
REvil Ransomware has reemerged to attack global PC giant Acer, according to BleepingComputer. As you might know, Acer is a Taiwan-based electronics and computer manufacturer of laptops, desktops, and monitors, employing 7,000 employees and earning $7.8 billion in 2019. Thus far, Acer has only responded to interested parties at BleepingComputer by saying that they "reported recent abnormal situations.” Acer’s full statement reads:
"Acer routinely monitors its IT systems, and most cyberattacks are well defensed. Companies like us are constantly under attack, and we have reported recent abnormal situations observed to the relevant law enforcement and data protection authorities in multiple countries."
"We have been continuously enhancing our cybersecurity infrastructure to protect business continuity and our information integrity. We urge all companies and organizations to adhere to cyber security disciplines and best practices, and be vigilant to any network activity abnormalities." - Acer.
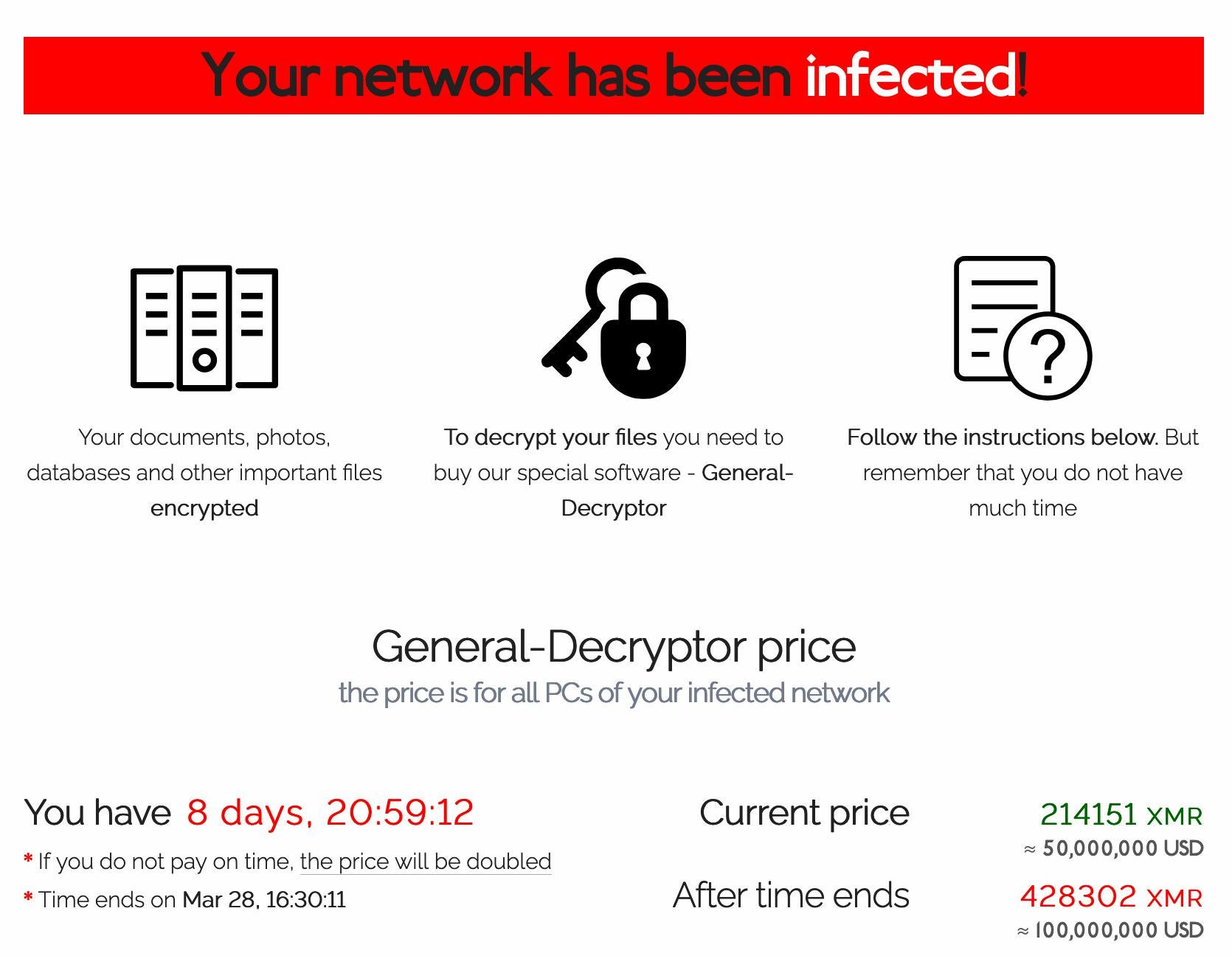
On March 14th, an Acer representative was surprised to find a ransom demand for $50 million, the largest recorded REvil ransom demand to date. REvil has been quite active in the APAC region and sadly, quite lucrative, lately, with a recent attack and demand for $30 million from Dairy Farm. The Dairy Farm Group has over 10,000 outlets and 230,000 employees throughout Asia, with total annual sales exceeding $27 billion. Acer should be nervous, because while they will not confirm or deny the reports, there were recently stolen spreadsheets and banking data posted online, as a warning to the computer manufacturer that their data is in danger.
LeMagIT first reported that the cybercriminals had offered a 20% discount on the original ransom if paid by March 17. ComputerWeekly reported that Acer allegedly offered $10 million to REvil operators, who turned it down and threatened to double the ransom demand if the full payment was not made before March 28th – so the clock is ticking. Bleeping Computer believes that REvil is using a vulnerability in Acer’s Microsoft Exchange server. On March 11 Microsoft issued an alert that a new family of ransomware was discovered that exploited the Exchange vulnerabilities so it is possible that REvil was reengineered to do so as well.
"It was only a matter of time before the recent Microsoft Exchange vulnerability exploited an organization, and in the current climate, it was swift," says James McQuiggan, security awareness advocate with KnowBe4. "The WannaCry ransomware from 2017 utilized the EternalBlue exploit and took only a few months before a massive attack occurred. With this attack, it took just weeks."
Ransomware is getting easier to operate and create, and the vulnerabilities harder to close – and as we can see, regardless of how accustomed a company is to cyber-attack, even those with all the IT resources in the world are susceptible. The eyes of the world are on Acer, and with good reason – their reputation is at stake. Luckily Acer has quite a portfolio and budget to fall back on. Does your business?
You might not suffer a ground-breaking ransomware attack, but even smaller scale attacks are likely to become very pricy, if this ransom demand is any indication of where the market is headed. It’s vital that you protect your network from this type of attack, and judiciously deploy products which can help you do just this.
Why Sangfor?
Sangfor provides the best and most powerful integrated solutions through the correlation of Sangfor Next Generation Application Firewall (NGAF), Cyber Command, Intelligent Threat Detection & Response, and Sangfor Endpoint Secure.
Sangfor NGAF is a converged security solution designed to protect users from internal, external, existing and future threats, with threat intelligence updated regularly to keep networks safer from ransomware. Sangfor focuses on four fundamental elements, proven to strengthen its capabilities, including security visibility, real-time detection & rapid response, simplified O&M and maintaining a high-performance application layer (L7).
Sangfor NGAF was designed to work seamlessly with Sangfor’s Cyber Command platform, which significantly improves overall security detection and response capabilities by monitoring internal network traffic, correlating existing security events and applying AI and behaviour analysis, all aided by global threat intelligence. Cyber Command uncovers breaches of existing security controls while simultaneously performing an impact analysis to identify hidden threat. Because Cyber Command integrates network and endpoint security solutions like NGAF and Endpoint Secure, the administrator’s ability to navigate and understand the overall threat landscape is significantly improved, and response to threat is automated and simplified.
The power of NGAF and Cyber Command is formidable, but add to that Sangfor Endpoint Secure, the future of endpoint protection, managing the endpoint asset security life cycle from prevention, detection and defence, to response. Endpoint Secure provides the most accurate identification and mitigation of rogue or malicious processes and applications.
Sangfor Technologies is an APAC-based, global leading vendor of IT infrastructure solutions specializing in Network Security and Cloud Computing. Visit us at www.sangfor.com to learn more about Sangfor’s Security solutions, and let Sangfor make your IT simpler, more secure and valuable.





