What Is a Hardware Firewall?
A hardware firewall, also known as a firewall appliance or physical firewall, is a physical device that is installed between a private computer network and the internet to monitor and filter incoming and outgoing network traffic using defined rules and policies. Newer next generation hardware firewalls also integrate additional security features such as antivirus, threat prevention, and intrusion prevention systems for enhanced protection.
A hardware firewall is an essential network security solution for organizations looking to protect their enterprise network from malicious traffic and cyber-attacks through effective threat prevention.
Examples of Hardware Firewall
Hardware firewalls can be recognized and categorized as either stateful or stateless. Stateless hardware firewalls, such as packet filtering firewalls, make decisions based on individual data packets, such as IP addresses and port numbers; they don’t store any information about the state of the network connection; thus, they have limited capability in detecting internet threats and attacks. However, they can handle large loads of traffic with speed and robust performance despite this limitation.
On the other hand, stateful firewalls monitor the state of active connections and make decisions based on the context of the traffic, offering better security features for corporations. Stateful inspection firewalls are a common type of stateful firewalls, keeping track of the traffic state while analyzing the data within packets to detect malicious code. Next generation firewalls are a relatively new type of stateful firewall, providing features and functionalities beyond what conventional stateful firewalls are capable of. They are capable of detecting and blocking more sophisticated attacks by enforcing security policies at the application, port and protocol levels.
How Do Hardware Firewalls Work?
Hardware firewalls are placed behind the router of an internet connection so that all incoming and outgoing traffic funnels through the firewall for inspection. Because of their position, hardware firewalls act as the first line of defense for a private network, providing essential threat prevention capabilities. They control what traffic enters and leaves the network based on defined rules and policies. Security administrators can configure hardware firewalls with granular firewall rules and policies to control the data flowing to and from specific IP addresses, ports, applications, services, devices and users.
Newer hardware firewalls integrate an intrusion detection system (IDS)and threat prevention mechanisms to identify suspicious traffic that indicates a network breach. By filtering out unauthorized traffic and detecting suspicious behavior, hardware firewalls protect enterprise networks from malware and cyberattacks.
Difference Between Software and Hardware Firewalls
Hardware firewalls are physical devices that are placed in a central position to filter traffic for the entire network or a network segment. Software firewalls, or host firewalls, are software applications that only filter traffic for the device they are installed on.
Because hardware firewalls work using their own components, they deliver superior traffic filtering performance and support enhanced security features. Software firewalls rely on the system resources of the device they are installed on. As a result, they tend to reduce operating system performance and have limited capabilities.
Despite the advantages of hardware firewalls over software firewalls, it’s good practice to use both. If threats manage to evade the hardware firewall, software firewalls can act as a second line of defense.
What is a Next Generation Firewall (NGFW)?
You may have heard of a type of firewall called “next generation firewall” (NGFW) and wondered what it is. A next-generation firewall is the name given to newer, more advanced firewalls. NGFWs are invariably hardware firewalls due to the computing resources needed to support their range of security features. NGFWs perform the same traffic filtering function of traditional hardware firewalls but also integrate additional security capabilities, such as antivirus, intrusion detection and intrusion prevention, application control, threat prevention, sandboxing, and more.
Who Needs a Hardware Firewall or Firewall Appliance?
Hardware firewalls are being widely adopted in a range of different scenarios including:
- Businesses that require advanced security and greater reliability to protect a network of computers and servers.
- Businesses that currently don't have the means to centrally manage software firewalls on a large number of network devices.
- Businesses that currently experience poor computing performance due to software firewalls consuming too many resources.
- Businesses that wish to save costs and operational complexity by having multiple security capabilities in one firewallappliance instead of deploying multiple layers of security tools.
- Businesses that wish to save on the amount they currently spend on software firewalls in the long term.
- Businesses that have the personnel and know-how to operate and maintain a hardware firewall.
Why Do We Need a Physical Firewall?
With the ever-growing array of cyber threats that can compromise sensitive data and disrupt operations. A hardware firewall becomes an indispensable asset for several key reasons:
- It provides a single point of control for monitoring and protecting all network traffic so businesses can implement consistent security policies across the organization.
- With advanced features like threat prevention and deep packet inspection, a hardware firewall builds a superior defense against sophisticated cyberattacks for any enterprise, which are vital in protecting business assets.
- Specifically designed with the capability to handle high traffic volumes without slowing down network performance, hardware firewalls ensure business operations run smoothly, with minimal downtime.
- As businesses grow, hardware firewalls can be scaled to accommodate increased network demands, making them a future-proof investment for expanding enterprises.
- Operating independently from the company’s primary computing resources, it prevents the slowdown of critical business applications and systems.
- Centralized management capabilities allow for the easy implementation of uniform security policies and quicker response to security incidents, streamlining IT administration.
- VPN support ensures secure remote access for employees, an essential feature in the era of flexible work arrangements.
Benefits of a Hardware Firewall
Hardware firewall devices rely on hardware for information security, which has many benefits over software firewalls, including:
- High specifications enable hardware firewalls to process large bandwidths. This means that they can protect a large network with many users and devices and filter data packets much faster. This capability is particularly beneficial for businesses with high traffic volumes, ensuring no disruption to network performance.
- Hardware firewalls don’t consume the computing resources of endpoints because no software is installed. This ensures better performance for computing tasks. As a result, endpoints can operate more efficiently, focusing their resources on productive tasks rather than security processing.
- The placement of hardware firewalls enables centralized firewall management using a single console. This significantly simplifies operations and maintenance. It allows for a streamlined security protocol, making it easier to update and enforce policies across the entire network.
- Centralized management means that rules can be applied to every device and user on the network equally. This ensures that there are no loopholes in the network. Uniform policy application simply reduces the risk of security breaches, making the network environment more secure and safer through consistent threat prevention measures.
- Integrated security capabilities such as an intrusion detection system, antivirus, application control, and threat intelligence mean increased threat protection. These comprehensive security measures equip organizations to better detect and respond to a wide range of cyber threats.
- As more companies and enterprises embrace the hybrid working mode, a modern hardware firewall that enables VPN, such as NGFW, is essential in adapting to this increasing trend. Access to a virtual private network (VPN) connection provides remote and traveling employees secure access to the network by encrypting traffic to ensure data security.
- By employing advanced algorithms and security protocols on designated hardware, the firewalls can accurately distinguish between legitimate traffic and potential threats, blocking malicious activities before they can penetrate the network. This preemptive approach significantly lowers the risk of cyber attacks and malware infections.
- With significant network visibility, IT administrators are able to monitor network traffic in real time. This visibility is key to identifying and addressing potential security vulnerabilities. By having a comprehensive overview of the network's security landscape, organizations can proactively manage risks, minimize cybersecurity blind spots, and adapt their security strategies to counter emerging threats effectively.
Disadvantages of a Hardware Firewall
Despite their many benefits, hardware firewalls may come with several shortcomings that businesses need to be aware of before implementation. These include:
- The superior performance and advanced configuration of hardware firewalls, as opposed to their software firewalls, require a much higher cost. While they have enhanced capability to handle large volumes of traffic with powerful security measures, it comes at a significant financial cost.
- Apart from regular maintenance, hardware firewalls require constant updates and potential hardware replacements over time. Performing these activities translates into higher operational costs for businesses, as they need to either train their staff accordingly or outsource these services.
- Unlike software solutions that can be installed and managed with basic software operation skills, hardware firewalls require specialized technicians who have a deeper understanding of network infrastructure and firewall configuration. This need for specialized skill sets poses a challenge for organizations without an in-house IT department.
- Hardware firewalls generally are physical devices that require dedicated space within an organization's network infrastructure. This requirement can be a constraint for businesses with limited physical space or those aiming for minimalistic setups. The need to accommodate such devices may lead to the reorganization of server rooms or additional investments in infrastructure to ensure proper ventilation, power supply, and security for the hardware.
Emerging Trends in Hardware Firewalls and Threat Prevention
As cyber threats evolve, so do hardware firewalls and their threat prevention capabilities. Understanding these emerging trends can help organizations stay ahead in the cybersecurity landscape:
- Integration with Artificial Intelligence (AI): Modern hardware firewalls are increasingly incorporating AI and machine learning to enhance threat detection and response times. AI-powered analytics enable real-time identification of sophisticated cyber threats that traditional methods might miss.
- Cloud-Based Management: With the rise of cloud computing, hardware firewalls are now offering cloud-based management portals. This allows for centralized control and monitoring of multiple firewall appliances across different locations, simplifying administration and policy enforcement.
- Support for Internet of Things (IoT) Security: As IoT devices become more prevalent in corporate networks, hardware firewalls are adapting to provide specialized security measures. They can identify and monitor IoT devices, ensuring that these potential vulnerabilities are secured.
- Zero Trust Network Access (ZTNA): Hardware firewalls are embracing the zero-trust security model, which operates on the principle of "never trust, always verify." This trend enhances threat prevention by continuously validating every device and user attempting to access resources within the network.
- High-Speed Connectivity Support: With the advent of technologies like 5G and high-speed broadband, hardware firewalls are being designed to handle greater bandwidth without compromising security. This ensures that organizations can leverage high-speed connections while maintaining robust protection.
- Enhanced VPN Capabilities: As remote work becomes the norm, hardware firewalls are improving their VPN features to support secure and seamless connectivity for a distributed workforce. This includes better encryption standards and user authentication methods.
How to Choose a Hardware Firewall for Your Enterprise
When looking to invest in a hardware firewall, you should always start by following a few easy steps.
- Look into features: As with any big investment, thorough research is crucial to making the right choice that best fits your circumstances. If you were going to buy a car, you wouldn’t just buy any car - you would choose a car that works with both your lifestyle and your budget. It’s the same with your hardware firewall. Decide what types of features you can’t live without, and square that with your budget. A more in-depth discussion of hardware firewall features is provided in the next section.
- Look at existing customer reviews: Customer reviews are the best place to find the truth about a product or service. The Gartner Peer Insights website by Gartner Inc., one of the world’s leading technological research and consulting firms, is a great place to start your search for a hardware firewall solution. All reviews on Gartner Peer Insights are vetted and authenticated by Gartner, ensuring that they are genuine and trustworthy. While the reviewer and their organization are kept anonymous, the organization’s size and industry are stated. This provides prospective buyers with more context to judge whether a product is right for them.
- Look into the ease of integration with other solutions: Good network security requires a layered security stack of different solutions. This includes firewalls, endpoint security solutions like antivirus, access controls, network traffic analysis, threat intelligence, and more. You must ensure that the hardware firewall you choose integrates easily with other security products. This helps to eliminate any security gaps that may otherwise exist due to poor integration and incompatibility. Better integration is more likely with products from the same vendor. For example, Sangfor’s NGAF hardware firewall integrates seamlessly with its entire range of security products and solutions.
To see Sangfor's NGAF in action and understand how it is pioneering the future of next-generation firewalls, watch the following video:
Hardware Firewall Features to Consider
Hardware firewalls from different vendors will have varying security capabilities and the same capabilities may be underpinned by various techniques. When choosing a hardware firewall, it’s important to know what capabilities you require. Request details about those features from the vendor to make sure they fit the needs of your organization.
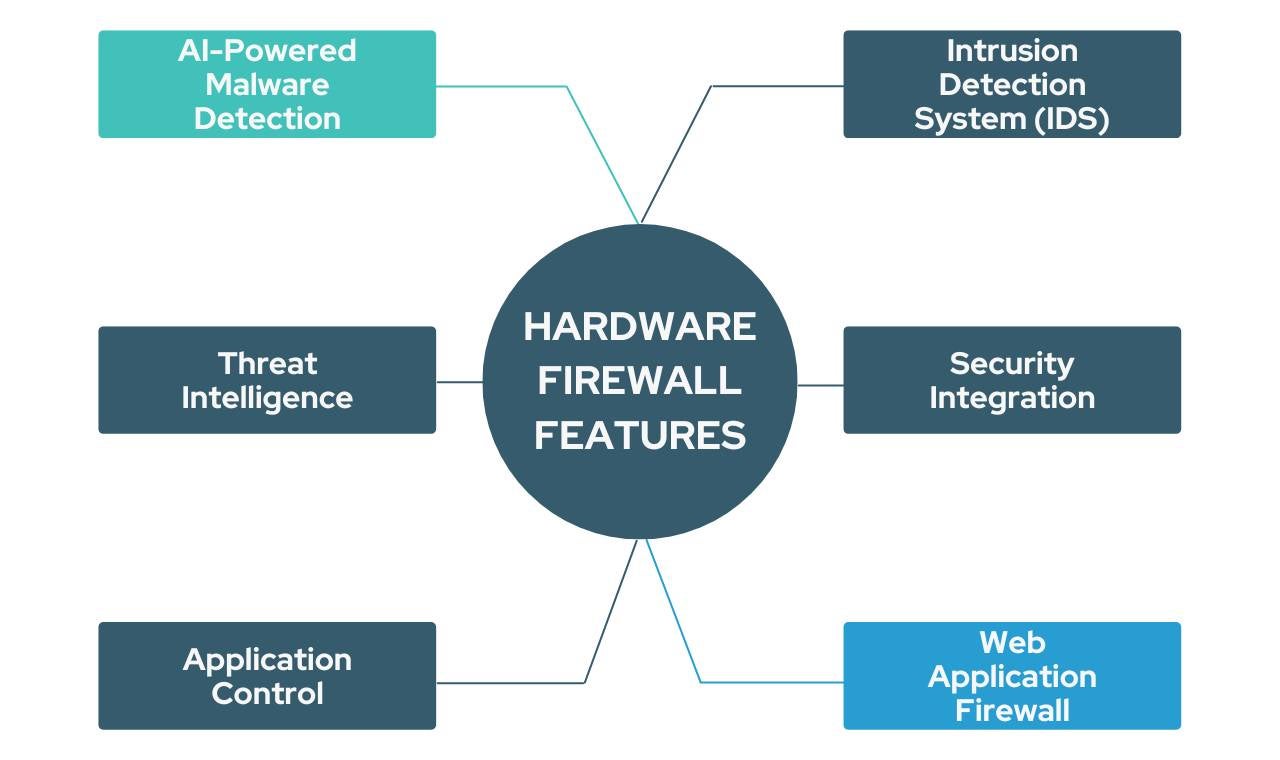
- AI-Powered Malware Detection: Firewalls filter malicious traffic based on rules and policies, but they don’t detect and block actual malware. That job has traditionally been left to antivirus or antimalware software installed on endpoints. Next generation hardware firewalls are integrated with antivirus so that malware is detected before landing on endpoints. Some malware detection engines use AI to detect new and unknown malware to achieve high malware detection rates. Organizations that are currently using traditional antivirus on their endpoints can enhance their protection with a hardware firewall integrated with AI-powered malware detection.
- Intrusion Detection System (IDS): IDS is a security tool that detects suspicious patterns of behavior that might indicate a threat. Some IDS work by detecting known patterns of malicious behavior using signature-based detection. However, as cyberattacks become increasingly sophisticated, this type of IDS has become less effective. Newer anomaly-based IDS, on the other hand, use AI and machine learning to detect unknown activity patterns. When choosing your hardware firewall, enquire whether the IDS is signature- or anomaly-based to make sure it fits your needs.
- Threat Intelligence: Cybercriminals are constantly developing new malware and hacking techniques. Firewall rules and malware signatures can become outdated very quickly and lose their effectiveness. Luckily, we can mitigate this using real-time threat intelligence. Threat intelligence feeds are continuous streams of data related to emerging threats. These can be integrated into security devices to enhance protection. When choosing your hardware firewall, enquire about the sources of the provider’s threat intelligence. Threat intelligence may come from the provider’s own security devices, third-party sources, or a combination of both. The source of the threat intelligence may have a geographical bias and, and therefore, you should choose a supplier with sources that best apply to your location.
- Security Integration: We have touched on the importance of hardware firewalls being able to integrate with other security tools above. This is beneficial in several ways. Firstly, integration allows for threat correlation, that is, the correlation of data and events from various security tools. This enables the integrated system to chain together a series of events to detect the most sophisticated threats that managed to bypass individual security tools. Secondly, integration also allows for coordinated responses to identified threats. For example, if malware is detected on an endpoint, a command will be issued to the firewall to block the IP address from which the malware was downloaded. Security integration builds a truly holistic security system that leaves a network virtually fool proof. Perspective buyers need to weigh up whether this type of integration is required for their level of risk.
- Application Control: Application control refers to controlling what applications are permitted to run on endpoints connected to the network. This allows network administrators to block any applications that are deemed to lower employee productivity, such as social media applications and applications that pose a threat to the network. Application control normally relies on integration with endpoint security solutions, where the latter reports all running applications on the endpoint, and the former enforces blocking. Prospective hardware firewall buyers who wish to make use of application control must ensure that the firewall and endpoint security solution integrate into this.
- Web Application Firewall: A web application firewall (WAF) is a type of firewall that works in the same way as a network firewall but is designed to filter HTTP traffic to and from web servers. This protects the web applications and services hosted on the server from web attacks such as SQL injection and cross-site scripting (XSS). WAFs are predominantly standalone devices but can also be integrated into hardware firewalls to protect both the network and web servers. If you are a small or mid-sized business that operates its own public-facing web applications and website, a WAF-integrated hardware firewall is ideal for saving costs and complexity.
Take Away
What should be the first step toward a network security-conscious future for your business? No solution is 100% secure, but by layering the right security solutions on top of the right foundation, you significantly reduce your risk of losing money, data, and reputation to cyberattacks. As the gatekeeper to your valuable data and systems in your network, a hardware firewall provides the foundation on which we build your robust network security fortress.
Sangfor’s Network Secure - Your Next-Generation Firewall Solution
As a robust type of hardware firewall, Sangfor Network Secure is a cutting-edge Next Generation Firewall (NGFW) solution for enterprises. It stands out with its unique features and capabilities. By combining AI Technology, Cloud Threat Intelligence, NG-WAF, IoT Security, and SoC Lite, Sangfor Network Secure redefines firewall technology for modern security needs. It holds multiple "world's first" titles, including being the first AI-enabled NGFW with intelligent detection and integration of Web Application Firewall (WAF), deception technology, and SOC Lite. With Sangfor Engine Zero, it achieves a remarkable 99.76% detection rate of known and unknown malware. The integration with Sangfor Neural-X provides real-time threat intelligence and analytics. Additionally, it offers cloud deception capabilities, robust web application protection with its integrated NG-WAF, and simplifies security operations with SOC Lite. By integrating with Sangfor Endpoint Secure and Cyber Command, it provides a comprehensive anti-ransomware solution. Sangfor Network Secure sets new standards for enterprise firewall solutions, ensuring advanced protection and simplified security management.
Sangfor's Network Secure Success Stories
- Bundamedik Healthcare System (BMHS), a healthcare provider in Indonesia, adopted Sangfor's Next-Generation Firewall to deliver perimeter security protection to both head offices and each branch.
- The Institute of Chartered Accountants of Pakistan (ICAP) uses the advanced Next-Generation Firewall for its enhanced malware detection and threat intelligence to ensure that cyber threats remain controlled and effectively removed without any damage to the network or data of the organization.
- The National Information Technology Board (NITB) uses Sangfor's Next-Generation Application Firewall for holistic and simplified web server protection. With the help of Sangfor's solutions, it can effectively provide advanced IT infrastructure for government bodies in Pakistan.
Frequently Asked Questions
Absolutely. It’s the first line of defense against harmful network traffic. It provides more comprehensive protection than a software firewall, is easier to install and update, and works 24/7.
Normally, a hardware firewall comes as a single unit with software pre-installed. Some hardware firewalls work on general OSs like Linux; most firewalls come with an operating system specifically designed to run the related software, reducing the risk of attack using vulnerabilities. They can also work alongside a larger and more comprehensive security system with advanced threat detection to provide greater overall protection.
A hardware firewall requires a higher initial investment than software firewalls, as it requires hardware installation. While software firewalls cost less to deploy, you may find that over time, you will pay more for the monthly subscription fee than you would have ultimately paid for a hardware firewall, which typically remains effective for 3-5 years.
The primary difference between hardware and software firewalls is that the hardware firewall runs on a physical device, while the software firewall is installed on a machine. Most PCs come with a built-in software firewall.
This will depend heavily on individual business needs. A hardware firewall is more secure, protects more computers and endpoints, and runs on its own power, not affecting computer performance. Centralized management means that a hardware firewall is easier to update for all users, making the subsequent operations and maintenance less troublesome and time-consuming. Software firewalls are better for businesses with smaller budgets, fewer endpoints, or fewer employees. However, with a software firewall’s lower price tag comes lower inspection and protection capabilities and complex operations and maintenance.
Absolutely. Using software firewalls in conjunction with hardware firewalls adds a layer of security to individual endpoints and the entire network as long as they are compatible with each other. When implemented together, hardware firewalls can provide network-wide protection from external threats. In contrast, software firewalls can provide more granular and closely inspected data protection for each individual device they are installed on. In many cases, businesses and individuals that are more concerned with their cyber security often implement multiple hardware and software firewalls to minimize any weaknesses in their defense.
Different businesses and organizations will have different cyber security needs depending on their industry, scope of operation, and the amount of confidential data they process on a daily basis. To find the best hardware firewall or a tailored cyber security solution for your needs, we recommend checking out our Enterprise Firewall Buyer’s Guide.





