The modern age of computing has brought about various improvements in how we communicate, store, and share data. The cloud has become an essential part of the information age and enhanced our ability to connect while simplifying the means to. However, like most technologies at the forefront of our era, cloud computing has vulnerabilities that malicious agents might look to exploit for their benefit.
The hesitation of most companies to make the transition to the cloud has stemmed from a general security concern – storing data in this intangible entity could feel uncertain. However, with the adoption of cloud infrastructure growing rapidly across industries, companies must understand the security challenges they may face in the cloud transition.

According to a report, the global cloud computing market size is expected to grow from USD 545.8 billion in 2022 to USD 1240.9 billion by 2027 with the Compound Annual Growth Rate (CAGR) of 17.9% during the forecast period - Gartner has predicted that 75% of cloud security failures by the year 2023 will be the result of inadequate management of identities, access, and privileges - up from 50% in 2020. Several factors are driving these cloud security breakdowns and we’ve rounded up the top 12 to help you navigate the cloud more efficiently.
Enterprise Cloud Security Threats
Organizations need to be aware of the potential security challenges they might encounter when adopting an enterprise cloud infrastructure. Some of the most common security issues with enterprise cloud computing may include:
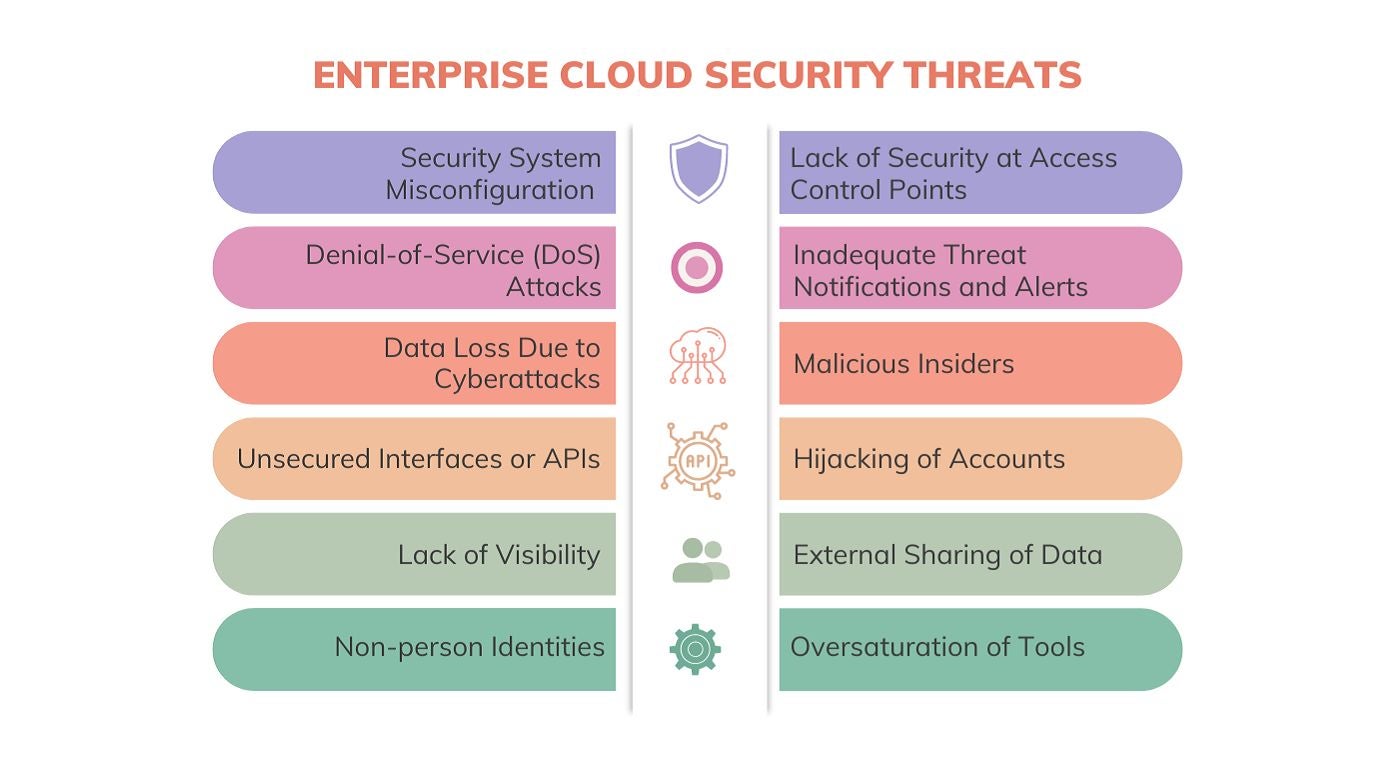
1. Security System Misconfiguration
A security system misconfiguration arises when essential security settings are either not implemented or implemented with errors. Cloud misconfigurations are specific errors, glitches, or gaps in your cloud environment that may leave your company exposed to potential risks – either in the form of data breaches, malware, or ransomware threats.
The most common misconfigurations in cloud computing involve:
- Exposing unencrypted data on the internet without any required authentication in place.
- Giving the public access to storage buckets.
- Allowing all network users to access cloud-stored data.
- The storing of encryption passwords and keys in open repositories.
The misconfiguration of a cloud security system is the leading cause of most cloud breaches and can be attributed to at least 3 main factors – firstly, in their efforts to make data more accessible and easier to share through the cloud, companies may encounter difficulty discerning who should have authorized access to data stores. Secondly, the use of multi-cloud infrastructures – with separate vendor security protocols, allows space for oversight and misconfigurations to occur. Finally, the use of inadequate cloud platforms with waning security measures may lead to a misconfiguration.
2. Denial-of-Service (DoS) Attacks
Denial-of-Service (DoS) attacks are designed to shut down a network and make it inaccessible to its intended users by flooding the targeted system with traffic or sending it information that triggers a crash. Most companies use the cloud to store and run critical applications and a successful DoS attack can compromise the network’s data - which can then be leveraged against the company for monetary gain.
The interruption of the cloud network’s ability to function during this type of attack can result in mass revenue loss and damage to a company’s brand. A responsible cloud security vendor will ensure enhanced cloud security measures to reduce the impact of a Denial-of-Service (DoS) attack.
3. Data Loss Due to Cyber-attacks
According to Statista 2021, 64% of respondents named data loss as their biggest cloud security concern and it’s not difficult to see why. The cloud is known most for its ability to store large amounts of data for companies without the hassle of on-site infrastructure or servers. Despite this forerunning feature, data breaches still stand to undercut the integrity of an organization’s cloud infrastructure. Cloud platforms make accessibility an important feature of cloud architecture to allow users to share and access data remotely with ease - which hackers may exploit to their advantage.
Data breaches involve the accessing of sensitive data to be stolen, copied, or leaked to external parties. These breaches may have nefarious outcomes, yet their means are often accidental – through human error or ineffective cybersecurity practices.
Nealy 45% of the data breaches in 2022 occurred within the cloud, according to the IBM Cost of a Data Breach report – where organizations with a hybrid cloud model achieved a lower average data breach cost of US$3.80 million—compared to organizations with a public or private cloud model.
Functional and tested disaster recovery capabilities must be installed within your cloud platform to ensure data efficiency.
4. Lack of Security at Access Control Points
A cloud infrastructure works outside of the physical parameters of an organization to make remote access achievable for employees and customers, alike. This feature has become increasingly attractive since the pandemic and the use of remote working models.
An access control point is the part of your security plan that stops intruders from entering the premises and verifies the access of people entering the facility – usually the entrance and exit perimeters of the physical area. With the use of cloud-based systems, the access control points of an organization don’t always fall within their physical access – making it easier for cyber-criminals to infiltrate the system, sometimes even without the organization’s awareness.
Cloud vendors are responsible for ensuring that the servers that provide cloud computing capabilities are secured at all access control points.
5. Inadequate Threat Notifications and Alerts
When a cyber-attack occurs, it’s crucial to have a system in place that will notify you immediately and alert your security infrastructure of any potential breach. This is enhanced when using cloud-based software as the instantaneous nature of the cyber-threats that target cloud technology needs to be met with an equally, if not more, rapid notification system for its mitigation.
Cloud platforms that ensure proactive searches for potential threats and alert organizations in real time of their dangers are more effective in keeping security in place.
6. Unsecured Interfaces or APIs
The term “interface” refers to a form of communication, leading to the understanding that an Application Programming Interface (API) is a software intermediary that allows two separate applications to communicate.
In cloud applications, APIs can be used to access different platforms and efficiently manage their security. They can be used to define the possible features and functions of the app or service. Public clouds are specifically based on their automated and self-servicing capabilities, making APIs inherently necessary to run them.
The use of APIs in the cloud computing sector has drastically improved migration and connectivity, however, they do pose a cybersecurity risk when they are left unprotected. An API that is left without adequate security provides an entry point for unauthorized access into the network where any amount of damage can be wrought.
7. Hijacking of Accounts
Account hijacking in cloud computing refers to gaining control of a cloud-based employee account. The credentials of a compromised user can exploit an entire system and use fraudulent accounts to impersonate personnel of authority and access sensitive information.
Cloud infrastructure makes it much more difficult to identify an account that has been hijacked and mitigate its access to the database before any damage can be done or information can be exfiltrated. The use of weak passwords, poor cyber hygiene practices, and lacking cybersecurity defenses from cloud platforms only enables this threat - exacerbating the impact of phishing attacks and data breaches.
8. Lack of Visibility
Security for cloud-based software has an unfortunate limitation in terms of visibility – where physical premises can use measures that ensure access is limited and areas are restricted, cloud resources are off-premises and do not guarantee that the infrastructure can be secured at all times.
Cloud vendors should focus on the constant and consistent monitoring of the cloud infrastructure to ensure that no malicious agents are found in areas prohibited and that the company always has access to its entire network.
9. External Sharing of Data
Cloud computing has revolutionized the way we can share and collaborate on files – making data accessible and simplifying how resources are connected. This has especially proven useful during the age of remote working.
Unfortunately, this external accessibility can also be a major security hazard for your cloud network. The difficulty lies in the ability to share a link to resources and access to several databases with so much ease that the security of that resource is then compromised. In a rush to make cloud sharing more convenient and innovative, we’ve exposed flaws in the infrastructure that can be exploited.
10. Malicious Insiders
When we consider malicious agents, we often presume they’d come from the outside and try to pry into the mainframe, but the personnel we employ are not impervious to a criminal rationale.
Insider threats are most commonly known as those agents within an organization that may accidentally or intentionally exploit their position and authorization to allow third-party access into a network. The detection of a malicious insider in cloud-based software is even more difficult due to the lack of infrastructure control and heightened accessibility.
A malicious insider can be anyone within the company who has information and is privy to the security protocols in place. The 4 main categories of insider threats boil down to sabotage, fraud, intellectual property theft, and espionage. However, these threats are not always “malicious” but can also be the result of negligent behaviors.
11. Non-person Identities
These days, the cyber threats we face are becoming even more advanced, sometimes even past our species. Non-person identities can refer to anything from virtual machines to serverless functions to compute. These bots can act intelligently and replaces user identities.
They can be exploited and serve as entryways into cloud networks if they are given excessive permissions to databases. Organizations should employ solutions that can identify these non-person identities and alert security teams if they begin to act suspiciously.
12. Oversaturation of Tools
With the growing need for cloud technologies, companies are quick to cover all bases when it comes to securing their cloud environment as much as possible. However, the adage of too many cooks spoiling the broth holds here as the overuse of multiple security systems on a network can sometimes in itself become a security risk. Your cloud infrastructure is meant to simplify your operations and its security should not complicate that.
An overwhelmed cloud security base can become too complex and difficult to maintain and monitor – allowing smaller incidents to slip through and cause damage to your network despite the excessive protection in place.
While the cloud is moving us into the future, it’s not difficult to see why people might be cautious before taking that next step.
Concerns When Using Enterprise Cloud
There are 4 main concerns that people still maintain when considering the shift to enterprise cloud computing:
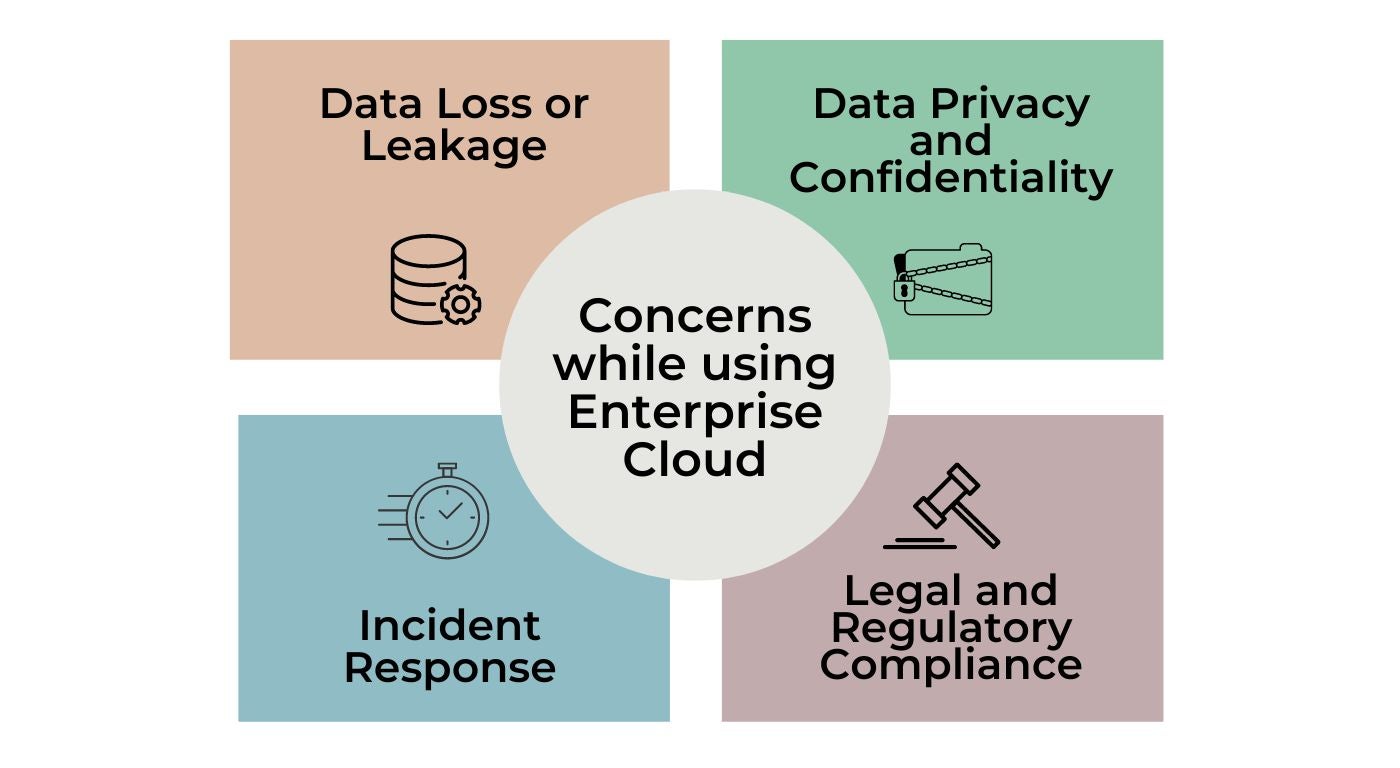
1. Data Loss or Leakage
While the cloud has made data so much more accessible and easier to store, the risk of breach has also significantly risen. Sensitive data files and system information are the main targets in a cyber-attack and access to either could easily capsize an entire organization.
Data breaches are easily the most prominent concern when considering an enterprise cloud service and the cloud platform you use should be able to mitigate those worries effectively.
2. Data Privacy and Confidentiality
The second most common concern would be data privacy. The cloud often comes across as an elusive concept – intangible and somehow keeping all our data safe somewhere far away. It’s a natural fear that the platforms we use might be able to access this data or it may somehow be exposed to the public in any way.
For most companies, the confidentiality of many users relies on cloud infrastructure, and a failure in these security measures could result in data breaches and sensitive information being leaked online or companies being held for ransom to gain back their client’s information. This has been proven in numerous cyber-attacks that targeted client information - from the Shangri-La Data Breach Incident to the Nikkei Group’s Singapore headquarters attack, both in May of this year.
3. Incident Response
InsuranceBee has revealed that 83% of small and medium-sized businesses are not financially prepared to recover from a cyber-attack, while 91% of small businesses have not purchased cyber liability insurance. Companies rely heavily on their incident response strategies to pull them through after the impact of a cyber-attack, but those resources are not always easily accessible – especially for smaller businesses that simply cannot afford most cloud security options available today.
Cloud infrastructure has inherently limited visibility and even those who do employ cybersecurity measures are still concerned that they might not be able to do enough to mitigate the threat of cloud breach.
4. Legal and Regulatory Compliance
As with all things, rules and regulations apply to keep us safe. Data protection regulations - like those from the PCI DSS and HIPAA - have set policies that require companies to limit access and regulation of sensitive information that may be used against individuals. These include credit card details, healthcare records, and many more.
With cloud adoption, the enforcement of these regulations has become a slight issue with the limited amount of visibility and control organizations retain over this information. Evidence of these limitations can be seen in the growing number of cyber-attacks in healthcare sectors in the past few years.
Regulations concerning cloud-based data also touch on the location of data files. This means that data that is held in servers outside of your country will be liable to the laws of that country and their accessibility regulations.
While the cloud has forever changed the way we operate and connect, it holds its risks. Cloud computing is an advanced technology that requires an innovative security system in place to work effectively. Sangfor Technologies provides all that and so much more.
Sangfor’s Cloud and Security Solutions
Sangfor offers a cloud adoption framework that is focused on practical preparations, such as strategic alignment, avoiding common mistakes, minimizing vendor lock-in, and identifying cost issues. These advanced cloud infrastructure solutions include:
- The Sangfor Hyper-Converged Infrastructure (HCI) is an innovative 3rd generation platform that converges computing, storage, networking, and security on a single software stack - providing a simplified 1-stop software-defined data center solution tailored for business-critical applications.
- Sangfor’s Cloud Platform is a reliable and seamless automated cloud computing platform that reduces the complexity of cloud data center construction and management through standardized and process-oriented functioning.
- Managed Cloud Service provides a globally distributed data center with the convenience and flexibility of a public cloud, with the security, control, and professional service of a private cloud.
- Sangfor Hybrid Cloud is an end-to-end cloud solution powered by Next Generation Converged Digital Infrastructure (NG-CDI) and enables flexibility in the application partition or workload placement design to optimize cloud adoption value.
- Sangfor’s Disaster Recovery Management (DRM) offers a comprehensive disaster recovery solution between Sangfor HCI and MCS which includes an active-passive disaster recovery solution and an active-active stretched cluster solution to protect business continuity on demand.
Sangfor provides all the ease and convenience of an innovative cloud platform combined with the highest levels of security for your data with advanced security features and SD-WAN capabilities.
Striving to provide pioneering and versatile cybersecurity solutions for your company to ensure the protection of your cloud computing platform, Sangfor offers a list of innovative products and services including:
- Anti-Ransomware: Sangfor NGAF (next generation firewall), Sangfor Endpoint Secure, Sangfor IAG (Secure web gateway), and Sangfor Cyber Command (NDR) integrate as part of Sangfor’s Anti-Ransomware solution. With security deployed at the perimeter, endpoint, and network, Sangfor’s Anti-Ransomware is a holistic solution that breaks every step of the ransomware kill chain.
- XDDR: Sangfor XDDR - Extended Detection Defense and Response is a framework that goes beyond traditional XDR by implementing a real integrated security solution, providing a holistic response to malware infections and APT breaches across the entire organization’s network, with ease of management, operation, and maintenance.
- Incident Response: Sangfor’s Incident Response service is geared towards flexible, fast, and effective elimination and prevention of cyber-attacks. The focus of incident response is locating and eradicating threats while implementing active disaster recovery and providing tailored analysis to help safeguard your company from future cyber-attacks.
Sangfor strives to provide intelligent and advanced cloud computing solutions combined with cybersecurity measures to improve protection and enhance the integrity of your IT infrastructure.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.





