbers.
British Airways
The staff at British Airways have also been warned that their bank details may have been stolen as well. The UK's National Cyber Security Centre said it was monitoring the situation and urged organizations using the compromised software to carry out security updates.
Ofcom
Another company recently stepping forward as a victim of the hack include Ofcom – the UK’s communications regulator. The organization released a statement detailing that a limited amount of information about certain companies regulated by Ofcom – including confidential data – and the personal data of 412 Ofcom employees was downloaded during the MOVEit attack.
While no payroll data or Ofcom systems were compromised during the cyber-attack, the company "swiftly" alerted all the affected companies that it regulates. It also went on to refer the matter to the data and privacy watchdog, the Information Commissioners Office (ICO).
Transport for London
Transport for London - which operates the UK capital's public transport system – revealed that it had been affected by the MOVEit hack as well. The company confirmed that one of its contractors suffered a breach and assured the public that they were writing to all involved and that the attack did not affect customer information or banking details.
Ernst & Young
Another victim of the attack included accountant firm, Ernst & Young. The company shared with the BBC that the vast majority of its systems which used the software were unaffected but added that it was manually and thoroughly investigating systems where data may have been accessed.
Prudential Malaysia
In Malaysia, two Prudential companies - Prudential Assurance Malaysia Bhd (PAMB) and Prudential BSN Takaful Bhd (PruBSN) also confirmed affected by the MOVEit cyber security incident. According to both firms, personal agent and customer data, comprising names, contact numbers, national identification numbers, and partial credit card information or bank account details, may have all been impacted. The companies have established a dedicated hotline with extended operating hours to inform affected customers and provide any necessary assistance.
While no ransom demands have been made public yet, experts claim that it is likely that the group will attempt to extort money from the organizations themselves rather than individuals. The affected companies are reminding staff to be vigilant of any suspicious emails that could lead to further cyber-attacks.
CISA and FBI Reaction to MOVEit Attack
The US Cybersecurity and Infrastructure Security Agency announced on the 7th of June that its new cybersecurity advisory is meant to warn and guide companies after the MOVEit attack. The organization advised that affected companies take the following steps:
- Take an inventory of assets and data, identifying authorized and unauthorized devices and software.
- Grant admin privileges and access only when necessary, establishing a software allow list that only executes legitimate applications.
- Monitor network ports, protocols, and services, activating security configurations on network infrastructure devices such as firewalls and routers.
- Regularly patch and update software and applications to their latest versions and conduct regular vulnerability assessments.
The FBI and CISA encourage organizations to implement these recommendations to reduce the likelihood and impact of CL0P ransomware and other ransomware incidents.
Sangfor Ransomware Solutions
Sangfor Technologies is a world-class cybersecurity and cloud computing company that offers intensive and advanced Anti-Ransomware prevention and state-of-the-art IT infrastructure.
Sangfor offers complete and holistic security solutions using a range of platforms and products. These include an advanced Next Generation Firewall (NGFW) integrated with Endpoint Security to identify malicious files at both the network level and endpoints and so much more.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.





