Athena SWG Use Cases
Without Athena SWG the office environment is comparable to an internet cafe where users and staff can freely access video, social media, and endless entertainment. IT administrators are hard-pressed to identify exactly which users are consuming excess bandwidth, preventing effective control over user browsing behavior. Athena SWG can identify and control non-work-related applications in the network while allowing companies to keep a close eye on their bandwidth management, whereby they allocate all available bandwidth for key business needs, and improving business efficiency and productivity. Numerous professional traffic management features allow Athena SWG to rationally allocate bandwidth resources and maximize bandwidth usage. For organizations with multiple branches, Athena SWG provides a unified management platform and supports 3G link backup, making network management more efficient and reliable.
Because customers have vastly different authentication procedures, each internal network requires user authentication integration with AD, Radius to achieve SSO. Athena SWG guest authentication provides convenient access through Facebook, WeChat, SMS and offers a unified authentication solution, which manages both the wired and wireless connected users within a single SWG platform. Athena SWG also offers a switch based user access control capability to help control LAN user access. Finally, Sangfor IAG can be integrated with WLAN vendors like Cisco, Aruba to allow the Unified Authentication Center to drastically simplify the process of network integration and management.
To protect the user from web threats, a secure web gateway is an effective defense over web-based threats and enabling secure internet access. Athena SWG can work with your on-premise applications and internet traffic. With the accelerated SSL decryption performance, all HTTP and HTTPS traffic will be monitored and analyzed with Athena SWG, which is the huge bottleneck of other solutions like NGFW or UTM. The AI-based threat intelligence platform provides web filtering services and improves the capability of identifying known and unknown threats. It also keeps users protected while ensuring they enjoy a safe and secure web experience.
As unauthorized use of networks becomes more common, many countries and regions are developing and enforcing laws governing user internet access behavior. The Athena SWG internal application database comprehensively logs malicious user activity including file uploads, BBS posting, email, browsing history, and applications accessed. This audit solution assists in customer compliance with local legal regulations and serves as a valuable investigative resource in the event of illegal network usage incidents.
Sangfor Endpoint Secure Key Capabilities
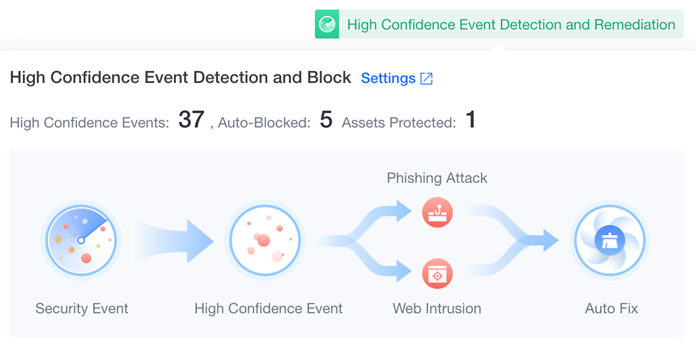
Phishing and web intrusion protection with automated response
- Enhanced protection against phishing and web intrusion attacks to counter the rising number of incidents worldwide.
- Accurate detection of phishing and web intrusion attacks, with detailed insights, including a comprehensive visual kill chain to pinpoint the origin and associated behaviors of the attack.
- Users can configure Sangfor Endpoint Secure to respond automatically to such attacks, such as terminating malicious processes and deleting malicious files to prevent lateral movement.
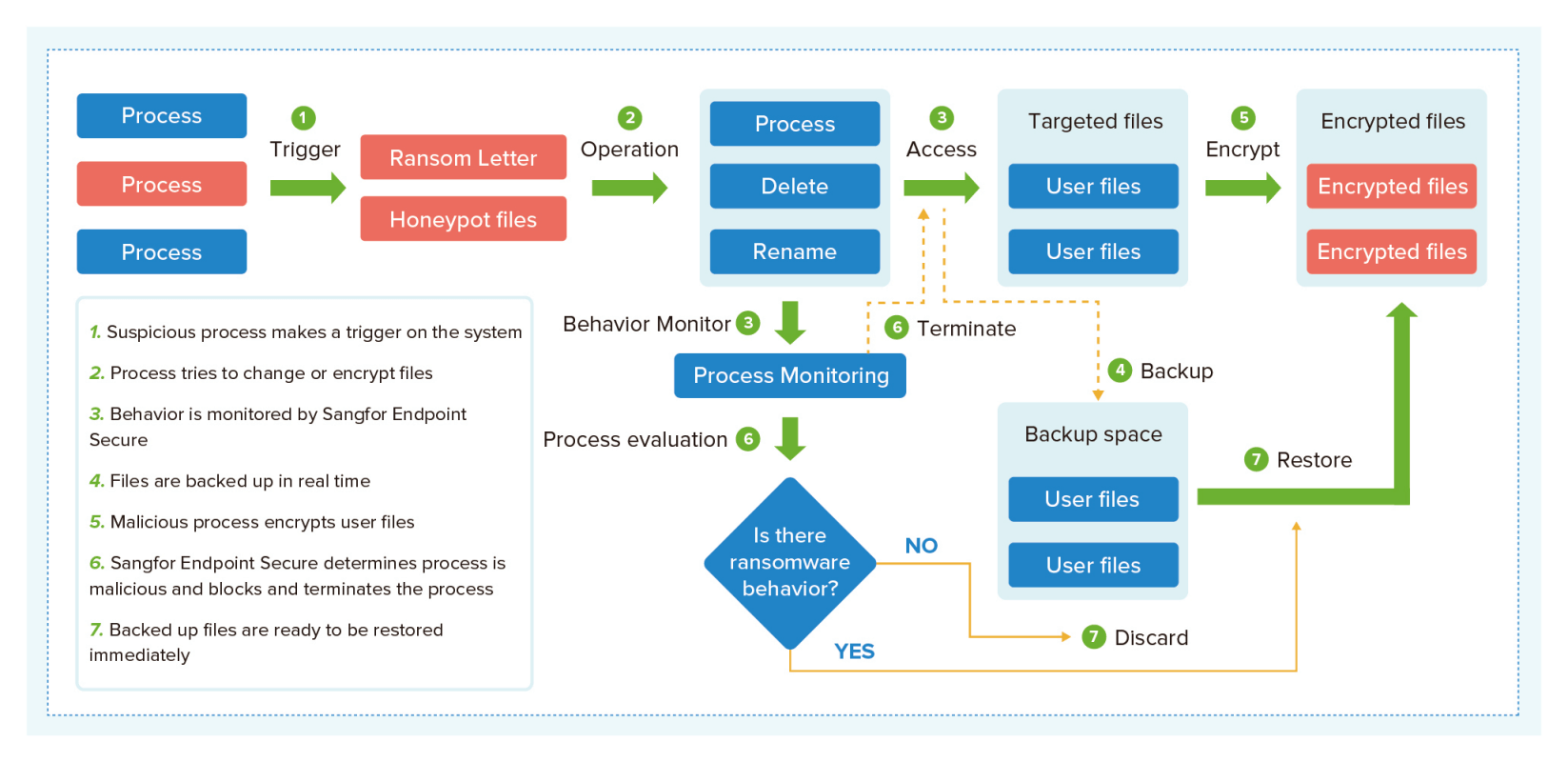
Ransomware Protection and Recovery
- Protects against all types of ransomware through static and dynamic AI-based detection engines.
- Detects suspicious ransomware-related processes and blocks them in as little as 3 seconds to ensure minimal impact on users’ assets.
- Ransomware indicators of compromise are collected from over 12 million devices deployed with Sangfor Endpoint Secure, allowing it to achieve a detection accuracy rate of 99.83%.
- In addition to existing ransomware protections, such as honeypot and RDP two-factor authentication, Sangfor Endpoint Secure provides ransomware recovery capabilities. These include file recovery and recovery via Windows Volume Shadow Copy Service (VSS) snapshot backup to fully secure and restore your data in case of ransomware encryption.
Synergy with Network and Cloud
Endpoint Secure integrates with Sangfor NGAF, IAG, and Cyber Command to enable advanced and coordinated threat detection and response. Threat correlation between endpoint, network, and cloud makes it possible to detect sophisticated threats that are missed by point solutions and produce an integrated evidence chain to streamline post-attack threat hunting and weakness remediation.
Phishing and web intrusion protection with automated response
- Enhanced protection against phishing and web intrusion attacks to counter the rising number of incidents worldwide.
- Accurate detection of phishing and web intrusion attacks, with detailed insights, including a comprehensive visual kill chain to pinpoint the origin and associated behaviors of the attack.
- Users can configure Sangfor Endpoint Secure to respond automatically to such attacks, such as terminating malicious processes and deleting malicious files to prevent lateral movement.

Ransomware Protection and Recovery
- Protects against all types of ransomware through static and dynamic AI-based detection engines.
- Detects suspicious ransomware-related processes and blocks them in as little as 3 seconds to ensure minimal impact on users’ assets.
- Ransomware indicators of compromise are collected from over 12 million devices deployed with Sangfor Endpoint Secure, allowing it to achieve a detection accuracy rate of 99.83%.
- In addition to existing ransomware protections, such as honeypot and RDP two-factor authentication, Sangfor Endpoint Secure provides ransomware recovery capabilities. These include file recovery and recovery via Windows Volume Shadow Copy Service (VSS) snapshot backup to fully secure and restore your data in case of ransomware encryption.

Synergy with Network and Cloud
Endpoint Secure integrates with Sangfor NGAF, IAG, and Cyber Command to enable advanced and coordinated threat detection and response. Threat correlation between endpoint, network, and cloud makes it possible to detect sophisticated threats that are missed by point solutions and produce an integrated evidence chain to streamline post-attack threat hunting and weakness remediation.
Network Secure Success Stories
Below you will find all the Success Stories of Sangfor, classified by Industry, such as Enterprises, Governments, Schools & Universities, etc.
EasyConnect Advantages

User-Friendly
Fully supporting Windows, MAC, Linux and other mainstream operating systems and internet browsers as well as virtual portals, application single sign-on and other functions, Sangfor EasyConnect simplifies system deployment and management.

Secure
EasyConnect includes an end-to-end security protection system, industry-leading encryption technology, multiple authentication methods, master-slave account binding and many other features to ensure user identity security, client/data security, transmission security, application permission security and audit security.

Fast
Various patented technologies optimize layer-by-layer from links, transmission & data to applications. Sangfor EasyConnect can accelerate access speed by 80%, providing each user with an extraordinary access experience.

Comprehensive
EasyConnect & Application Virtualization allow easy migration of business systems without secondary development. EasyApp & Security Reinforcement modules achieve automatic data encryption with its integrated VPN module, making it perfect for easy business mobility.
Sangfor aStor - High Performance and Low TCO Unified Storage Solution
Sangfor aStor uses software-defined technology to consolidate various storage resources (block, file, and object storage) into a unified resource pool for elastic expansion and on-demand allocation. It adopts a fully symmetrical distributed architecture, enabling flexible allocation of different storage resources—from high-performance to low-cost, large-capacity storage resources—to meet the specific needs of different services.
Available as a software and hardware-integrated solution or as a standalone software model, Sangfor aStor offers flexibility to accommodate various IT environments. It is scalable from just three commodity x86 server hardware nodes, making it a practical choice for businesses looking to efficiently manage their storage needs while maintaining the ability to scale and adapt to future demands.
Athena XDR Use Cases


Centralized Security Management
Centralized Security Management
Integrates cybersecurity tools into one platform to eliminate silos and boost operational efficiency.


Integrated Threat Detection & Response
Integrated Threat Detection & Response
Delivers unified detection and response across endpoints, servers, networks, and cloud using existing tools.


Noise Reduction & Threat Triage
Noise Reduction & Threat Triage
Grouping 2,000 security logs into one security alert and 30 security alerts into a single security incident.


Centralized Log Storage & Compliance Management
Centralized Log Storage & Compliance Management
Collects and stores logs with scalable retention to support compliance and efficient data searches.


Automated Investigation & Threat Hunting
Automated Investigation & Threat Hunting
Explains incidents and hunts related threats to reveal patterns and affected assets automatically.


APT Prevention & Detection
APT Prevention & Detection
Uses machine learning to detect hidden APT threats by analyzing correlated data across systems.
Sangfor NG-CDI Benefits

Business Centric
Application-centric management delivers outstanding business agility Run any app that your business favors, be it VM-based or container-based Adaptive infrastructure with Kubernetes conformant API

Secure and Resilient
Comprehensive stack of security with end-to-end protection Built-in infrastructure reliability with HA, backup and DR Platform-level resiliency with automated self-healing capabilities

Cost-Saving
Start from two nodes and scale out on demand Unified platform for both legacy and modern applications Easy-to-use GUI-based management simplifies O&M
Key Security Operations Challenges
Siloed Security Products
Organizations often have numerous security tools from different vendors. The lack of communication among these tools reduces overall effectiveness and limits the ability to automate threat detection and incident response for improved efficiency.
Flooded with Alerts
Security teams face an overwhelming volume of alerts each day, leading to alert fatigue and difficulty identifying the most critical threats. Without effective correlation analysis, false positives remain high, further reducing efficiency and response accuracy.
Lack of Context in Investigation
Security analysts often struggle to investigate threats due to fragmented data across multiple tools and platforms. This results in broken visibility and incomplete context, causing delays in identifying the root cause and responding effectively.
Security Skills Shortage
A lack of qualified cybersecurity professionals prevents organizations from running 24/7 security operations, leaving them vulnerable during non-business hours. This shortage also limits their ability to effectively manage advanced threats like APTs and emerging threats.
Athena XDR Frequently Asked Questions
XDR (Extended Detection and Response) is an advanced cybersecurity solution that provides unified threat detection, investigation, and response across multiple security layers—such as endpoints, networks, servers, cloud workloads, and email. Unlike traditional tools that operate in silos, XDR integrates and correlates data across different security tools to deliver a centralized, real-time view of threats.
Athena XDR stands apart from other XDR solutions in several important ways.
First, while many XDR platforms evolved from their vendors’ EDR products—often requiring customers to use that specific EDR—Athena XDR was built from the ground up as a standalone, vendor-neutral platform. Its open architecture allows seamless integration with a wide range of third-party EDRs, enabling organizations to leverage their existing security investments for both detection and response.
Second, Athena XDR functions as a true all-in-one SecOps platform. In contrast to other XDRs that rely on third-party tools for SIEM, SOAR, reporting, or ticketing, Athena includes these capabilities natively, streamlining workflows and reducing complexity for SOC teams.
Third, Sangfor leads the market in GenAI integration. Unlike other solutions that use GenAI merely as a chatbot for user queries, Athena XDR features dedicated GenAI models—such as Detection GPT, Operations GPT, and Anti-Phishing GPT—designed to handle specific security domains and replicate real human judgment and analysis.
Fourth, Athena XDR goes beyond basic alert aggregation. It performs true correlation analysis using AI-driven normalization and parsing to identify meaningful relationships between disparate data points, reconstructing the full sequence and context of an attack.
Lastly, Athena XDR offers flexible deployment options. While most vendors provide only SaaS-based offerings, Athena is available in both SaaS and on-premises models, accommodating organizations with strict data residency, compliance, or infrastructure requirements.
While both Athena XDR and SIEM capture and store logs from diverse third-party devices and support search and security analytics, they serve different purposes:
Athena XDR focuses on security operations, emphasizing data access from security devices. It supports real-time detection and analysis, enabling efficient correlation through built-in rules and engines to identify threats and malicious actors.
SIEM, on the other hand, gathers data from a broader range of devices, not limited to security tools. Its log collection is primarily geared toward threat hunting, allowing users to trace hacker activities following a security incident rather than conducting real-time security analysis. Additionally, SIEM relies heavily on manual rule creation, which limits detection to known threats and makes it less effective against unknown threats. In practical scenarios, many SIEM customers use it to monitor the operational status of network device.
Athena EPP and STA/NDR are both core components of Athena XDR. While deploying them together is recommended for enhanced security, it is not mandatory. This flexibility is especially valuable if you are using an EDR solution from another vendor and do not wish to replace it.
However, for organizations not using a Network Traffic Analysis (NTA) solution, we strongly recommend deploying Athena STA for the following four reasons:
- Enhanced Detection Capabilities: Athena STA provides NTA capabilities by monitoring traffic and enabling protection for unmanaged endpoint devices (BYOD), intranet lateral movement, and shadow IT.
- Correlated Traffic Analysis: Athena STA improves correlation between EDR and firewall data, enhancing visualization and reducing false negatives and false positives.
- Ease of Deployment: Athena STA is easy to deploy and does not disrupt normal business operations, using a bypass method to mirror traffic from the switch.
- Cost-Effective Solution: Athena STA is affordable and offers excellent value for enhanced security.
Athena XDR offers several distinct advantages over Athena NDR:
- Comprehensive Log Collection: Athena XDR captures raw logs from Sangfor components, enabling deeper correlation analysis beyond just security alerts.
- Enhanced Third-Party Log Integration: It effectively ingests logs from third-party devices, utilizing AI-driven parsing for automated log analysis, allowing for comprehensive security and correlation insights.
- Visualized Security Incidents: Athena XDR graphically represents individual security incidents in their entirety, reconstructing the attack narrative rather than relying solely on aggregated data.
- Flexible Reporting: The platform supports customizable security report templates, enabling users to create tailored reports with drag-and-drop functionality.
- Case Management: Athena XDR includes a ticketing system to help large organizations manage security operations more effectively, establishing clear accountability for security tasks.
- Integration with Security GPT: It seamlessly combines with Operations GPT and Anti-phishing GPT tools, providing organizations with user-friendly and comprehensive security solutions.
Sangfor Receives Frost & Sullivan’s 2025 APAC Customer Value Leadership Recognition
In the Extended Detection and Response Market
Learn more!Athena SWG Reviews

Comprehensive reporting, ease of use and intuitive dashboard
Administrator of State and Local Government

IAG is practical and helpful. It help to kept the log for company for audit.
CTO of a Carriers Industry

IAM is a good product for improve the network security, operation and control.
Assistant IT Manager of an Industrial Company

Bye bye...... bad performance online meeting by using Sangfor IAG
CxO of an Insurance Industry
Reviews of Sangfor Cyber Command Customers on Gartner Peer Insights

What is XDR?
XDR is becoming a critical component in modern cybersecurity strategies, offering a unified approach to threat detection and response across endpoints, networks, servers, email, and more. But what is XDR? And why do you need it?
In this video, Sangfor Solutions Expert Witt Lin explains how XDR consolidates security tools into a single platform to improve visibility, streamline operations, and accelerate threat response. Watch the video to learn how XDR can help your organization stay ahead of advanced threats, reduce alert fatigue, and enhance overall security posture.
Latest Events

Sangfor International Roadshow 2025 – Thailand
Sangfor's Bangkok Roadshow united 400+ attendees for a day of tech insights, cybersecurity trends, and cloud innovation under "Digital Plus | IT Minus".
Sangfor International Roadshow 2025 – Jeddah, Saudi Arabia
Building on the electrifying momentum from Riyadh, Sangfor Technologies successfully brought the energy to Jeddah with an unforgettable stop on our 2025 Roadshow on May 20th!
Sangfor International Roadshow 2025 – Riyadh, Saudi Arabia
We are excited to share the outstanding success of the Sangfor 2025 Roadshow held in Riyadh, Saudi Arabia, on 18th May.
Latest Blog

Unified Threat Management vs Traditional Security: What’s Better in 2025?
Discover in-depth 2025 comparison of unified threat management vs traditional security with market data, feature analysis & buying guide.
Cartier Confirms Customer Data Breach Amid Growing Cybersecurity Concerns in Retail
Cartier confirms a cyberattack compromising customer data, joining North Face and Victoria’s Secret in a surge of retail-targeted breaches.
Marks & Spencer Cyberattack: A Wake-Up Call for Supply Chain Cybersecurity
Learn how the 2025 M&S cyberattack exposed third-party risk, disrupted services, and revealed key lessons for retail cybersecurity resilience.
Latest News

Sangfor Technologies Unveils Sangfor Athena: A Bold New Brand for Its Cybersecurity Business
Sangfor Athena unifies advanced security solutions under one brand, powered by SynergyAI for proactive cyber defense. Discover intelligent, integrated protection today!
Sangfor Honored with Frost & Sullivan’s 2025 APAC XDR Customer Value Leadership Recognition
Sangfor wins Frost & Sullivan’s 2025 APAC award for XDR, recognized for AI-driven threat detection, automation, and customer-centric innovation.
Sangfor Backup Platform Powered by Veeam Sets to Deliver Effortless, Enterprise-Grade Data Protection
Empower your business with Sangfor Backup Platform powered by Veeam—offering agentless backup, 1-click recovery, and simplified data management.
test message
12345
| 1 | 2 |
| 3 | 4 |



12345
| 1 | 2 |
| 3 | 4 |




