What is Cyber Threat Hunting?
Essentially, cyber threat hunting refers to the proactive search for cyber threats or vulnerabilities that could leave your IT infrastructure vulnerable to attack. Cyber threat hunting seeks out any threats that may have made it past your system’s baseline cybersecurity. The cyber threat hunter will then find any concealed threats even if they are unknown, unresolved, or undetected.
Traditionally, threat-hunting solutions relied solely on the skills and time of security analysts and other cybersecurity professionals. However, those skills are now in high demand due to a lack of qualified technicians with the required experience, education, and instincts. This fact has made cyber threat hunting difficult and time-consuming. The expected human error involved also makes threat-hunting solutions less effective.
These days, hackers are just as sophisticated as the professionals trying to stop them. This forces companies to evaluate threat actor intentions and capabilities while monitoring for vulnerabilities – without any threat-hunting security tools or skills. However, a few open-sourced and commercially available threat-hunting tools can serve as effective threat-hunting solutions.
Why Cyber Threat Hunting is Important?
Cyber-attacks are growing more sophisticated and cybercriminals don’t rest. While most of your automated cybersecurity can securely deal with threats, they are not entirely foolproof. This is because cyber-attacks continue to evolve - becoming smarter and harder to detect. Given enough time and resources, these modern threats can break past most automated defense solutions.
Modern malware and viruses can also lay dormant within a network and go undetected for days when using typical cybersecurity protocols. Joseph Ochieng’s study revealed that cybercriminals can spend almost 192 days in a system on average before being discovered. This leaves your entire system open to ongoing damage from the inside. A cyber threat-hunting tool can act as a stealthy hunter catching these files unawares.
According to IBM's "Cost of a Data Breach Report" in 2023, the average cost of a data breach was estimated at US$ 4.45 million. Companies can no longer afford to be simply reactive in their approach to cyber threats. Effective cyber threat hunting helps organizations understand the areas of their cybersecurity that need extra attention. This will ultimately reduce the potential damage that can be done - which is a lot.
Objectives of Cyber Threat Hunting
The best way to determine which cyber threat hunting platform is suited to your business needs is to evaluate the potential attacker’s goals, capabilities, and opportunities.
- Goals: The type of data you collect and store, the size of your enterprise, and the amount of money that flows through your business daily are indicators of your level of risk and the types of threats your system is vulnerable to. Determine if a cyber-attack will target your customers, or finances, or try to hold operations for a ransom. This will help you to measure the methods of attack you will likely experience. Formative threat-hunting solutions will prioritize this detection.
- Capabilities: Staying updated on the latest cybersecurity trends will help your threat-hunting platform understand what attacks might be launched against your network. For example, if you know that your most valuable company asset is customer PII, you should research the latest and most successful cyber-attacks aimed at the theft of customer information. This will give you a head start in identifying security gaps in your network.
- Opportunities: Closing the door to known and unknown threats before they can be used against you is an important way of proactively protecting your network. Being a victim of the same cyber-attacks as other companies gives your customers the view that your company lacks awareness and is not prepared. This passive commitment to network security is bad for your brand in general. However, maintaining effective cyber threat hunting will reduce the likelihood of that.
Threat Hunting Process: How Threat Hunting Works
Effective cyber threat hunting is a strategic and systematic process designed to detect and mitigate threats that have evaded traditional security defenses. This process typically involves three key steps:
Trigger
The process begins with a trigger, an alert that directs cyber threat hunters to a specific system or network segment for further investigation. Advanced detection tools identify unusual activities that could indicate malicious behavior. Often, the trigger comes from a hypothesis about a new or evolving threat, prompting a proactive search for potential adversaries.
Investigation
In this critical phase, threat hunters operate under the assumption that adversaries are already present within the network. Their task is to identify and confirm potential threats through detailed data analysis and behavioral examination. The investigation typically falls into three main categories, hypothesis-driven investigation, IOC-based investigation and advanced analytics and machine learning.
Resolution
Upon identifying anomalies, skilled analysts conduct thorough investigations to uncover stealthy threats. This phase relies heavily on human expertise, combining threat intelligence resources with advanced security technologies to protect the organization's systems and information proactively. In cases where the threat is significant, there may be an escalation to specialized teams as part of a comprehensive communication and action plan.
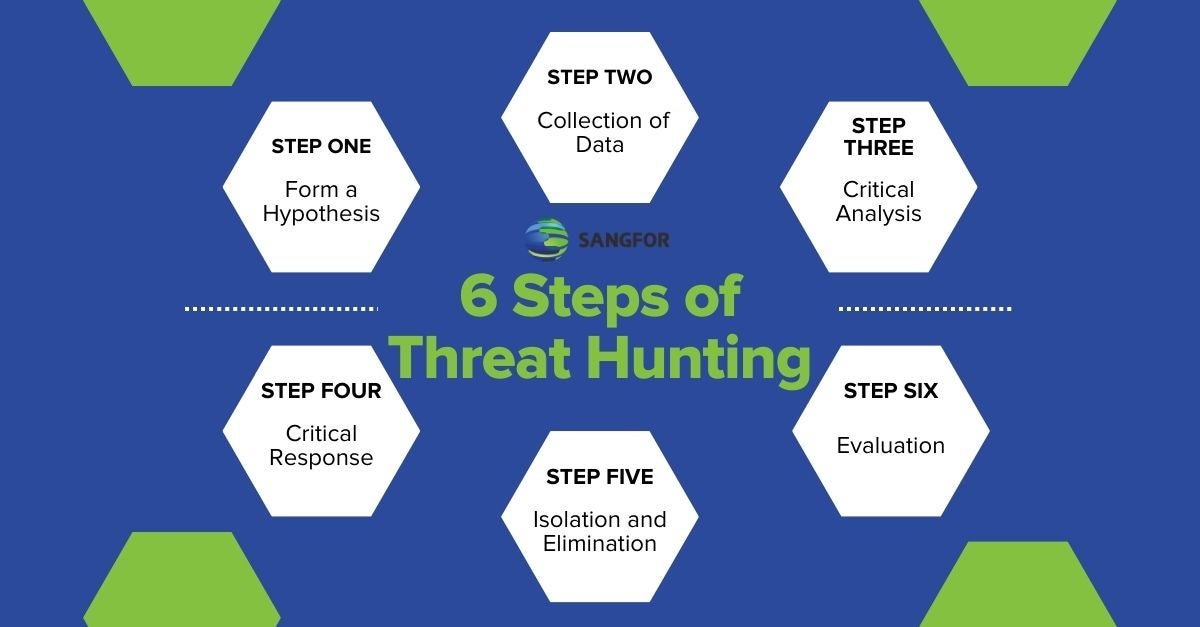
Six Steps of Threat Hunting
There are specific threat-hunting steps that can be taken to find an actual threat. These steps can be sorted into the following six simple steps as follows:
Step One: Form a Hypothesis
This is where threat hunters will establish what type of threat they’re looking for. The hypothesis will be informed by analysis of previous malware attacks, trends in cybersecurity attacks, and critical areas of attack. Threat hunters must make use of threat-intelligent techniques to locate and develop a plan of action. This step is where your cyber threat-hunting goal is set.
Step Two: Data Collection
Threat hunting cannot be done without a sufficient amount of data collection. In step 2, your cyber hunter needs to establish centralized and organized data. Cyber threat hunting should also be built on the data of previous threat-hunting exploits. This ensures that threat hunting is continuous and that only the relevant data is used to critically analyze threats. Threat hunters can then use the data collected to determine if the hypothesis is worth expanding on.
Step Three: Critical Analysis
This step of the process is crucial and will provide the data needed to mitigate potential threats. Patterns and processes must be carefully monitored for anomalies and suspicious behaviors. As more analysis takes place, your threat-hunting team also learns new tactics and develops its threat-hunting capabilities.
Step Four: Critical Response
Time is of the essence when threat hunting and a rapid response is necessary to ensure your network’s safety. The response needs to consider both long-term and short-term measures to prevent and mitigate the threat. This includes disabling users, implementing security patches, blocking IP addresses, updating authorization privileges, altering network configurations, or introducing new identification requirements. The main goal of threat hunting is to protect the host, prevent system damage, and eliminate the possibility of a future attack.
Step Five: Isolation and Elimination
This step sees the threat dealt with in isolation to prevent further damage to the network. Using advanced threat detection sandboxing techniques will make sure that suspicious malware is quarantined away from other files. This will reduce the risk of damage to the server and automatically mitigate the threat.
Step Six: Evaluation
The last step of the process involves understanding the threat-hunting techniques and practices vital to your business. The evaluation also means implementing stricter controls over areas in your network that are vulnerable to cyber-attacks. This allows your IT team to predict and proactively safeguard your network before any damage can be done. The best threat-hunting tool is preventative measures.
Once these steps are involved, your threat-hunting team will be ready to fight off malware, but there are more threat-hunting tools and techniques that you can use.
What’s Required to Start Threat Hunting Program?
- The Team of Cyber Threat Hunters: This security team with expertise forms the foundation. The team needs a deep understanding of cybersecurity concepts, including network security, operating systems, and common attack vectors. Key skills include analytical skills and problem-solving skills. Strong analytical skills are crucial to identify patterns, anomalies, and potential indicators of compromise (IOCs). With problem solving skills, threat hunters need to formulate hypotheses, investigate leads, and develop effective remediation strategies.
- Repository of Data: Organizations should have a central repository for security data from various tools like SIEM (Security Information and Event Management) and EDR (Endpoint Detection and Response). This allows for comprehensive analysis and correlation of events across the network. In addition, comprehensive visibility into network traffic and endpoint activity is essential to detect suspicious behavior.
- Threat Intelligence: Enterprises can subscribe to reputable threat feeds that provide up-to-date information on attacker tactics, techniques, and procedures (TTPs). This knowledge helps one tailor the hunting process to focus on the most relevant threats. Moreover, staying informed about the latest vulnerabilities affecting one’s systems and applications should be a priority.
Difference Between Threat Hunting and Threat Intelligence
|
Aspect |
Threat Hunting |
Threat Intelligence |
|---|---|---|
|
Definition |
Proactive search for threats within an organization’s environment |
Information about existing and emerging threats that could affect an organization |
|
Goal |
Identify and neutralize active threats |
Understand the threat landscape |
|
Approach |
Proactive, searching for threats |
Reactive, collecting and analyzing information |
|
Focus |
Internal security posture, detecting hidden or active threats |
External threat landscape, trends, and attacker tactics |
|
Tools |
SIEM (Security Information and Event Management), EDR (Endpoint Detection and Response), forensic tools |
Threat intelligence platforms, data feeds, analytics tools |
|
Outcomes |
Detection of malicious activity, identification of compromised systems and recommendations for remediation |
Contextual understanding of threats, improved security posture and prioritization of defensive measures |
Cyber Threat Hunting Methodologies
Threat hunting methodologies encompass various approaches and techniques used to proactively search for and detect cyber threats within a network. It's important to note that these methodologies often work in tandem, and threat hunters may employ a combination of approaches depending on the specific needs and goals of an organization. Here are some common threat hunting methodologies as described in the provided resources:
- Hypothesis-driven investigation. This methodology involves formulating hypotheses about potential threats based on known attack patterns, threat intelligence, or suspicious indicators. Threat hunters then investigate the network to validate or refute these hypotheses. By leveraging crowdsourced attack data and insights into attackers' tactics, threat hunters can identify and respond to emerging threats.
- Investigation based on known Indicators of Compromise (IOCs) or Indicators of Attack (IOAs). Threat hunters leverage threat intelligence to catalog and analyze known IOCs and IOAs associated with new threats. These indicators serve as triggers to uncover hidden attacks or ongoing malicious activities. By proactively searching for these indicators, threat hunters can detect and mitigate threats before they cause significant damage.
- Advanced analytics and machine learning investigations. This methodology combines data analysis and machine learning algorithms to sift through large volumes of information and identify anomalies that may indicate potential malicious activity. Skilled analysts investigate these anomalies to uncover stealthy threats. By using advanced analytics and machine learning, threat hunters can detect sophisticated attack techniques that may evade traditional security defenses.
Threat Hunting Maturity Model
The threat hunting maturity model is a framework that helps organizations assess their level of readiness and effectiveness in conducting threat hunting activities. It consists of five levels, with each level representing a different stage of maturity in threat hunting capabilities. The levels range from ad-hoc and reactive to proactive and automated.
- Level 0: At the ad-hoc level, organizations have no formal threat hunting program in place and only respond to threats as they arise.
- Level 1: There is a basic reactive threat hunting program in place, but it is not consistent or proactive.
- Level 2: The proactive level involves a more structured and strategic approach to threat hunting, with dedicated resources and processes in place.
- Level 3: Advanced level threat hunting incorporates automation and machine learning to enhance the effectiveness and efficiency of threat hunting activities.
- Level 4: When threat hunting procedures have been optimized, it is integrated into the overall security strategy and continuously evolves to stay ahead.
Tools and Techniques Used for Cyber Threat Hunting
Cybersecurity experts use critical thinking, manual forensic investigation, and automated threat-hunting tools to protect companies. Threat hunters seek out insider threats and outsider attack surfaces to hunt down potential attackers or vulnerabilities before they can become a problem. This is done by executing a well-rehearsed incident response (IR) plan.
A few critical elements of any cyber threat-hunting mission are:
- Data analytics and reporting
- OS and network knowledge
- Information security experience
Evolved Cyber Threat Hunting Techniques
Cyber threat hunting today has evolved from more traditional and manual methods. Thanks to advancements in technology, we can threat hunt more effectively and efficiently. Coupled with advances in automation, machine learning, and behavior analytics, cyber threat hunting is imperative to an organization’s cybersecurity strategy. Here are some core techniques used today:
- Baselining: As its name suggests, this technique helps threat hunters understand what a normal baseline IT operation looks like within an organization. This acts as a baseline for comparison when threats are possible. Baselining is critical as it helps establish a clear difference between malicious and non-malicious events to identify anomalies.
- Attack-Specific Hunts: Unlike baselining - where the overall environment is analyzed - this technique focuses on a threat actor or threat alone. This helps threat hunters find malicious activity faster. Attack-specific hunts can often be limiting, however, which is why they are often used in conjunction with baselining to get better results.
- Time Sensitivity: Threat hunting is generally constrained by time. Time is valuable when protecting against malicious attacks. Threat hunters should validate their baseline terms and data periodically to keep up with the rapid pace of hackers.
- Help from Third-Party Sources: Threat hunting can be an overwhelming process because of the sheer number of threats and data that need to be analyzed. Getting some help ensures your organization is better protected. These third-party sources can also help with geolocation, encrypted traffic metadata, ruling out false positive leads, and more.
Threat Hunting Investigation Types
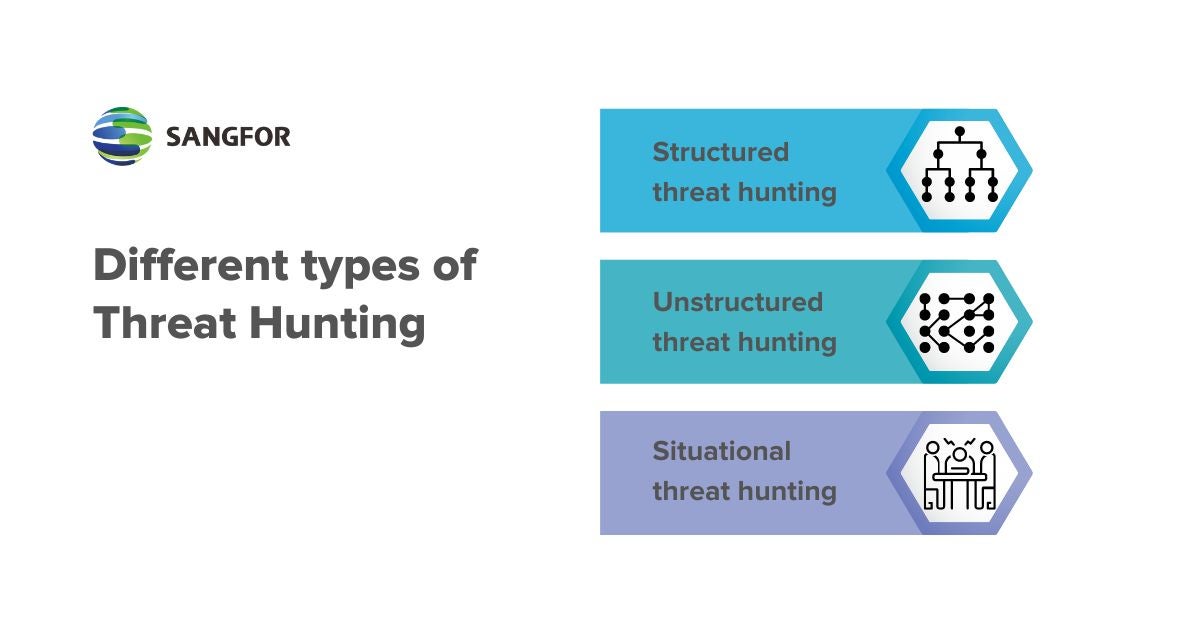
Threat-hunting techniques differ in organizations, industries, and environments. However, many of the core threat-hunting strategies remain mostly the same. The main three types of cyber threat hunting include:
- Structured threat hunting: This type of threat hunting is more organized. It is based on an indicator of attack and tactics, techniques, and procedures of an attacker. This method allows you to gain a better understanding of the techniques used by attackers. Structured threat hunting is usually based on previous methods of attacks found which means that it’s driven by a particular technique.
- Unstructured threat hunting: An unstructured threat hunt is primarily based on indicators of compromise. These hunts are initiated based on a trigger. The trigger then pushes threat-hunting programs to look for pre- and post-detection behavior.
- Situational threat hunting: A situational threat hunt comes from an internal risk assessment of the vulnerabilities of a specific organization - unique to its IT environment. This type of cyber threat hunt involves uniquely generated data from previous attack assessments to check if a similar situation might repeat itself.
Challenges of Cyber Threat Hunting
As cyber threat hunting is a proactive activity - that not many are familiar with - it may come with challenges. Here are some of the common challenges of cyber threat hunting:
- Lack of Skilled Hunters. While threat-hunting solutions have evolved, there is still a human element to the methods. Hiring skilled cyber threat hunters who can use the tools, techniques, and software better can be difficult with the current gap in cybersecurity talent in the industry.
- Gathering Wrong or Poor Data. To identify hidden cyber threats and keep watch over a network, it’s essential to have the right security data in the first place. Having poor data will waste time and resources - leading to inefficient results.
- Using Outdated Threat Intelligence. Threat hunters need to be equipped with the latest and most accurate cyber-attack tactics, techniques, and procedures. It is vital to generate an effective threat-hunting hypothesis model and threat intelligence. This allows threat hunters to better analyze attack trends and protect the organization.
What to look for in a Cyber Threat Hunter Solution
By considering the following elements, organizations can select a cyber threat hunter solution that effectively detects and mitigates cyber threats, enhances their security posture, and supports proactive threat hunting activities.
- Advanced Detection Capabilities: Your solution should have advanced detection capabilities to identify sophisticated and evasive threats that may bypass traditional security tools. It should employ a combination of behavioral analytics, machine learning, and threat intelligence to detect unknown threats and anomalies.
- Real-time Monitoring and Alerting: Being able to react quickly means that your solution should provide real-time monitoring of network traffic, logs, and endpoints, detecting and alerting on potential threats as they occur. In addition, it should have the ability to generate actionable alerts with relevant context to facilitate timely response and investigation.
- Comprehensive Data Collection and Analysis: Choose a solution that collects and analyzes a wide range of data sources, including network traffic, logs, system events, and endpoint telemetry. It should be capable of correlating and analyzing this data to identify patterns and indicators of compromise.
- Threat Intelligence Integration: Integration with external threat intelligence feeds is crucial to enrich the analysis and detection capabilities of the solution. It should have the ability to consume and leverage threat intelligence feeds to identify known malicious indicators and detect emerging threats.
- Hunting Techniques and Tools: A good threat hunter solution should provide a range of hunting techniques and tools to proactively search for potential threats. It should support both manual and automated hunting techniques, allowing analysts to conduct in-depth investigations and leverage advanced analytics for efficient threat hunting.
- Collaboration and Reporting Capabilities: Your solution should facilitate collaboration among security teams and stakeholders. It should provide a centralized platform for sharing findings, collaborating on investigations, and generating reports to communicate the results of threat hunting activities.
- Scalability and Flexibility: When choosing a cyber threat hunter solution, you should consider how scalable the solution is to handle the volume and velocity of data in large enterprise environments. Your solution should be flexible enough to adapt to evolving threats and support customization based on specific organizational requirements.
- Integration with Security Infrastructure: Seamless integration with existing security infrastructure is essential for effective cyber threat hunting. Your solution should be able to integrate with SIEM (Security Information and Event Management), EDR (Endpoint Detection and Response), and other security tools to leverage their data and enhance detection and response capabilities.
- User-Friendly Interface and Workflow: Your solution should have an intuitive and user-friendly interface that enables efficient navigation, investigation, and reporting. It should provide clear visualizations and contextual information to aid analysts in understanding and prioritizing threats.
- Vendor Support and Expertise: When choosing your solution, consider the vendor's reputation, experience, and support capabilities. Look for a vendor with a strong track record in the cybersecurity industry and a commitment to ongoing research and development.
Professional Cyber Threat Hunting: Sangfor’s Cyber Command
Professional threat hunting platforms and vendors are the most reliant when it comes to protecting your business from cyber-threats. These expert threat hunting capabilities provide encompassing protection from stable and secure vendors who make it their priority to ensure your data is safe.
Sangfor’s Cyber Command is real-time threat intelligence, detection and response platform designed with the singular purpose of improving enterprise IT security and risk posture and presents several advantages when considering a threat hunting platform solution for your enterprise. Threat-hunting cybersecurity platforms and vendors are the most reliable when it comes to protecting your business from cyber threats. Their expert threat-hunting capabilities provide encompassing protection. A stable and secure vendor will make it their priority to ensure that your data is safe. Sangfor Technologies is proud to be a leading cybersecurity provider capable of that and so much more.
Sangfor’s Cyber Command is a real-time threat intelligence, detection, and response platform. Designed with the singular purpose of improving a company’s IT security and risk posture, it has several advantages for your threat-hunting needs:
- Cyber Command Is a Fully Integrative System. Being able to integrate with existing software and multiple other cybersecurity and cloud-compatible products allows Cyber Command to be accessible and easy to deploy within your network.
- Secure Access. While most open-source threat-hunting tools can be deemed sketchy and unstable, Cyber Command provides reliable and secure protection for your data from a professional perspective. This gives you peace of mind knowing that your network is in good hands.
- Ease of Operation. The Cyber Command platform offers simplified operation and a holistic view of your entire network through an easily navigable dashboard. Sangfor also provides expert teams on-hand for additional support whenever you need it.
- Cost Efficient. Lastly, we know that the main reason open-source threat-hunting is favored over professional vendors is the implied cost of an expert threat-hunting platform. Sangfor seamlessly eases those worries by providing the most advanced and encompassing cybersecurity without breaking the bank.
Sangfor Cyber Command is used and trusted by customers worldwide to significantly improve threat detection and response. You don’t have to only take our word for it though, just read some of the success stories of the Cyber Command platform from our esteemed clients:
- The Azienda Socio Sanitaria Territoriale (ASST) Lariana is an established healthcare provider in the Province of Como, Italy. Sangfor Cyber Command gave the healthcare providers 360-degree visibility of the network to ensure cybersecurity.
- Naquadria S.r.l. is a reliable internet service provider and data center based in Piacenza, Italy. Sangfor’s Cyber Command NDR (Network Detection and Response) solution provided Naquadria with a reliable and advanced control and response center for all threats that plagued the exposed systems - including the web and mail servers.
Watch this introduction video to learn how Cyber Command provides elite and advanced threat detection and cybersecurity for your enterprise.
Frequently Asked Questions
Threat intelligence is a data set about attempted or successful intrusions, usually collected and analyzed by automated security systems with machine learning and AI. Threat hunting, on the other hand, is a proactive approach to identifying previously unknown or ongoing threats within an organization's network. It uses threat intelligence as a starting point, but goes beyond it by conducting a thorough, system-wide search for bad actors. While threat intelligence focuses on data and analysis, threat hunting involves skilled IT security professionals manually searching, monitoring, and neutralizing threats before they can cause significant damage. Additionally, threat hunting can uncover threats that have not yet been identified by automated systems, making it a crucial component of a comprehensive cybersecurity strategy.
Reacting to cyber threats alone is insufficient because it introduces a time gap between the occurrence and detection of threats, allowing attackers to cause damage. Reactive measures often rely on known attack patterns and may miss new or sophisticated threats. Advanced Persistent Threats (APTs) and insider threats, which are designed to evade detection, require proactive monitoring and analysis.
By implementing proactive threat hunting, you enable early detection and mitigation of threats, reducing dwell time and potential impact. Proactive threat hunting also provides organizations with better visibility into their security posture, enhances incident response capabilities, and fosters continuous improvement. By combining proactive threat hunting with reactive measures, organizations can stay ahead of evolving threats and better protect their systems and data.





