1. The Bank of Chile closed all branches after the ransomware attack
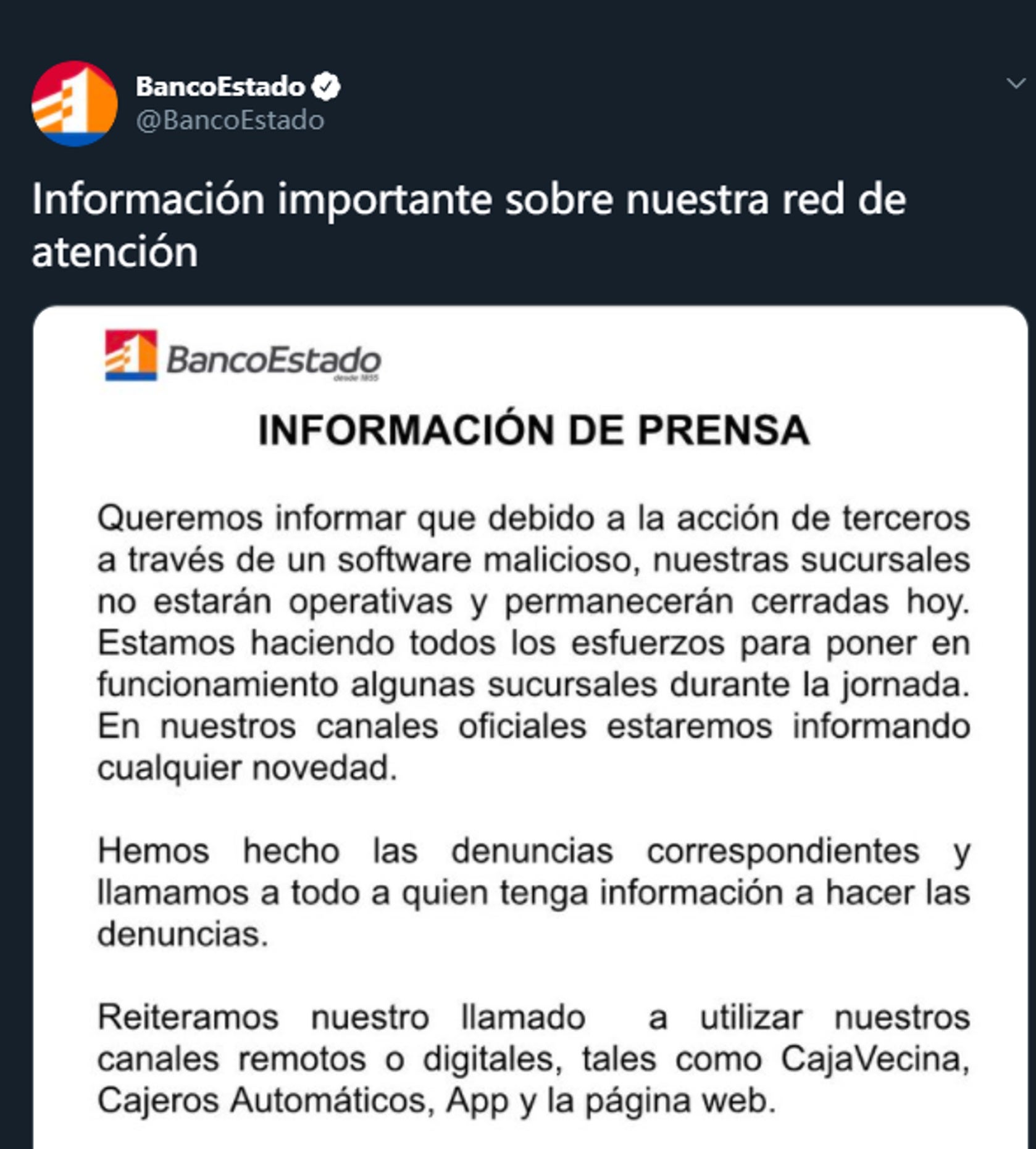
BancoEstado, one of the three largest banks in Chile, was forced to close all branches after a recent cyberattack. The bank released a statement on its Twitter account saying, "Our branches will not be operational and will be closed today."
Development
According to public information, the bank’s internal network has been infected with Sodinokibi (REvil) ransomware, which found its way in through an employee who received and opened a malicious file disguised as an office document. The malicious file installed a backdoor program on the bank’s network. Investigators believe that hackers used this backdoor to access the bank’s network and install ransomware. Bank employees working on the weekend found the anomaly when they arrived on a Saturday, which blocked their access to work files.
Conclusion
Sodinokibi ransomware was first discovered in China in April 2019 and shortly thereafter, in Italy in May, and spreads by means of RDP attacks. It has a certain degree of similarity with the GandCrab ransomware. The REvil ransomware criminal gang is one of the few organizations that has a data leakage site that steals unencrypted files from the victim’s network and publishes them, exerting extra pressure to encourage the victim to pay the requested ransom.
2. School district in North Carolina forced to close due to SunCrypt ransomware attack
The Haywood County School District in North Carolina, USA announced that they were attacked by ransomware on August 24, 2020, causing the region to shut down its network and stop distance learning programs that began on August 17.
Development
The school district resumed distance learning on August 31 after the attack, but the technical services of some schools were still affected. After investigating, the school district stated that unencrypted data had been stolen by the attacker.
Conclusion
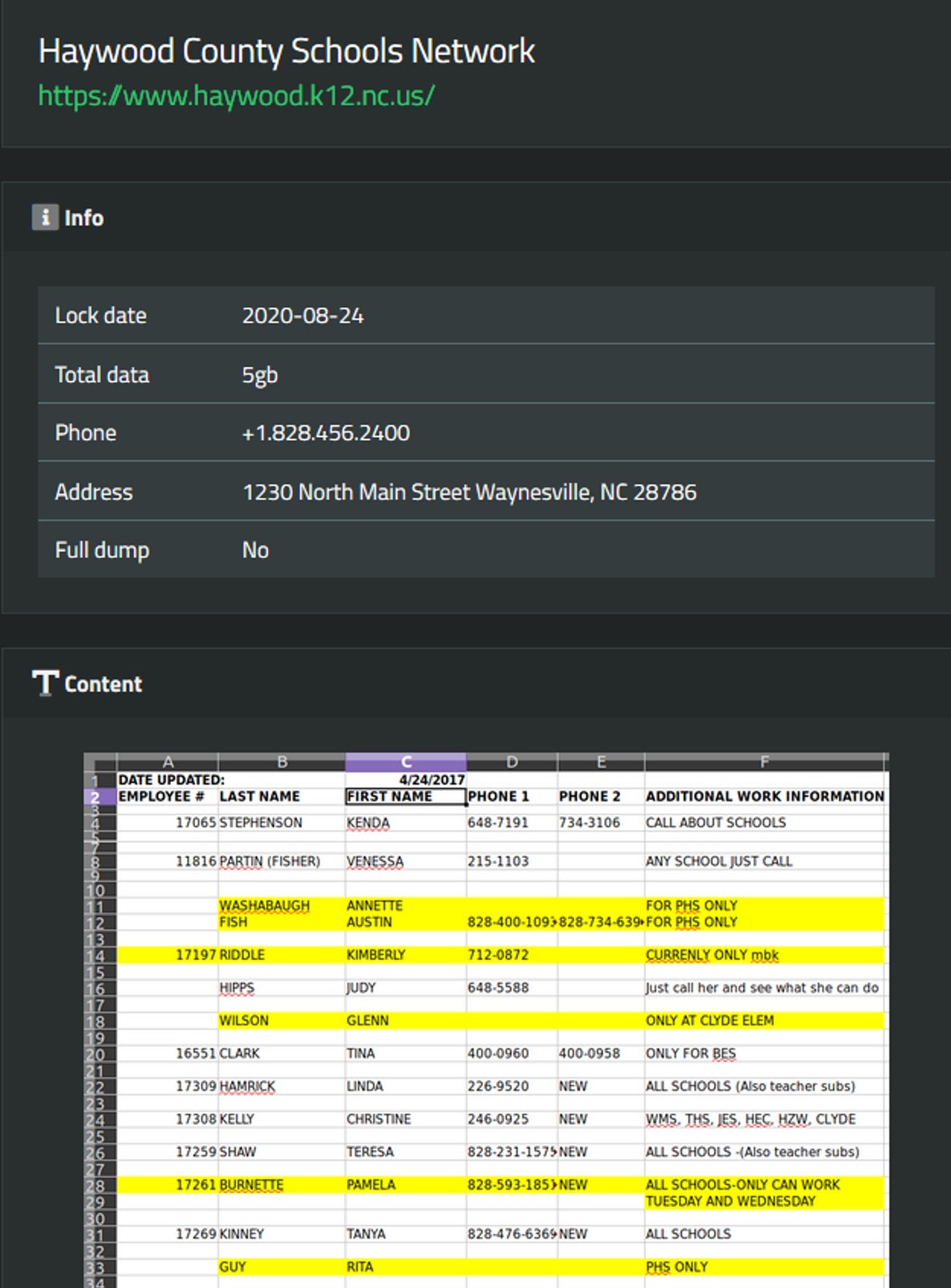
SunCrypt ransomware began to appear in October 2019, but was not very active at first. The Maze group, a separate hacker organization, was operating at the same time but typically not the most organized gang, until they began to specialize in ransomware in conjunction with SunCrypt. The two groups are known to cooperate and share profits. As a member of a large ransomware organization, it is natural to establish a data breach site, and at present, according to statistics, the SunCrypt data leakage site has listed nine victims and their sensitive data files. Below is the data from the Haywood Country School District.
3. Netwalker ransomware attacks Argentine government agencies, demanding US$4 million
Recently, Dirección Nacional de Migraciones, Argentina’s official immigration agency, was attacked by Netwalker ransomware, causing the temporary suspension of transit operations in the country.
Development
In order to prevent the ransomware from infecting other devices, the computer network used by the immigration and control station was shut down. According to the Argentine news website Infobae, this caused border crossings to be suspended for four hours while the server was rebooted. The National Immigration Service (DNM) stated: “The Integrated Immigration Capture System (SICaM) operating at international border crossings is particularly affected, which has caused delays in entering and leaving the country’s territory.” A government source told Infobae, “They will not be negotiating with hackers, they will not worry too much about the need to decrypt the data."
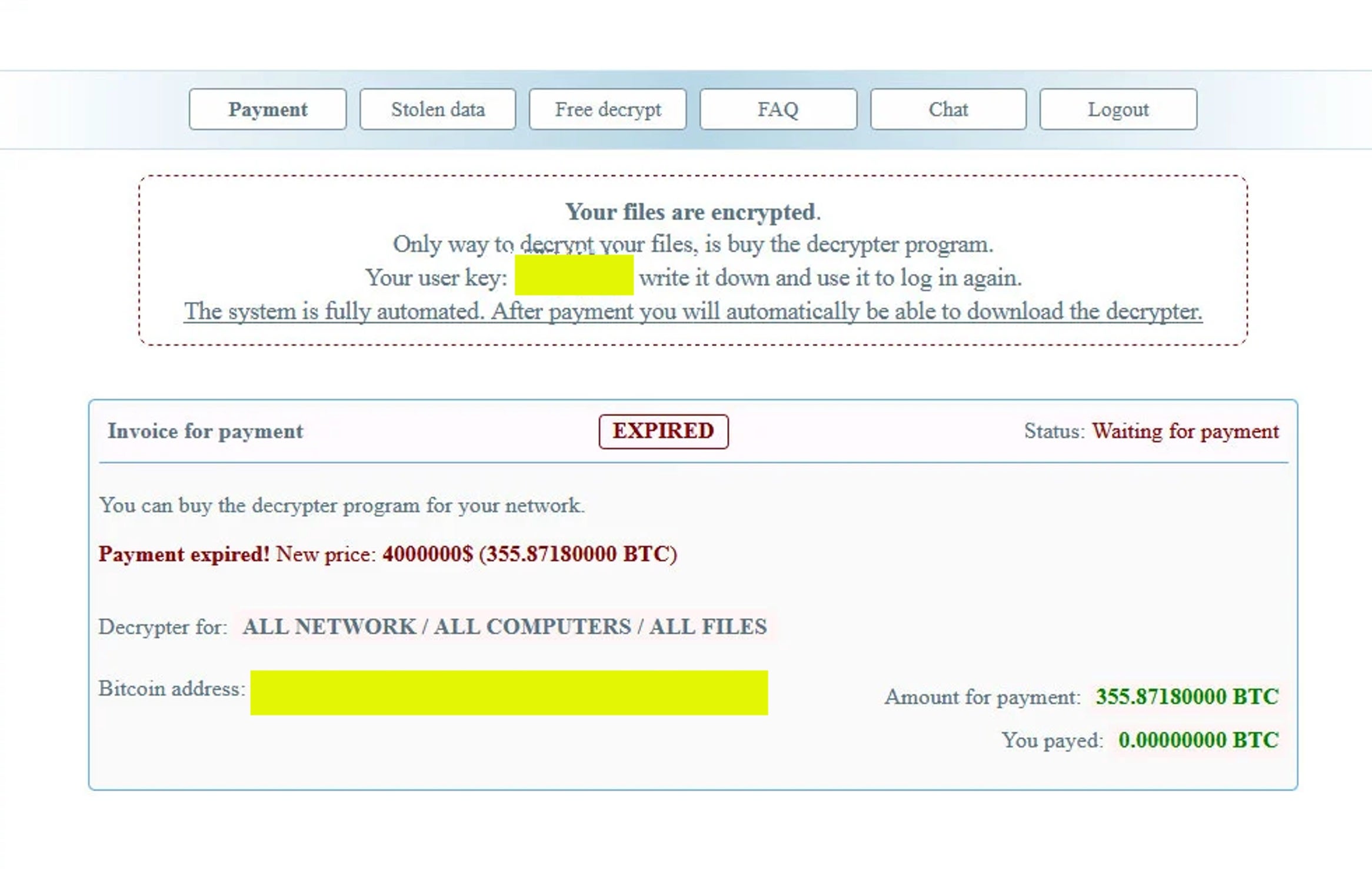
The payment page obtained on the Netwalker site shows that the ransomware operator initially requested a ransom of $2 million. After 7 days, the ransom was increased to $4 million U.S. dollars, or about 355 Bitcoin.
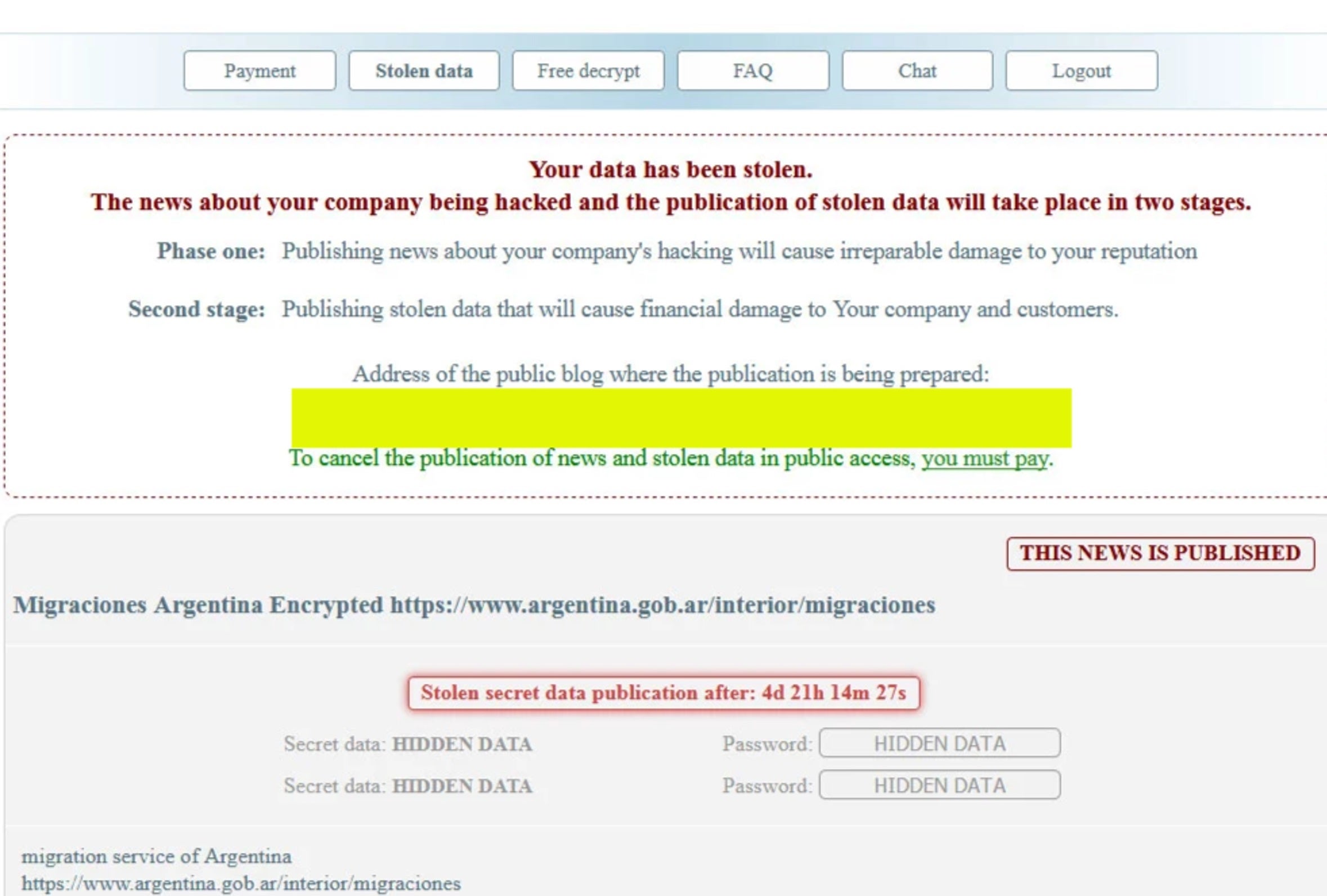
The website also includes a "stolen data" page that shows screenshots of data stolen from "Migraciones Argentina" during the attack.
Conclusion
Although ransomware attacks against cities and local institutions have become commonplace, this incident may be the first known and noteworthy attack on a government agency that disrupts operations in a country.
Sangfor Ransomware Solution
Sangfor's Security Solution for Ransomware provides a holistic solution to stop ransomware attacks in real-time. The solution is robust enough to block every step in the ransomware Kill Chain, but modular enough to be tailored to any organization.
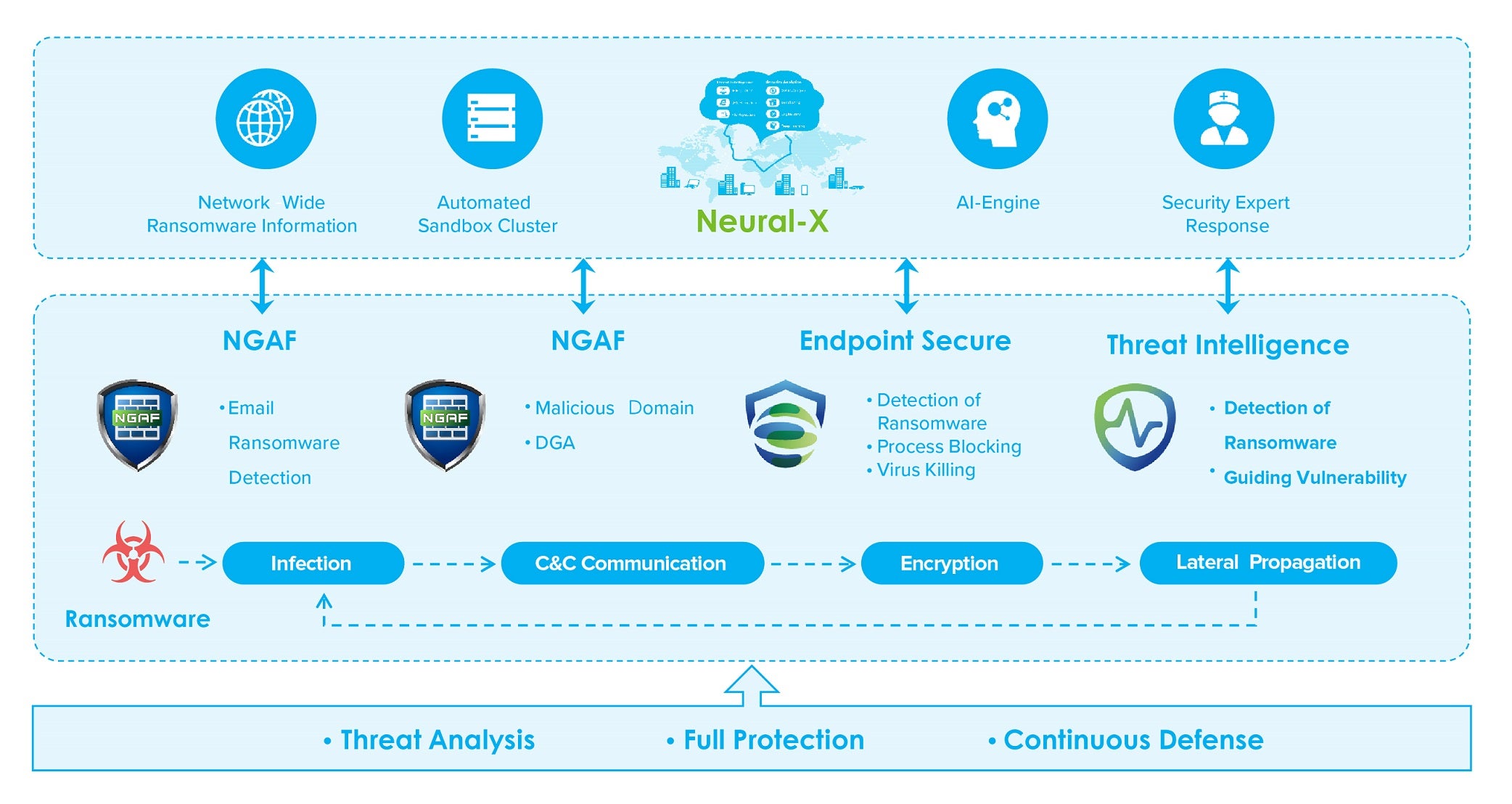
Cloud (Neural-X)
• Cloud Monitoring Service: Detecting existing exploits or vulnerabilities like RDP port exposure, deserialization vulnerabilities and Eternal Blue Vulnerabilities.
• Cloud Threat Intelligence: Pushing the latest ransomware intelligence.
Next Generation Firewall (NGAF)
• Deploy Border Security Devices: Block WEB exploits/RDP brute force attacks.
• Configure Protection Device to Associate with the Cloud Reputation: Directly block outbound C&C host behavior and malicious file downloads, based on IP/file reputation.
Sangfor Endpoint Secure
• Early detection of vulnerable points that are easily exploited by ransomware.
• Scan the terminal directory regularly to check if ransomware has been inserted.
• Real-time, AI-powered analysis of ransomware behavior.
• Immediate isolation of infected hosts to avoid widespread infection.
Sangfor Cyber Command
• Link network and terminal data to jointly analyze suspicious behavior, monitor in real-time and provide early warning of any threats.
Ransomware Protection Video
Watch a video of a simulated ransomware attack triggered by a phishing email and see how the Sangfor Cloud-Firewall-Endpoint integrated solution can protect your organization against each step of the ransomware kill chain!
SECURE YOUR NETWORK BY CONTACTING US NOW





