It has been almost 2 weeks since Sangfor wrote about the DarkSide ransomware attack on Colonial Pipeline in the US, and a week since operations were restored, but the after-effects continue. Although gas is again flowing through the largest pipeline in the US, gasoline prices hit a six-year high with a national average of $3.04 USD per gallon this week, as over 10,000 pumps on the eastern half of the country were still without supply. At one-point last week, the price of gasoline reached $6.99 USD due to hoarding and price gouging.
It was also confirmed today that Joseph Blount, CEO of Colonial Pipeline Co., paid $4.4M USD ransom in 75 Bitcoins to the DarkSide group on May 7, the day of the attack. Mr. Blount, after much consideration, likened the ransomware attack to pipeline and refinery shutdowns lasting several days, that occurred during many past strong Gulf Coast hurricanes.

Joseph Blount, CEO of Colonial Pipeline. Photo: PHOTO: COLONIAL PIPELINE CO.
“I know that’s a highly controversial decision. I didn’t make it lightly,” Mr. Blount said publicly today. “I will admit that I wasn’t comfortable seeing money go out the door to people like this. But it was the right thing to do for the country.”
It may have been the right thing to do for the country, but it did little to help restore operations at Colonial Pipeline. The decryption tool provided after payment was so slow, Colonial Pipeline still had to restore backups of data to restore operations in a timely manner.
Colonial Pipeline’s pipeline system moves gasoline and other fuels from refineries in the US Gulf Coast and other locations over 5,500 miles to customers in the Eastern and Southern United States. The pipeline normally carries over 100 million gallons of fuel per day (45% of all fuel consumed on the eastern half of the US), making it the biggest refined products pipeline in the US, according to the company.
Ransamware Attack Timeline
The Colonial Pipeline story is not just about a company recovering from a cyberattack, but also a lesson on how the federal and several state governments acted to contain a national energy crisis.
7 May 2021, 5:30AM: DarkSide ransomware attack was discovered in Colonial Pipeline’s business operations systems, including the customer billing system, when a ransomware note was discovered on a business system. 100 gigabytes of data were also stolen in a double extortion scheme where data is held hostage with threats to leak the stolen data if the ransom is not paid. The mechanisms used to breach and infect systems have not been publicly disclosed as of this date.
7 May 2021, approximately 6:00AM: CEO Joseph Blount was notified of the attack and told that gas pipeline operation systems were not yet affected.
7 May 2021, approximately 6:30AM: Pipeline operations were shutdown to prevent ransomware from attacking operations and control systems. This affected 260 gasoline delivery points across 13 states and Washington, D.C. Employees were instructed not to log into any systems on the corporate network for fear of further spreading ransomware. Colonial Pipeline contacted the FBI’s offices in Atlanta and San Francisco, as well as a representative from the Cybersecurity and Infrastructure Security Agency (CISA), as per their operations protocol. Cybersecurity vendor FireEye was reportedly hired to consult and investigate.
7 May 20201, evening: CEO Blount, after consultation with cybersecurity experts, US government authorities, and their cyber insurance carrier, paid $4.4M USD using 75 Bitcoins to DarkSide group. Ransomware decryption tool was received by Colonial Pipeline.
Recovery operations start. Colonial Pipeline attempts to use the decryption tool to decrypt infected systems, but tool proves to be inefficient and very slow. Colonial Pipeline forced to restore backups if available. US authorities work with Colonial Pipeline to investigate how breach occurred and trace attack back to DarkSide.
10 May 2021: Colonial Pipeline releases announcements “…Colonial operations team is executing a plan that involves an incremental process that will facilitate a return to service in a phased approach…,” and “…Line 4, which runs from Greensboro, N.C., to Woodbine, Md., is operating under manual control for a limited period of time while existing inventory is available.”
US Department of Transportation issued exception on hours of operation for transportation of fuel products across the eastern United States, as well as the US Environmental Protection Agency (EPA) issuing waivers to reduce supply disruptions. Transportation hours for gasoline, diesel and jet fuel are normally limited during the day to prevent hazardous accidents during peak driving hours.
North Carolina, South Carolina and Virginia declared states of emergency due to gasoline supply shortages.
12 May 2021: US President Joseph Biden signs an Executive Order on Improving the Nation’s Cybersecurity with the goal of improving US cybersecurity defenses, after a string of cyberattacks on the federal government and private companies, exacerbated by concerns about fuel shortages caused by the attack on Colonial Pipeline.
The order states, incremental improvements will not give us the security we need; instead, the federal government needs to make bold changes and significant investments in order to defend the vital institutions that underpin the American way of life."
12 May 2021, 5:10PM: Colonial Pipeline announces restart of pipeline operations and gasoline starts to flow. But it will take several days for the pipeline to fill and delivery supply chain to return to normal. An army of employees are walking or driving along the 5,500-mile length of pipeline to ensure there are no operational issues.
13 May 2021, 4:40PM: Colonial Pipeline announces pipeline operations fully restarted with delivery to all client markets. But it will take several days for the pipeline to fill and delivery supply chain to return to normal.
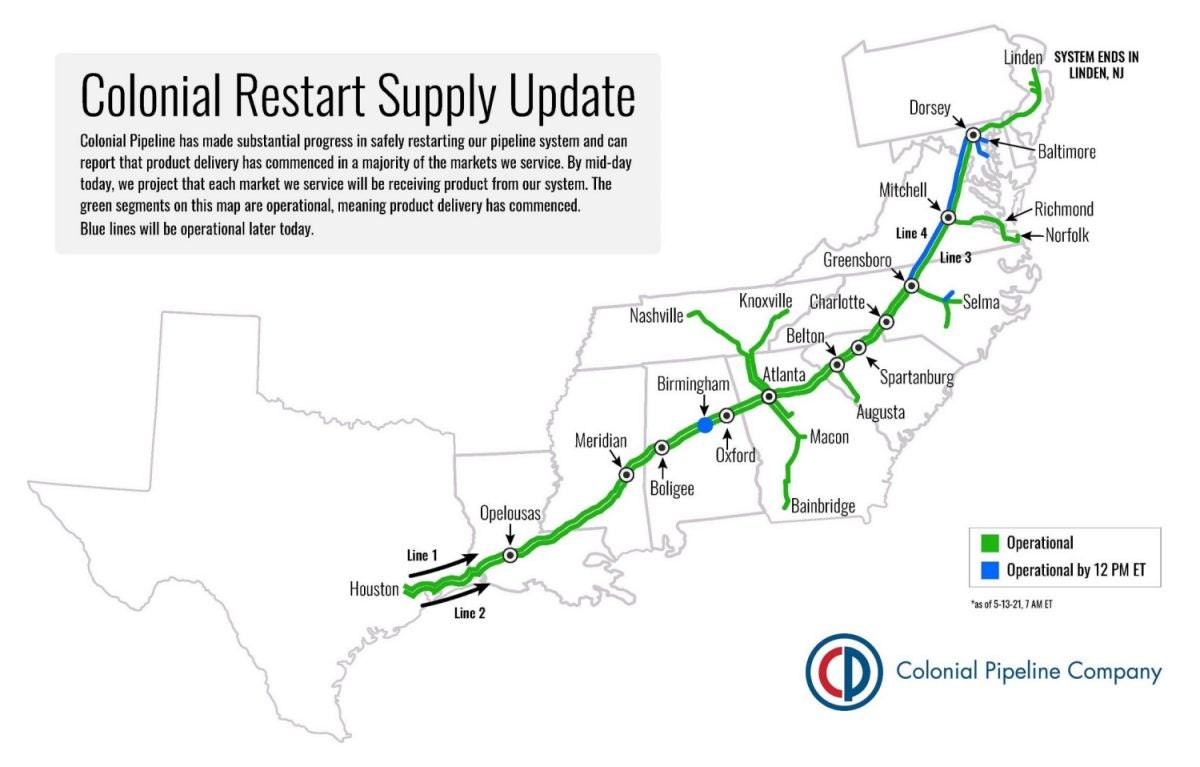
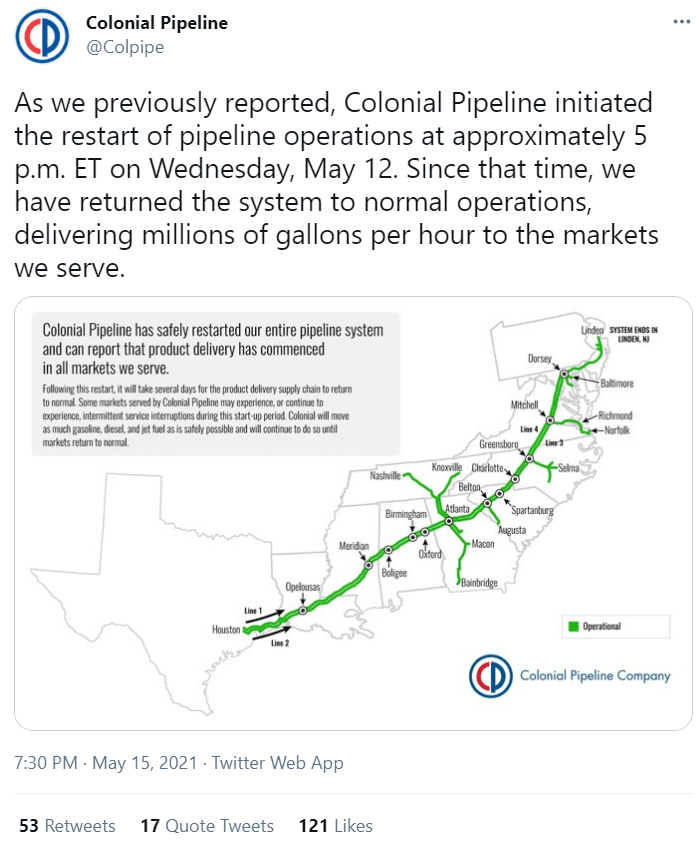
15 May 2021: Colonial Pipeline tweets all pipeline operations fully normal.
Effects and Aftereffects of the Attack
- The transportation of aviation fuel was impacted by the pipeline shutdown and American Airlines Group AAL had to put additional stops into some long-haul routes originating from Charlotte, NC. Other carriers like United Airlines and Southwest Airlines had to take extra fuel on flights.
- A shortage of certified truck drivers that can drive tanker trucks became immediately obvious as few were available to transport fuel in place of the pipeline. Most were laid off during the pandemic and many had their certifications expire during that time.
- Fears of Inflation driven by spot energy price surges possibly forcing increases in the retail prices in the near future caused the US Stock Markets to fall 2.0% before bouncing back over 500 points later in the week. The impact on US markets also impacted Asian stock markets causing them to fall as well.
- This is one of the largest and most successful cyberattacks on a critical component of a country's infrastructure to date -- but it is not the first and nor will it be the last. There have already been attacks globally against power grids & nuclear power plants, water treatment facilities, telecommunications, transportation, and healthcare.
- DarkSide made over $90M USD in Bitcoin in nine months before announcing last week that they are shutting down their Ransomware-as-a-Service (RaaS). Originally it was thought DarkSide was ceasing operations because of pursuit by US law enforcement, but it appears someone emptied their Bitcoin accounts and stole all their money. That is karma for you.
- The executive order President Biden signed to improve national cybersecurity is laudable, but is it enough? The order includes a shift to multi-factor authentication, data encryption both at rest and in transit, a zero-trust security model, and improvements in endpoint protection and incident response.
The Big Takeaway
One of the biggest flaws in Colonial Pipeline’s security architecture was that they could not quicky prevent business systems from infecting operational systems, so they had to shut down everything to be sure. Had Colonial Pipeline implemented strong anti-ransom protection, the effects of the attack could have been minimized and contained.
Cyberattacks including ransomware are only going to increase. They will never stop because there is too much profit in it. Worse, attacks are going to be directed more at critical infrastructure because it may be the most vulnerable and the most impactful for ransoms to be paid. More attention and priority are needed to improving infrastructure security worldwide. Yet, little is being done globally or even regionally to secure aging and obsolete infrastructure cybersecurity.
Sangfor Protects Infrastructure
Sangfor protects critical information infrastructure around the world, providing real-time comprehensive security monitoring and protection of critical information infrastructure.
Sangfor Solution for Ransomware based on Sangfor’s award winning Endpoint Secure endpoint protection, the award winning NGAF next-generation firewall and the next generation Cyber Command threat hunting platform is proven to break every step of the ransomware attack chain, providing comprehensive prevention, protection, detection, and response.
- Prevention: Identify vulnerabilities in systems before an attack through security baseline inspection, vulnerability detection and repair, and blocking the entry point of ransomware attacks.
- Protection: Deploying protection against brute-force RDP & login attacks, fileless APT attacks, as well as technologies such as ransomware honeypots and network-wide one-click kill of malware.
- Detection and response: Real-time AI-based malware/APT detection, network-wide threat visualization, hybrid network/cloud integration allows the NGAF to work with Endpoint Secure to stop command & control (C&C) communications and enact micro-isolation of endpoints to stop the lateral spread of ransomware throughout the environment.
Sangfor VDI provides secure virtual desktop environments that facilitate secure ICS and infrastructure operations while preventing both APT/ransomware from attacking and sensitive data from being exfiltrated. In addition, Sangfor's MSS security operation service suites provide users with preventative, monitoring, and incident response services for ransomware prevention and response.
Sangfor reminds users that the best protection against ransomware is prevention. Most files encrypted by ransomware cannot be decrypted so regular preventive measures should include:
- Upgrade/patch systems and applications to mitigate high-risk vulnerabilities.
- Perform regular remote offline multi-media backup of important data files.
- Do not click on email attachments from unknown sources, and do not download software from unknown websites.
- Remove unnecessary file sharing permissions across all systems.
- Change account passwords using strong passwords and avoid using the same password on multiple systems.
- Disable RDP and do not map RDP services to external network unless absolutely necessary.
- Use endpoint protection with proven ransomware defense and response capabilities such as ransomware honeypots to stop encryption processes
To know more about this topic, please join us in this webinar on BrightTalk
BrightTALK Webinar: US Colonial Pipeline attack: Everything you need to know

About this Webinar
Colonial Pipeline is the largest oil product pipeline operator in the United States, and the recent Ransomware attack forced shutdown of all their operations.
This cyber attack is just the latest in a long series of serious ransomware and malware attacks, and we can’t help but envision a world in the not-too-distant future where ransomware attacks impact all our daily lives. Ransomware is booming and now targeting all kind of industries, including critical infrastructure, healthcare and government.
Participate in this webinar to learn more about this recent attack, how it unfolded, its impact and what your organization can do to prevent such cyber-attacks.





