Advances in technology have opened up the world to a barrage of new and improved threats. One of the leading culprits in the modern age has been the rapid increase of ransomware attacks. While cyber-attacks are mostly destructive in nature, ransomware attacks have been found to have ripple-effect repercussions across multiple industries. We look at a brief overview of the latest ransomware attacks in 2022 that caught headline attention.

Ransomware is a form of malicious software that is used by threat actors to infiltrate a network. The process involves encrypting data found and withholding a decryption key until a certain ransom amount is paid to the hackers. The digital age has made it much more convenient for ransomware groups to operate within the anonymity of the internet and make most ransom demands in the form of bitcoin to avoid being traced. Recent years have shown a drastically high rate of ransomware occurrences – 2022 has been no different in that regard.
Ransomware Attack Statistics for 2022
These are some sobering statistics about the state of ransomware attacks in the year 2022:
- There were a total of 236.1 million ransomware attacks worldwide during the first half of 2022 alone. (Statista)
- The number of ransomware attacks between the first and second quarters of 2022 saw an 18% increase – climbing from nearly 130 million incidents to approximately 106 million incidents worldwide. (Statista)
- 71% of companies worldwide were affected by ransomware in 2022 alone. (Statista)
- 62.9% of the victims of ransomware attacks paid the ransom. (Statista)
- Austria saw the highest rate of ransomware attacks with over 80% of organizations saying they experienced a ransomware attack last year. (Statista)
- 54% of respondents indicated that phishing scams were the most common cause of ransomware infection. (Statista)
- The Cybersecurity and Infrastructure Security Agency reported in February 2022 that it was aware of ransomware incidents against 14 of the 16 U.S. critical infrastructure sectors. (CISA)
These statistics may seem alarming and they should be, ransomware attacks have devastating effects on organizations and people’s lives. The fiscal implications of a ransomware attack are also not something that should be taken lightly.
The Average Cost of a Ransomware Attack in 2022
Many enterprises do not have the means to overcome a ransomware attack or even pay the ransom demanded and choose to simply close down. The financial consequences of a ransomware attack are enough to put any business owner’s hair on edge – and if it isn’t, you haven’t been paying attention.
Ransomware attackers have extorted at least $456.8 million from victims in 2022 according to chainalysis – a number which is surprisingly lower than the $765.6 million of the year before, however, this decrease is credited more to increasing unwillingness to pay ransomware attackers rather than a decline in the actual number of ransomware attacks.
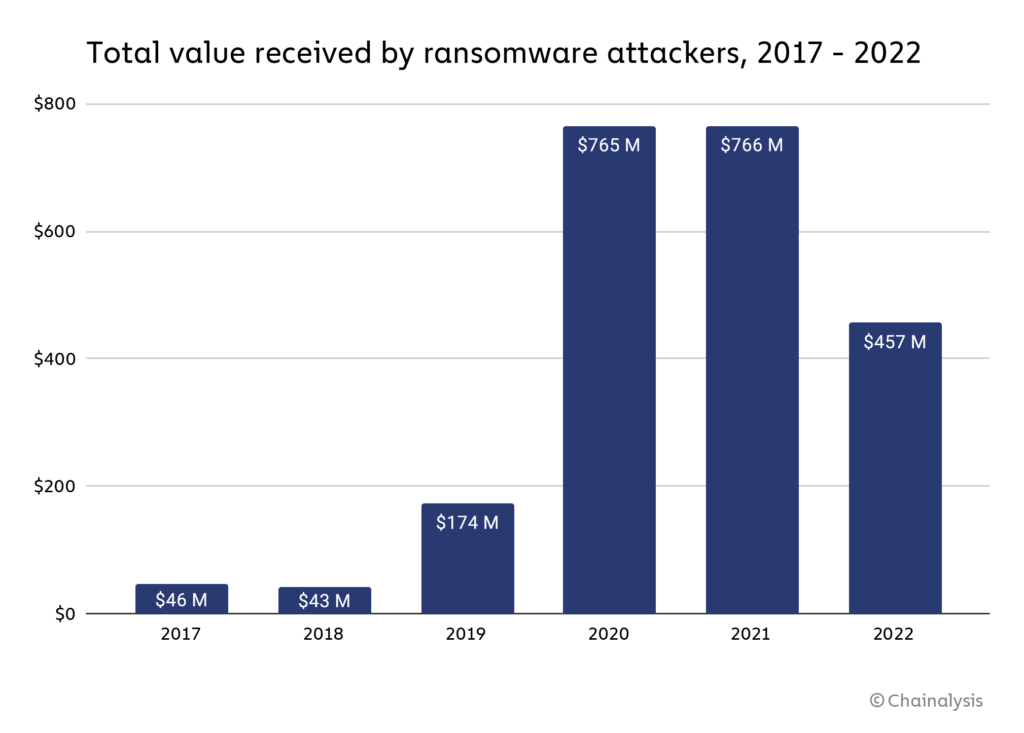
Source: https://blog.chainalysis.com/
The average cost of a ransomware attack in 2022 reported by IBM’s latest data breach report puts the number at $4.54 million – excluding the actual ransom itself.
Forbes has gone on to warn that we will be facing an estimated $10 trillion digital headache by the year 2025 if we continue to take a “business-as-usual approach to cybersecurity.” The publication continued to report that ransomware attacks have increased by 80% yearly with over 37 700 incidents happening every hour globally – reaching around 578 ransomware attacks each minute.
A list of Top Ransomware Attacks in 2022
Sangfor breaks down the details of comparing the costs of cybercrime and the expenses of improving your cybersecurity in this helpful article – highlighting the need for more enterprises to take a serious look at their security infrastructure to prevent cyber-attacks from happening. Now we can take a look at more specific top ransomware attacks that have occurred within the year 2022:
Nvidia Ransomware Attack 2022
Nvidia the largest semiconductor chip company, sure suffered. The California-based company confirmed that a threat actor had leaked employee credentials and proprietary information online. Once the infiltration was discovered, the organization engaged its cybersecurity framework however it later came out that employees had been using weak passwords that contained the company name.
A hacking group called Lapsus$ claimed responsibility for the attack and demanded a $1 million ransom and a percentage of an unspecified fee from Nvidia for access to 1TB of crucial company data. The group also has a history of using ransomware on other big companies - such as Impresa, Samsung, Microsoft, and T-Mobile.
Costa Rica Ransomware Attack 2022

Source: https://securityintelligence.com/
While most ransomware attacks tend to be about the financial benefits, there have been occasions where politics came into play. Such was the ransomware attack on the country of Costa Rica. The Conti Ransomware Attack pushed the small Central American country into a frenzy in April of 2022 when multiple cyber-attacks shut down its economy - affecting several branches of government and the general public.
Rodrigo Chaves was sworn in as president of Costa Rica on May 8th and on May 11th had to declare a state of emergency due to the attacks. CSO reported that he reallocated funds from the previous COVID-19 state of emergency under the assumption that this new declaration would ensure an efficient response, however, Costa Rica’s National Commission for Risk Prevention and Emergency Management (CNE) then made a public announcement that it had no strategy for handling this emergency just hours later.
After a few days, the notorious hacking group Conti took responsibility for the ransomware attack. The group has alleged ties to the Kremlin and has been heavily involved in the ongoing Ukrainian conflict.
Costa Rica has not yet recovered from the ransomware attacks and still suffers massive service disruptions and is struggling to contain this national crisis.
CHI Ransomware Attack 2022
CHI Health is a healthcare group subsidiary of CommonSpirit Health - the second-largest nonprofit hospital chain in the United States. In October of 2022, the hospital chain was hit by a ransomware attack that compromised patient data and affected daily operations. The group took immediate action to secure its infrastructure and try as best as it could to ensure continuity of care.
Some CHI Health employees and nurses have told 6 News that they’ve been “forced to go back to doing everything by hand, including charting patient information, which takes far longer.” According to JournalStar, Edward Porter - a diabetic living in Omaha - was unable to reorder sensors for his continuous glucose monitor due to the CHI Health's systems being offline. The implications of a cyber-attack on a healthcare organization can be lethal in most cases and causes severe and unnecessary discomfort to innocent patients.
LAUSD Ransomware Attack 2022
Hackers found a way to infiltrate LAUSD – the second-largest educational district in the United States with more than 1,000 schools and 600,000 students. The Los Angeles Unified School District – or LAUSD – came under the fire of a ransomware attack in September of last year that resulted in the release of data in what might be the biggest education breach in recent years.
A hacking group named Vice Society claimed the attack as their own and demanded an unspecified ransom amount from the schooling department for the stolen data. The attack disrupted computer systems and applications and eventually ended with the group publishing the stolen data to a dark web leak site. The data revealed contained confidential documentation, bank account details, and health information of students - including COVID-19 test data, previous conviction reports, and psychological assessments.
In an email to TechCrunch, the hacking group insisted that the CISA stalled the release of data and was “wrong” to advise LAUSD not to pay the ransom demand, stating that they “always delete documents” and “don’t talk about companies that paid us…now LAUSD has lost 500GB of files.”
In a report to the Los Angeles Times, Unified School District Superintendent Alberto Carvalho called the ransom demands "absurd" and "insulting” then reaffirmed in a tweet that “negotiating with cybercriminals attempting to extort education dollars from our kids, teachers, and staff will never be a justifiable option."
The educational system is already strained under the weight of underfunding and a lack of resources. Ransomware attacks within these industries have alarming ripple effects across the entire schooling system and call into question the ability of institutions to protect student information.
Hospital Ransomware Attacks 2022
As mentioned before, ransomware attacks on hospitals have life-threatening repercussions. This fact, however, does not impede cyber-attacks from being carried out on these facilities - most cyber-attacks against the healthcare industry are actually in the form of ransomware threats.
Texas Methodist McKinney Hosptial
In July of 2022, the Texas Methodist McKinney Hospital reported a breach in its systems in July of this year. A Russian hacking group called Karakurt claimed responsibility for the attack when they posted about acquiring 367 gigabytes of data from the hospital group on the dark web.
St. Charles Health System
Later on, in August, the St. Charles Health System overpaid 2 million dollars to 2,358 employees after the hospital was prevented from accessing timecard data for months due to a cyber-attack in December on the Ultimate Kronos Group –a company responsible for scheduling, timekeeping, payroll, and human resources data.
SickKids Hospital - an apology by LockBit Group
Source: https://www.cbc.ca/
NBCNews reported a new study that found the increase in cyber-attacks against healthcare facilities often leads to increased patient mortality rates. Some hacking groups even found a moral compass after leading a cyber-attack on a hospital - like the LockBit group which apologized after launching a ransomware attack on a sickkids children’s hospital. Unfortunately, healthcare industries are not always met with such forgiving decorum from cyber-criminals.
Healthcare Ransomware Attacks 2022
Sangfor discussed in a detailed article the ways that the healthcare industry suddenly became a huge target for cyber-criminals to exploit for ransoms due to the overwhelming need for care continuity and the severe lacking cybersecurity resources allocated within the industry.
A recent example can be seen when Practice Resources LLC notified 28 healthcare entity clients that 942,000 of their patients’ sensitive information was compromised in a ransomware attack in April of 2022. The New York-based management and billing vendor revealed in its incident report that hackers may have obtained names, home addresses, dates of treatment, and internal account numbers.
Sangfor Technologies believes that healthcare systems need to undergo a shift in cybersecurity and data management to combat this growing scourge of ransomware attacks.
Moving Forward With Sangfor Technologies
Due to its growing popularity, companies have become increasingly worried that they might be the latest target of a ransomware attack. According to the World Economic Forum in its Global Cybersecurity Outlook 2022 Insight Report, the USA has warned that 100 different strains of ransomware are now in circulation.
In the same report, Bruce Schneier says that we need to get ransomware under control. The Harvard University lecturer goes on to state that “ransomware is a crime well-optimized to the Internet age, we need defense [forces] to up their game as well.”
A 2022 survey revealed that nearly 60% of respondents stated that their organizations focused on preventing ransomware attacks rather than detecting and responding to them.
Sangfor Technologies is a world-class cybersecurity and cloud computing company that offers intensive and advanced Anti-Ransomware solution and state-of-the-art IT infrastructure. Offering numerous solutions that will protect your enterprise from ransomware and prevent ransomware from disrupting your new year. Ransomware detection and avoidance have never been simpler with this integrated solution that pieces together several advanced Sangfor products:
- Next-Generation Firewall - Sangfor’s ransomware solution uses an advanced Next Generation Firewall (NGFW) in conjunction with Endpoint Security to identify malicious files at both the network level and endpoints. The advanced firewall is a security device designed to inspect network and application traffic for threats, secure the network environment from intrusion, and bring in security intelligence from outside the network. Anything that the on-premises features cannot analyze is automatically sent to the cloud-based Neural-X sandbox for isolation and critical inspection.
- Cyber Command - The Sangfor Cyber Command monitors for malware, residual security events, and future potential compromises in your network and is coupled with an enhanced AI algorithm and threat intelligence – ensuring your data is always kept strictly protected and consistently monitored for lingering threats.
- Endpoint Secure - Lastly, Sangfor Endpoint Secure (Endpoint Detection and Response, EDR) solution is used to go beyond traditional antivirus and anti-malware software. Leveraging Sangfor’s proprietary Engine Zero AI-powered malware detection engine and Neural-X threat intelligence platform to deliver unrivaled malware protection at all endpoints. Endpoint Secure provides integrated protection against malware infections and APT breaches across your entire organization's network – all with ease of management, operation, and maintenance. The platform also received the AV-TEST “Top Product” award for achieving 100% ransomware protection against zero-day malware.
Sangfor has the only complete, holistic security solution to prevent and mitigate ransomware attacks in real time.
For more information on Sangfor’s cyber security and cloud computing solutions, visit www.sangfor.com.





