Introduction
Spring Framework is a lightweight open-source application framework for developing enterprise Java applications. It helps developers create high performance, easily testable, and reusable code.
Summary
Sangfor security team received a notice about a remote code execution vulnerability in the Spring Framework, named SpringShell and classified as critical.
The vulnerability impacts Spring MVC and Spring WebFlux applications running on JDK 9+. The specific exploit requires the application to run on Tomcat as a WAR deployment. If the application is deployed as a Spring Boot executable jar, i.e., the default, it is not vulnerable to the exploit. However, the nature of the vulnerability is more general, and there may be other ways to exploit it.
The exploitation of this vulnerability could result in a webshell being installed onto the compromised server that allows further command execution.
NOTE: Palo Alto Unit 42 has reported that an exploit for this vulnerability has been seen in the wild.
Impact
Spring Framework is a very popular Java development framework. There are millions of applications on the internet that were developed using the Spring Framework.
Affected versions:
- Spring Framework 5.3.X < 5.3.18
- Spring Framework 5.2.X < 5.2.20
- Note: Other older versions are also affected.
Provided by Spring Framework
Spring Framework 5.3.18 and Spring Framework 5.2.20 are two secure versions (as of March 31)
Solutions
Remediation Solution
1. Check the component version
Option 1
Search the system for spring-beans. If spring-beans-{version}.jar exists, and the field inside the <version> tag is less than 5.3.18 or 5.2.20, it may be affected by the vulnerability.
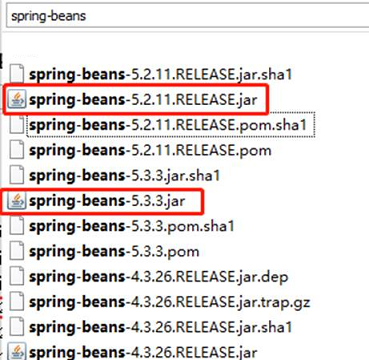
Option 2
If the project is compiled using Maven, there will usually be a pom.xml in the root directory of the project.
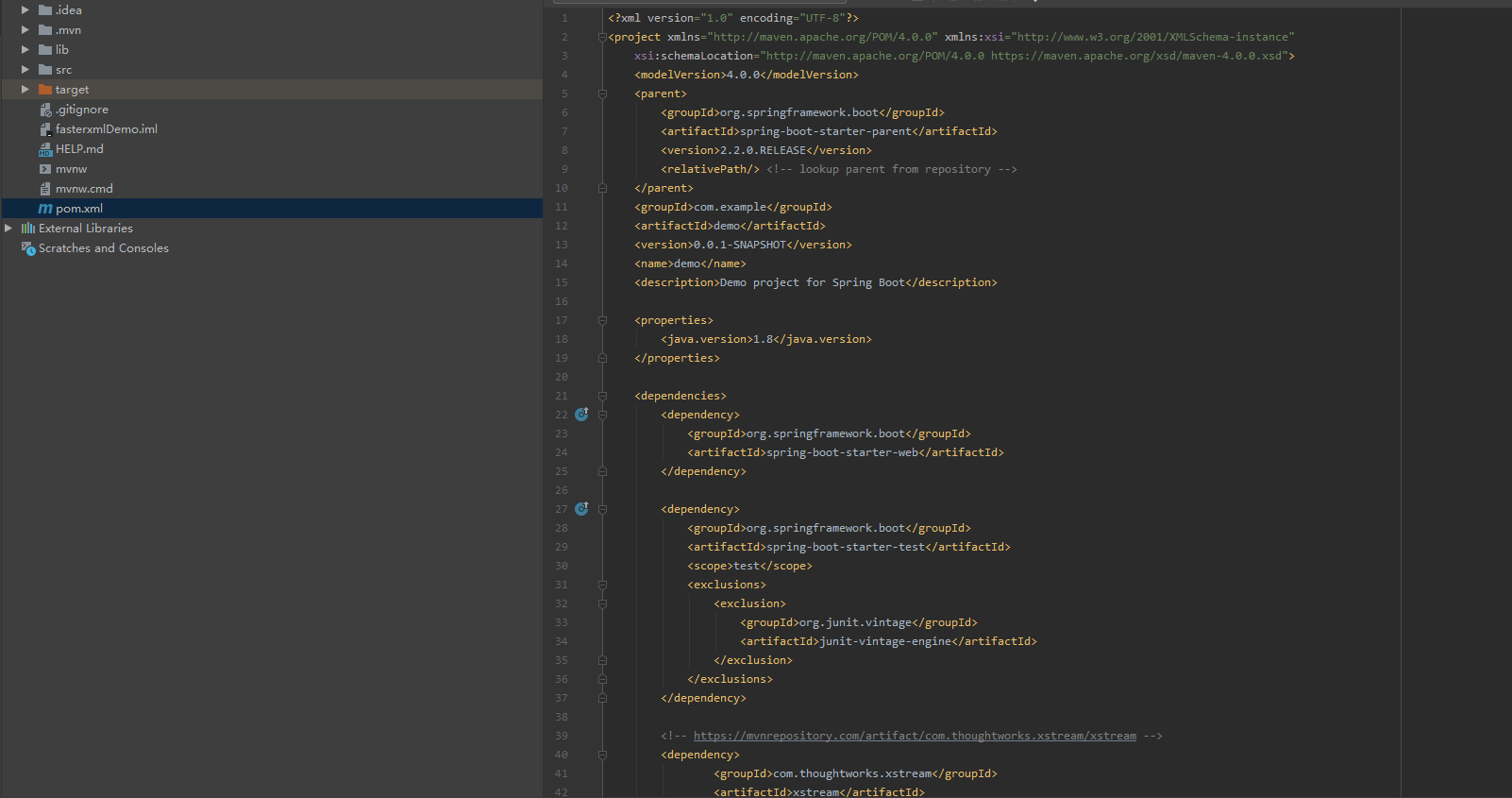
Open the pom.xml file, as shown below:
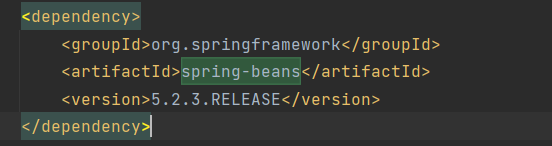
Search for spring-beans in this file. If the spring-beans is found, and the field inside the <version> tag is less than 5.3.18 or 5.2.20, it may be affected by the vulnerability. (The version of spring-beans in the image is 5.2.3, which may be affected by the vulnerability.)
However, if spring-beans is not found, it does not prove definitively that Spring Framework is not used.
2. Spring Framework Solution
Spring Framework has released a new version to fix this vulnerability. Affected users can download it from the following link:
https://github.com/spring-projects/spring-framework/tags
Note: Spring Framework 5.3.18 and Spring Framework 5.2.20 are two secure versions officially provided by Spring (as of March 31)
1. Workaround
This workaround does not fix the issue completely. Users can decide whether to adopt the solution based on their business needs.
Perform the following steps:
1. Perform a full search for the @InitBinder annotation in the application to see if the dataBinder.setDisallowedFields method is called in the method body. If the introduction of this code snippet is found, add {"class.*","Class.* to the original blacklist ","*.class.*", "*.Class.*"}. (Note: If this code snippet is used a lot, it needs to be appended everywhere.)
2. Create the following global class under the project package of the application system, and make sure that this class is loaded by Spring (it is recommended to add it in the package where the Controller is located). After the class is added, the project needs to be recompiled and packaged and verified for functionality. Finally, republish the project.
import org.springframework.core.annotation.Order;
import org.springframework.web.bind.WebDataBinder;
import org.springframework.web.bind.annotation.ControllerAdvice;
import org.springframework.web.bind.annotation.InitBinder;
@ControllerAdvice
@Order(10000)
public class GlobalControllerAdvice{
@InitBinder
public void setAllowedFields(webdataBinder dataBinder){
String[]abd=new string[]{"class.*","Class.*","*.class.*","*.Class.*"};
dataBinder.setDisallowedFields(abd);
}
}
Note: On the running server of the business system, run the "java -version" command to check the running JDK version. If the version number is less than or equal to 8, it is not affected by the vulnerability, as shown below:
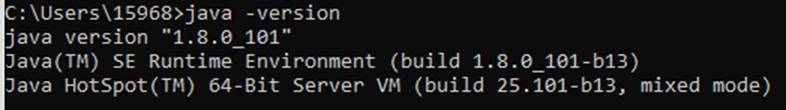
The JDK version found in the above is 8, which is not affected by the vulnerability.
Sangfor Solutions
No Sangfor product or service uses the Spring Framework and thus none of our products or services are affected by this vulnerability
- Sangfor NGAF customers, please update NGAF security protection.
- Sangfor Cyber Command detects attacks which exploit this vulnerability, and alerts users in real time. Users can correlate Cyber Command with Sangfor NGAF to block the attackers’ IP address.
About Sangfor NGAF:
Sangfors NGAF is a Next Generation Firewall that can effectively deal with vulnerability scanning, SQL injection attacks, website defacement attacks, brute force attacks to crack weak passwords and can effectively identify and interpret high-risk user behavior.
About Cyber Command:
Sangfor Cyber Command is an advanced Network Detection and Response (NDR) platform that significantly improves overall security detection and response capabilities by monitoring internal network traffic & correlating existing security events, applying AI and behavior analysis, all aided by global threat intelligence.
Timeline
- On Mar 29, 2022, Sangfor FarSight Labs received a notice about the Spring Framework remote code execution vulnerability.
- On Mar 31, 2022, Sangfor FarSight Labs released a vulnerability alert with remediation steps and solutions.
Reference
https://spring.io/blog/2022/03/31/spring-framework-rce-early-announcement
Learn More
Sangfor FarSight Labs researches the latest cyberthreats and unknown zero-day vulnerabilities, alerting customers to potential dangers to their organizations, and providing real-time solutions with actionable intelligence. Sangfor FarSight Labs works with other security vendors and the security community at large to identify and verify global cyberthreats, providing fast and easy protection for customers.





